
umap Command in Linux
The umap command in Linux is a powerful utility for managing user mappings, particularly in the context of user namespaces. While not as commonly used as some other Linux commands, umap plays a crucial role in scenarios involving containerization, security contexts, and user ID mapping between different namespaces.
This tutorial will explore the umap command in detail, covering its purpose, syntax, available options, and practical examples with thorough explanations. By the end, you'll have a comprehensive understanding of how to use umap effectively in various system administration and security contexts.
Table of Contents
Here is a comprehensive guide to the options available with the umap command −
- Understanding the umap Command
- How to Use umap Command in Linux?
- Advanced Usage Examples
- Security Considerations
Understanding the umap Command
Before diving into the umap command itself, it's essential to understand the concept it operates within: User namespaces are a Linux kernel feature that allows for the isolation of user and group IDs. This means processes in different user namespaces can have different privileges, even when running as the same user ID.
User mapping is the process of translating user IDs (UIDs) and group IDs (GIDs) between different namespaces. The umap command helps manage these mappings.
Basic Syntax of umap
The general syntax for the umap command is −
umap [options] [command] [arguments]
How to Use umap Command in Linux?
The umap command offers several options and subcommands for managing user mappings −
Listing Current Mappings
umap list [options]
Options −
- -u or --user : List user ID mappings
- -g or --group : List group ID mappings
- -a or --all : List all mappings (both user and group)
- -n or --numeric : Display numeric IDs instead of names
- -p or --pid=PID : Show mappings for a specific process
Example −
umap list -a
Explanation − This command displays all current user and group ID mappings in the system. The output typically shows ranges of IDs mapped between different namespaces.
Creating New Mappings
umap create [options] outer inner count
Parameters −
- outer − The starting ID in the parent namespace
- inner − The starting ID in the user namespace
- count − The number of consecutive IDs to map
Options −
- -u or --user : Create user ID mapping
- -g or --group : Create group ID mapping
- -f or --file=FILE : Write mapping to a specific file
- -p or --pid=PID : Apply mapping to a specific process
Example −
umap create -u 1000 0 100

Explanation − This creates a user ID mapping where UIDs 0-99 in the user namespace correspond to UIDs 1000-1099 in the parent namespace. This is particularly useful for container scenarios where you want processes in the container to run as root (UID 0) while actually being mapped to an unprivileged user on the host.
Modifying Existing Mappings
umap modify [options] outer inner count
Options −
- Similar to the create subcommand
- --replace : Replace existing mappings instead of merging
Example −
umap modify -u 2000 0 50 --replace
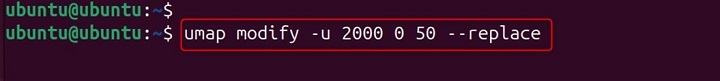
Explanation − This replaces the existing user ID mapping so that UIDs 0-49 in the user namespace now map to UIDs 2000-2049 in the parent namespace, removing any previous mappings for this range.
Deleting Mappings
umap delete [options] [outer|inner|all]
Options −
- -u or --user : Delete user ID mappings
- -g or --group : Delete group ID mappings
- -a or --all : Delete all mappings
- -p or --pid=PID : Delete mappings for a specific process
Example −
umap delete -u 1000-1099
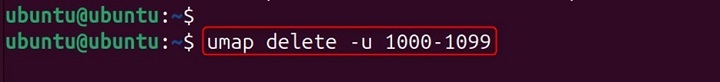
Explanation − This deletes the user ID mapping for the range 1000-1099 in the parent namespace. Any processes relying on this mapping will lose their translated UIDs.
Verifying Mappings
umap verify [options]
Options −
- -u or --user − Verify user ID mappings
- -g or --group − Verify group ID mappings
- -p or --pid=PID − Verify mappings for a specific process
Example −
umap verify -u -p 1234
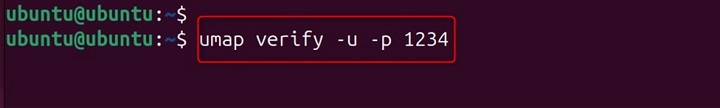
Explanation − This verifies that the user ID mappings for process with PID 1234 are correctly set up and functioning as intended.
Advanced Usage Examples
Setting Up a Container User Mapping
Create a new user namespace −
unshare -Ur
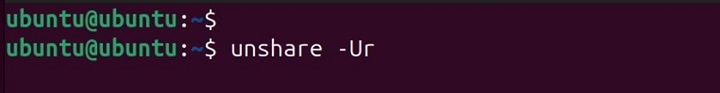
Inside the new namespace, set up mappings −
umap create -u 100000 0 65536 umap create -g 100000 0 65536
Explanation − This sequence creates a new user namespace and establishes mappings where UIDs/GIDs 0-65535 in the namespace correspond to UIDs/GIDs 100000-165535 on the host. This is a common setup for containers to have their own "root" user while using high-numbered IDs on the host system for security.
Nested User Namespaces
# First level namespace unshare -Ur umap create -u 10000 0 1000 # Second level namespace unshare -Ur umap create -u 0 0 1000
Explanation − This demonstrates nested user namespaces. The first namespace maps host UIDs 10000-10999 to namespace UIDs 0-999. The second namespace then maps these UIDs 0-999 to its own UIDs 0-999. A process running as UID 0 in the second namespace would actually be UID 10000 on the host.
Per-Process Mapping
# Start a process in a new user namespace unshare -Ur -- bash -c 'umap create -u 1000 0 100; some_application'
Explanation − This starts some_application in a new user namespace with a specific mapping where UIDs 0-99 in the namespace correspond to UIDs 1000-1099 on the host. The application can run with root privileges within its namespace while being confined to unprivileged host UIDs.
Security Considerations
When working with umap, several security aspects should be considered −
- Privilege Escalation Risks − Improper mappings could potentially allow privilege escalation. Always verify mappings carefully.
- Overlapping Ranges − Avoid overlapping mapping ranges as they can lead to unpredictable behavior.
- Persistent Mappings − Be cautious when making persistent mappings as they affect all future processes in the namespace.
- Default Deny − It's often safer to explicitly map only the IDs you need rather than mapping large ranges.
Best Practices
- Document Mappings − Maintain clear documentation of all user mappings in your system.
- Minimum Necessary − Only map the IDs you actually need for your application.
- Testing − Thoroughly test mappings in a development environment before production deployment.
- Monitoring − Implement monitoring to detect unauthorized mapping changes.
- Automation − For complex setups, consider automation tools to manage mappings consistently.
Conclusion
The umap command is a powerful tool for managing user ID and group ID mappings in Linux, particularly in the context of user namespaces. While its usage is more specialized than many common Linux commands, understanding umap is essential for system administrators and security professionals working with containers, sandboxing, or complex multi-user environments.
By mastering the options and examples provided in this guide, you'll be equipped to −
- Create secure user mappings for containerized applications
- Troubleshoot user namespace issues
- Implement sophisticated security models using ID mapping
- Manage complex multi-user systems with precision
Remember that with great power comes great responsibility-always exercise caution when modifying user mappings, as improper configurations can lead to security vulnerabilities or system instability.