
openssl Command in Linux
The openssl command in Linux manages SSL/TLS cryptography. This toolkit implements the Secure Sockets Layer (SSL v2/v3) and Transport Layer Security (TLS v1) protocols and the cryptographic standards they rely on. Moreover, it provides access to OpenSSL's cryptographic functions, supporting private/public key management, X.509 certificate handling, message digests, encryption/decryption, SSL/TLS testing, S/MIME email handling, and time-stamp operations.
Table of Contents
Here is a comprehensive guide to the options available with the openssl command −
- Syntax of openssl Command
- OpenSSL Standard Commands
- OpenSSL Commands Options
- Examples of openssl Command in Linux
Syntax of openssl Command
The syntax of the openssl command is as follows −
openssl <command> [options]
In the above syntax, <command> is used to specify OpenSSL operations such as genpkey, req, enc, and others. The [options] field is used to specify options that modify the behavior or provide input parameters.
OpenSSL Standard Commands
Commonly used standard commands of openssl are listed below −
| Commands | Description |
|---|---|
| genpkey | Generate private keys |
| rsa | Manage RSA private keys (for example, conversion) |
| req | Generate Certificate Signing Requests (CSRs) or self-signed certificates |
| x509 | Manage X.509 certificates (for example, display or convert them) |
| dgst | Compute message digests (hash values) |
| enc | Encrypt or decrypt data using various ciphers |
| s_client | Test SSL/TLS client connections |
| ca | Perform Certificate Authority (CA) tasks, like signing CSRs |
| crl | Manage Certificate Revocation Lists (CRLs) |
| smime | Handle S/MIME encryption, decryption, and signing |
| rand | Generate random numbers or data |
| ts | Handle time-stamp requests and responses |
OpenSSL Commands Options
The options of openssl command are listed below −
| Command | Options | Description |
|---|---|---|
| genpkey | -algorithm <name> | Specify the algorithm such as RSA or EC |
| -out <file> | Output file for the private key | |
| rsa | -in <file> | Input private key file |
| -out <file> | Output file for the key | |
| -outform PEM/DER | Specify the output format | |
| -check | Validate the private key | |
| req | -new | Create a new CSR |
| -key <file> | Specify the private key file | |
| -out <file> | Output CSR file | |
| -x509 | Create a self-signed certificate | |
| x509 | -in <file> | Input certificate file |
| -out <file> | Output certificate file | |
| -text | Display certificate details | |
| -noout | Suppress output of encoded certificate | |
| dgst | -in <file> | Input file |
| -out <file> | Output file | |
| -aes-256-cbc | Specify encryption algorithm | |
| -salt | Add salt for ber encryption | |
| s_client | -connect <host:port> | Specify server address and port |
| -showcerts | Display server certificates | |
| -verify <depth> | Set certificate verification depth | |
| ca | -in <file> | Input CSR file |
| -out <file> | Output signed certificate | |
| -config <file> | Configuration file for CA settings | |
| crl | -in <file> | Input CRL file |
| -out <file> | Output CRL file | |
| -noout | Suppress output of encoded CRL | |
| -text | Display CRL details | |
| smime | -encrypt | Encrypt a message |
| -decrypt | Decrypt a message | |
| -sign | Sign a message | |
| -verify | Verify a signed message | |
| -in <file> | Input file | |
| -out <file> | Output file | |
| rand | -out <file> | Output file for random data |
| -base64 | Encode output in Base64 | |
| <size> | Specify the number of bytes to generate | |
| ts | -query | Generate a time-stamp request |
| -data <file> | Input data file | |
| -out <file> | Output file for the request | |
| -reply | Process a time-stamp response |
Examples of openssl Command in Linux
This section shows the usage of openssl command in Linux with examples −
Generating an RSA Private Key
To generate an RSA private key, use the command given below −
openssl genpkey -algorithm RSA -out myprivatekey.pem -pkeyopt rsa_keygen_bits:2048
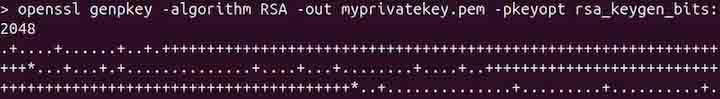
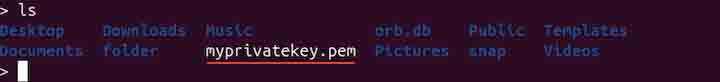
In the above command, genpkey is used to generate private keys. The -algorithm option specifies the algorithm to be used, which is RSA. The -out option specifies the output file for the generated key. The -pkeyopt option is used to define key generation parameters, such as rsa_keygen_bits, which determines the key size (2048 bits in this case). A private key will be generated in the current working directory as shown in the image below −
Generating a Private Key and a CSR
To generate a private key with CSR (Certificate Signing Request), use the following command −
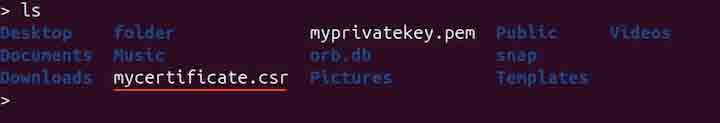
openssl req -new -newkey rsa:2048 -keyout myprivatekey.pem -out mycertificate.csr

During execution, the command will ask a few questions, such as the passphrase, country name, organization name, common name, and email as shown in the above image. A certificate will be generated in the current working directory.
Generating a Private Key and a Self-Signed Certificate
To generate a private key and self-signed certificate, use the following command −
openssl req -x509 -newkey rsa:2048 -keyout myprivatekey.pem -out mycertificate.crt -days 90
During execution, the command will ask a few questions, such as the country name, organization name, common name, and email. The validity is set to 90 days in the above command, if it is not specified then by default it is set to one month.
Note: A CSR is a request sent to a trusted authority to issue a certificate, while a self-signed certificate is created and trusted only by the person or organization that made it.
Verifying a CSR File
To verify a CSR, use the command given below −
openssl req -in mycertificate.csr -text -noout

The -in option is used to specify the input certificate file, -text is used to specify the output in human-readable form. The -noout option is used to prevent the openssl command from displaying encoded content.
Validating an RSA Private Key
To validate an RSA private key, use the command given below −
openssl rsa -in myprivatekey.pem -check

The -check option is used to validate the private key.
Converting a PEM to DER
To convert a PEM to DER, use the command given below −
openssl pkey -in myprivatekey.pem -outform DER -out myprivatekey.der
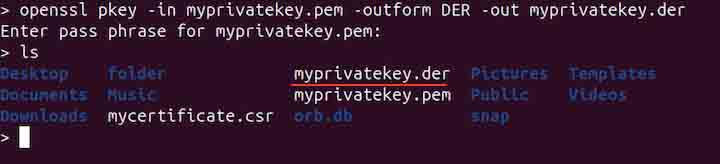
Note that the PEM is Base64 encoded, while DER is binary.
Generating a Public Key from a Private Key
To generate a public key from a private key, use the command given below −
openssl rsa -in myprivatekey.pem -pubout -out mypublickey.pem
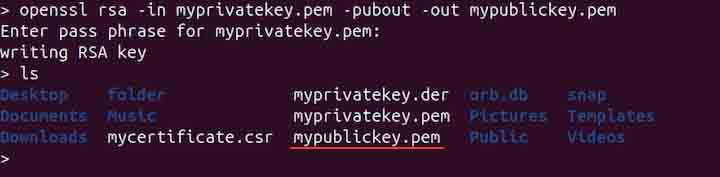
Generating a Random Password
To generate a random password, use the command given below −
openssl rand -base64 32
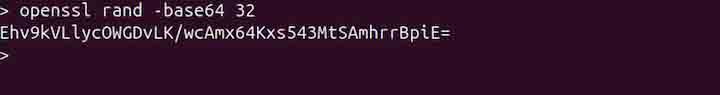
The above command will generate a 32-byte random password in base64.
Encrypting a File using a Public Key
To encrypt a file using a public key, use the openssl command in the following way −
openssl pkeyutl -encrypt -inkey mypublickey.pem -pubin -in textfile.txt -out encrypted.bin
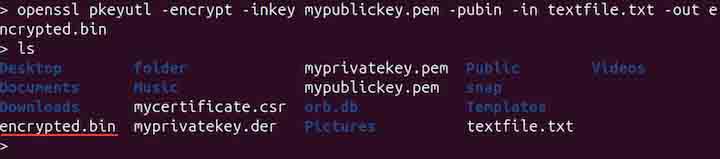
The above command uses the OpenSSL pkeyutl utility to encrypt data from textfile.txt using an RSA public key specified in mypublickey.pem. The -pubin flag indicates that the key is a public key, and the encrypted output is saved to encrypted.bin in binary format. Note that if the -pubin is not defined, then the command will assume the key is private.
Decrypt a File Using a Private Key
To decrypt a file using the private key, use the command given below −
openssl pkeyutl -decrypt -inkey myprivatekey.pem -in encrypted.bin -out decrypted.txt

The above command uses the OpenSSL pkeyutl utility to decrypt data from encrypted.bin using the RSA private key in myprivatekey.pem. The decrypted plaintext is saved to decrypted.txt.
Displaying Help
To display help related to the openssl standard, digest, and cipher commands, use the following command −
openssl -h
Conclusion
The openssl command in Linux is a versatile tool for managing SSL/TLS cryptography. It enables tasks such as private/public key management, certificate handling, message digest computation, encryption/decryption, SSL/TLS testing, S/MIME operations, and time-stamping.
From generating private keys, CSRs, and self-signed certificates to verifying keys, converting formats, and encrypting/decrypting data, OpenSSL is a handy tool for secure communications and cryptographic operations in Linux.