
ip6tables Command in Linux
The ip6tables command configures IPv6 packet filtering and Network Address Translation (NAT) for secure network management. It examines each packet's header containing IP addresses, ports, and protocol type and applies rules to control packet flow. NAT modifies IP address information in packet headers, allowing multiple devices on a private network to share one public IP when accessing external networks.
Table of Contents
Here is a comprehensive guide to the options available with the the Linux ip6tables command −
Syntax of ip6tables Command
The syntax of the ip6tables command is as follows −
ip6tables -t [table] [command] [chain] [options] -j [target]
In the above syntax [table] field is used to specify the filtering tables from filter, nat, mangle, and raw (default is filter). The [command] field is used to specify commands to append, delete, and insert rules, a list of commands is given below −
| Commands | Description | |
|---|---|---|
| -A | --append | Append a rule to a chain |
| -C | --check | Check if a rule exists in a chain |
| -D | --delete | Delete a matching rule or by rule number |
| -I | --insert | Insert a rule in a chain by position |
| -R | --replace | Replace a rule with a rule number |
| -L | --list | List rules in a chain or all chains |
| -S | --list-rules | Print rules in a chain or all chains |
| -F | --flush | Delete all rules in a chain or all chains |
| -Z | --zero | Reset counters in a chain |
| -N | --new | Create a new chain |
| -X | --delete-chain | Delete a user-defined chain |
| -P | --policy | Set the default policy for a chain |
| -E | --rename-chain | Rename the chain (old-chain - new-chain) |
[chain] − To specify the chain that needs to be manipulated from the selected table. A list of chains and their respective tables is given below −
| Chain | Description | Table |
|---|---|---|
| INPUT | Controls the incoming packets destined for the host system | This chain is in Filter, and Mangle tables |
| OUTPUT | Manages packets originating from the host and going out to the network | This chain is in all tables |
| FORWARD | Handles packets passing through the system (not destined for or originating from it) | This chain is in the Filter, Mangle, and Security tables |
| PREROUTING | Alters packets as soon as they come in, before any routing decisions | This chain is in nat, mangle, and raw tables |
| POSTROUTING | Alters packets right before they leave the system | This chain is in nat and mangle tables |
[options] − To specify the options listed in the following section.
[target] − To specify the rule target. The list of targets is given below −
| Target | Description |
|---|---|
| ACCEPT | Permits the packet to pass through the firewall |
| DROP | Discards the packet without notifying the sender |
| REJECT | Discards the packet and sends an error response to the sender |
| LOG | Logs the packet's information to a file |
| SNAT | Source Network Address Translation; modifies the packet's source address |
| DNAT | Destination Network Address Translation; modifies the packet's destination address |
| MASQUERADE | Changes the packet's source address for dynamically assigned IP addresses |
ip6tables Command Options
The options of the Linux ip6tables command are listed below −
| Flags | Options | Description |
|---|---|---|
| -p protocol | --protocol protocol | Specify protocol by name or number (tcp) |
| -s address/mask | --source address/mask | Specify source address with optional mask |
| -d address/mask | --destination address/mask | Specify destination address with optional mask |
| --dport port | --destination-port port | Specify the destination port number that the rule will apply to |
| -i name | --in-interface name | Input network interface |
| -j target | --jump target | Target action for the rule |
| -g chain | --goto chain | Jump to the chain without returning |
| -m match | --match match | Use extended match options |
| -n | --numeric | Display numeric output for addresses/ports |
| -o | --out-interface | Output network interface |
| -t | --table | Table to modify (default is filter) |
| -v | --verbose | Enable verbose mode |
| -w | --wait | Wait time to acquire the lock |
| --line-numbers | Show line numbers in the list output | |
| -x | --exact | Show exact counter values |
| -f | --fragment | Match second or further fragments |
| --modprobe=[command] | Command to insert modules | |
| -c pkt bytes | --set-counter pkt bytes | Set packet and byte counters |
| -V | --version | Display version information |
Examples of ip6tables Command in Linux
This section demonstrates the usage of the ip6tables command in Linux with examples −
Allowing Incoming SSH Traffic
To append a rule to the INPUT chain that allows incoming TCP packets directed to port 22 (SSH), use the ip6tables command in the following way −
sudo ip6tables -A INPUT -p tcp --dport 22 -j ACCEPT

The above command appends the rule to the filter table.
Note − The ip6tables command usually runs without displaying any output, but adding the -v or --verbose option can provide detailed information.
Allowing Incoming HTTP and HTTPS Traffic
To append a rule to the INPUT chain of the filter table that allows incoming HTTP and HTTPS traffic directed to port 80 (HTTP) and 443 (HTTPS), use the ACCEPT target −
sudo ip6tables -A INPUT -p tcp --dport 80 -j ACCEPT sudo ip6tables -A INPUT -p tcp --dport 443 -j ACCEPT
Blocking Traffic from a Specific IP
To block traffic from a specific IP, use the -s option with DROP as a target −
sudo ip6tables -A INPUT -s 2001:0db8:85a3:0000:0000:8a2e:0370:7334 -j DROP
Blocking All the Incoming Traffic
To block all the incoming traffic, use the following command −
sudo ip6tables -P INPUT DROP
The above command sets the default policy for the INPUT chain to DROP, blocking all incoming traffic.
Note that blocking all the incoming traffic also blocks remote SSH access. While blocking the incoming traffic, ensure SSH is allowed −
sudo ip6tables -A INPUT -p tcp --dport 22 -j ACCEPT
This configuration keeps the server secure while allowing remote access.
Allowing Ping (ICMPv6)
To allow ICMPv6 packets which is useful for ping and other network diagnostic tools, use the following command −
sudo ip6tables -A INPUT -p icmpv6 -j ACCEPT
Logging before Dropping Traffic
To log incoming traffic before dropping it, use the ip6tables command in the following way −
sudo ip6tables -A INPUT -j LOG --log-prefix "IP6Tables-Dropped: " sudo ip6tables -A INPUT -j DROP
Listing all the Rules
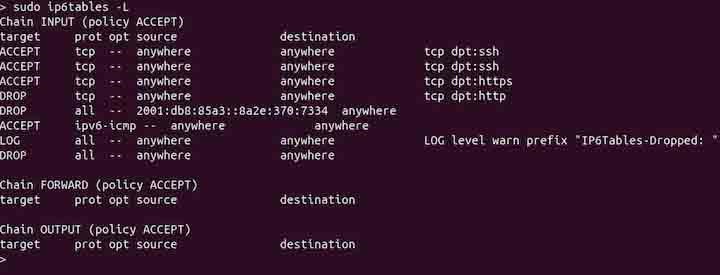
To list all the rules, use the -L option with the ip6tables command −
sudo ip6tables -L
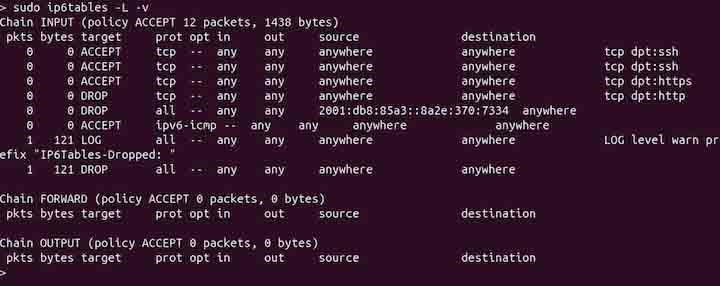
To list all the rules with verbose output, use the -v or --verbose option −
sudo ip6tables -L -v
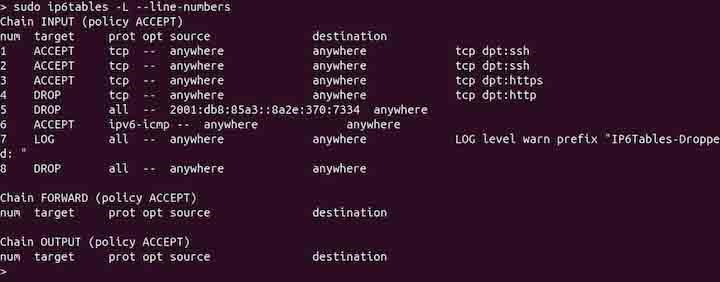
To list rules with line numbers, use the --line-numbers option −
sudo ip6tables -L --line-numbers
To list table-specific rules, use the -t option with the table name −
sudo ip6tables -t nat -L
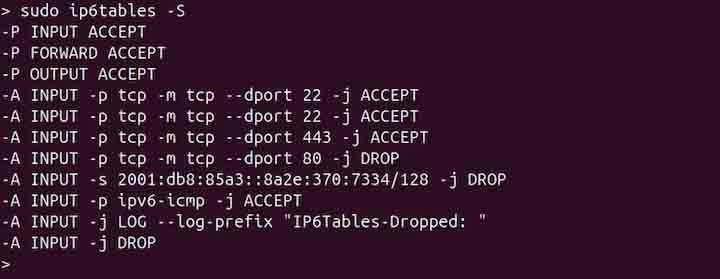
To list rules in a chain format, use the -S option −
sudo ip6tables -S
Flushing all the Rules
To delete all the rules, use the -F option −
sudo ip6tables -F -v

The above command flushes all rules in all chains, effectively resetting the ip6tables configuration to its default state. This can be useful when starting over with a clean slate for firewall rules.
Displaying Help
To display the help related to the command, use the -h or --help option with the command −
ip6tables -h
Conclusion
The ip6tables command is a handy tool for handling IPv6 packet filtering and Network Address Translation (NAT) on Linux systems. It enables administrators to manage the flow of network packets according to set rules, enhancing security and allowing devices on private IPv6 networks to utilize a shared public IP address. The command's syntax includes options to define filtering tables, commands for modifying rules, chains to route traffic, and targets that specify actions for each rule.
In this tutorial, we explained the ip6tables command, its syntax, options, and its usage in Linux through examples.