
ocsp Command in Linux
The ocsp command is part of OpenSSL that interacts with the Online Certificate Status Protocol (OCSP) responder. OCSP is a protocol used for checking the revocation status of an X.509 digital certificate. It allows querying a certificate authority (CA) in real time to confirm whether a certificate is still valid or has been revoked.
The ocsp command facilitates various OCSP-related tasks. It can generate and display requests and responses, create and send queries to an OCSP responder, and even function as a lightweight OCSP server.
Table of Contents
Here is a comprehensive guide to the options available with the ocsp command −
Syntax of ocsp Command
The syntax of the Linux ocsp command is as follows −
openssl ocsp -issuer <issuer_file> -cert <certificate_file> -url <responder_url> [options]
In the above syntax, the -issuer is used to specify the issuer's certificate file in PEM format. The -cert is used to specify the certificate file whose revocation status is being checked. The -url option is used to specify the URL of the OCSP responder to query for certificate status. The [options] field in the above syntax is used to specify various options listed in the next section.
ocsp Command Options
The options of the ocsp command are listed below −
| Option | Description |
|---|---|
| -out filename | Specifies the output file for the OCSP response. Default is the standard output |
| -issuer filename | Specifies the issuer's certificate, which must be in PEM format. This option must come before the -cert option |
| -cert filename | Specifies the certificate for which the status is being checked |
| -serial num | Specifies the certificate's serial number to check its status, as an integer |
| -signer filename | Specifies the signer certificate used to sign the OCSP request |
| -signkey filename | Specifies the private key for signing the OCSP request. If not present, the private key is read from the same file as the certificate |
| -sign_other filename | Specifies additional certificates to include in the signed request |
| -nonce | Adds an OCSP nonce extension to the request to prevent replay attacks |
| -no_nonce | Disables the OCSP nonce extension, if it was previously added |
| -req_text | Prints the textual representation of the OCSP request |
| -resp_text | Prints the textual representation of the OCSP response |
| -url responder_url | Specifies the URL of the OCSP responder to query for certificate status |
| -host hostname:port | Specifies the hostname and port for the OCSP request |
| -CAfile file | Specifies a file containing trusted CA certificates to verify the OCSP response signature |
| -verify_other file | Specifies additional certificates to use when locating the OCSP response signing certificate |
| -trust_other | Specifies that certificates in the -verify_other option should be trusted without additional checks |
| -noverify | Disables all verification of the OCSP response's signature and nonce values |
| -validity_period nsec | Specifies the range of time in seconds that will be tolerated for the OCSP response's validity period |
| -status_age age | Specifies the maximum age of certificate status information in the OCSP response |
| -md5|-sha1|-sha256 | Specifies the digest algorithm used for identifying certificates in the OCSP request |
| -index indexfile | Specifies a text index file with certificate revocation information for an OCSP responder |
| -CA file | Specifies the CA certificate corresponding to the revocation information in the index file |
| -rsigner file | Specifies the certificate used to sign OCSP responses |
| -rkey file | Specifies the private key to sign the OCSP response |
| -port portnum | Specifies the port on which the OCSP server listens for requests |
| -nrequest number | Specifies the number of OCSP requests the server will handle before exiting |
| -nmin minutes | Specifies the number of minutes when fresh revocation information is available |
| -ndays days | Specifies the number of days when fresh revocation information is available |
| -help | Displays help |
Examples of ocsp Command in Linux
The section shows the usage of the ocsp command in Linux with examples −
Checking the Status of a Certificate
To check the status of a certificate, use the command given below −
openssl ocsp -issuer issuer.pem -cert cert.pem -url http://ocsp.globalsign.com/
In the above command, the issuer.pem should be signed pem file by a Certification Authority (CA). The cert.pem is the file that needs to be checked. The -url option in the openssl ocsp command is important for sending an OCSP request to a specific OCSP responder to validate the status of a certificate. If the -url option is not specified, the command might attempt to fetch the OCSP responder URL from the certificate's Authority Information Access (AIA) extension, if it exists. However, not all certificates include this information.
For verification of both issuer.pem files use the following command −
openssl x509 -in issuer.pem -text -noout
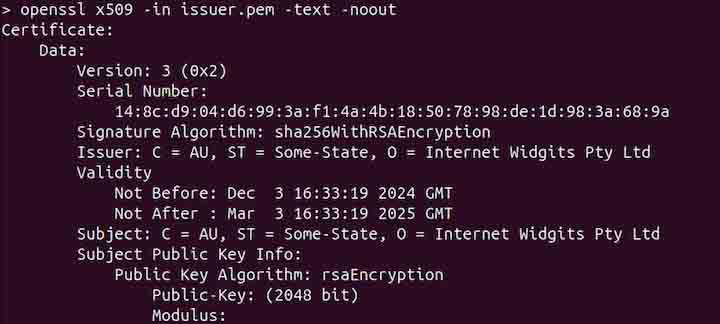
The above command will also display the AIA information.
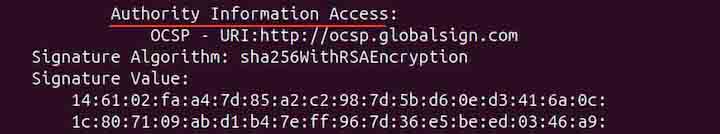
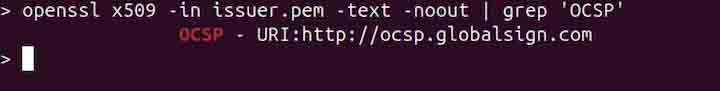
To find it, use the command given below −
openssl x509 -in issuer.pem -text -noout | grep 'OCSP'
To verify the certificate file, use the following command −
openssl x509 -in cert.pem -text -noout
If the files are incorrect, retrieve the proper files from the Certification Authority (CA).
Displaying the Response in Text Format
To display the responder's response in text format, use the -resp_text option −
openssl ocsp -issuer issuer.pem -cert cert.pem -url http://ocsp.globalsign.com/ -resp_text
Saving the Response to a File
To store the response to a file, use the -respout option with the file name −
openssl ocsp -issuer issuer.pem -cert cert.pem -url http://ocsp.globalsign.com/ -respout response.der
The above command will save the response in the der-coded file.
Displaying Help
To display help about the openssl ocsp command, use the -help option −
openssl ocsp -help
Conclusion
The ocsp command in OpenSSL is a useful tool for checking the revocation status of X.509 certificates using the Online Certificate Status Protocol (OCSP). It helps query certificate authorities in real time to verify whether a certificate is still valid or has been revoked.
The ocsp command offers various options, such as specifying certificate files, signing keys, and responder URLs, allowing users to check certificate status, display responses in text format, save responses to a file, and more.