
Reject Command in Linux
Linux provides several networking commands to control traffic, and one of them is the reject command. This command blocks network packets and sends a response back to the sender, letting them know their request was denied. In contrast, the drop command simply discards packets without any notification.
Using the reject command can be helpful when you want to be transparent about blocked requests, such as for troubleshooting or following network policies. It ensures that the sender isn't left guessing why their connection failed, making it a more informative way to manage network security.
Table of Contents
Here is a comprehensive guide to the options available with the Reject command −
- What is Reject Command in Linux?
- Syntax of Reject Command
- Reject Command Options
- How to Install Reject Command in Linux?
- How to Use Reject Command in Linux?
- Best Practices for Reject Command in Linux
What is Reject Command in Linux?
The reject command in Linux is often used in firewall rules, such as with iptables and nftables, to block network connections while sending an error response back to the sender. Unlike simply dropping packets, which leaves the sender waiting without any feedback, reject lets them know their request has been denied.
The reject command is useful for troubleshooting, security policies, or maintaining transparency in network management. It's commonly used in access control settings to manage which connections are allowed and which are blocked efficiently, helping administrators enforce security rules while ensuring proper communication with legitimate users.
Syntax of Reject Command
The basic syntax of reject when using iptables is shown below −
iptables -A INPUT -s <IP-ADDRESS> -j REJECT
Here, -A INPUT appends a rule to the INPUT chain, -s <IP-ADDRESS> specifies the source IP to reject, and -j REJECT sets the action to reject the packet.
Similarly, with nftables, the basic syntax for reject would be as follows −
nft add rule ip filter input ip saddr <IP-ADDRESS> reject
This nft command adds a rule to the filter table in the input chain for IPv4 traffic. It checks if the source IP address (ip saddr <IP-ADDRESS>) matches the specified <IP-ADDRESS>. If it does, the packet is rejected, sending an error response to the sender.
Reject Command Options
The reject command offers different types of rejection messages. We can use one of the following options to achieve a specific purpose −
| Option | Description |
|---|---|
| --reject-with icmp-port-unreachable | Sends an ICMP message indicating that the port is unreachable. |
| --reject-with icmp-host-unreachable | Indicates that the host is unreachable. |
| --reject-with icmp-net-unreachable | Notifies that the network is unreachable. |
| --reject-with tcp-reset | Sends a TCP RST (reset) packet for rejected TCP connections. |
How to Install Reject Command in Linux?
reject comes pre-installed into firewall tools like iptables and nftables, so itâs already available on most Linux distributions. However, if itâs missing, you can install the necessary packages using the distribution package manager −
iptables is a widely used firewall utility that manages network traffic rules. If itâs not installed, you can add it with the following commands depending on your distribution −
sudo apt install iptables # Debian/Ubuntu sudo yum install iptables # CentOS/RHEL sudo pacman -S iptables # Arch Linux
nftables is the modern replacement for iptables, providing more flexibility and efficiency in managing firewall rules. You can Install it using one of the following commands −
sudo apt install nftables # Debian/Ubuntu sudo yum install nftables # CentOS/RHEL sudo pacman -S nftables # Arch Linux
How to Use Reject Command in Linux?
Letâs use the following examples to understand how the reject utility works in Linux −
Rejecting Specific IP Addresses
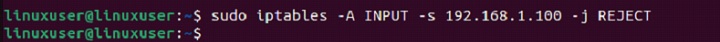
We can block a specific IP address and notify the sender by running the following command −
sudo iptables -A INPUT -s 192.168.1.100 -j REJECT
Rejecting TCP Connections with a Reset
For better handling of TCP-based connections, use the TCP reset option as follows −
sudo iptables -A INPUT -p tcp --dport 22 -j REJECT --reject-with tcp-reset
This command adds a rule to the iptables firewall to reject incoming TCP traffic on port 22 (used for SSH). It sends a TCP reset (RST) packet to the source, indicating the connection is rejected. The rule is appended to the INPUT chain.
Using Reject with nftables
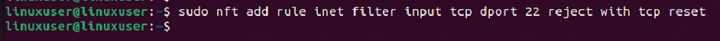
To reject packets using nftables, you can use the following command −
sudo nft add rule inet filter input tcp dport 22 reject with tcp reset
This command adds a rule to the nftables firewall configuration to reject incoming TCP traffic on port 22. It sends a TCP reset packet to the source, indicating the connection is rejected −
The rule is added to the input chain in the filter table under the inet family.
Best Practices for Reject Command in Linux
Hereâs how you can make your firewall rules more effective and easier to manage by using the reject command in Linux −
- Use REJECT instead of DROP when feedback is needed, as it sends a response to the sender (like a reset packet), which helps avoid connection timeouts and makes debugging easier.
- Instead of rejecting all traffic, apply rules to specific protocols like TCP, UDP, or ICMP for more precise control over your firewall.
- For faster connection handling, use tcp-reset when blocking services like SSH, as it terminates the connection quickly.
- Consider logging rejected packets before rejecting them, so you can monitor network activity and analyze it for security improvements.
Thatâs all about managing network traffic using the reject command in Linux.
Conclusion
The reject command in Linux offers a powerful way to manage network traffic while providing transparency to senders about blocked requests. Sending error responses back to the sender helps in troubleshooting and maintaining clear communication, which is essential for network management and security.
Whether using iptables or nftables, reject can be applied in various ways, such as rejecting specific IP addresses, resetting TCP connections, or using customized rejection messages.
You can follow practices such as using "reject" when feedback is needed and applying rules to specific protocols. By doing so, administrators can ensure more efficient and secure network configurations.