
sshd Command in Linux
The sshd command belongs to the OpenSSH suite and is responsible for initiating the SSH server. It runs as a daemon, listening for incoming connection requests, handling the authentication, providing secure communication, and encrypting all data between client and server. The sshd command very much enables remote system access and secure communication over untrusted networks.
The main job of sshd is to work as an SSH server, facilitating secure and encrypted communications for remote access. sshd provides user privacy and data integrity in communications with different authentication mechanisms like password, key, and host authentication. sshd processes are critical to ensuring that there is a remote-accessible environment with great security.
Table of Contents
Here is a comprehensive guide to the options available with the sshd command −
Syntax of sshd Command
The basic syntax of the sshd command is as follows −
sshd [options]
Here, [options] indicate flags to customize the behavior of the SSH server.
sshd Command Options
Listed below are a few different options that can be used with the sshd command on Linux −
| Option | Description |
|---|---|
| -4 | Forces the sshd daemon to use only IPv4 addresses for listening to incoming connections. |
| -6 | Forces the sshd daemon to use only IPv6 addresses for incoming connection requests. |
| -b bits | Defines the size (in bits) of the ephemeral protocol version 1 server key. The default size is 1024 bits. |
| -C connection_spec | Sets specific connection parameters for extended test mode (-T). |
| -D | Prevents sshd from running as a background daemon. |
| -d | Activates debug mode, where sshd outputs detailed logs to the system log and does not fork into the background. |
| -e | Redirects sshd output to the standard error stream instead of the system log. |
| -f config_file | Specifies an alternate configuration file for sshd. If no configuration file is found, sshd will refuse to start. |
| -g login_grace_time | Sets the duration (in seconds) allowed for clients to authenticate. If the client fails within this time, the server disconnects. Default is 120 seconds. |
| -h host_key_file | Defines the specific file from which to read the host key. If not run as root, this option is required, as the default files are only accessible to the root user. |
| -i | Indicates that sshd is being run from the inetd service. While typically avoided due to key generation delays, smaller keys (e.g., 512 bits) might make this feasible. |
| -k key_gen_time | Sets the frequency (in seconds) for regenerating the ephemeral protocol version 1 server key. |
| -o option | Provides configuration options directly from the command line in the same format as those in the sshd_config file. |
| -p port | Specifies the port number for incoming connections. Multiple ports can be specified. Default is 22. |
| -q | Enables quiet mode to suppress logs for connection events, such as authentication or session termination. |
| -T | Runs sshd in extended test mode, validates the configuration file, and outputs the effective settings. |
| -t | Runs a basic test to validate the configuration file without starting the daemon. Checks for syntax errors and key sanity. |
| -u len | Defines the maximum length of the host name field in the utmp structure. |
Examples of sshd Command in Linux
Let's explore a few practical examples of the sshd command on Linux environment −
- Force SSH Server to Use IPv4 Connections Only
- Restrict SSH Server to IPv6 Connections
- Customize Ephemeral Key Size
- Redirect Logs to Standard Error
- Test Configuration with Specific Parameters
- Run sshd in Debug Mode
Force SSH Server to Use IPv4 Connections Only
When configuring an SSH server on a network where IPv6 is not supported or unreliable, you can ensure it uses only IPv4 for incoming connections.
sudo sshd -4
This command starts the sshd process while restricting it to listen only for IPv4 connections.
Restrict SSH Server to IPv6 Connections
In modern networks or environments that operate purely on IPv6, you can configure sshd to handle IPv6 traffic exclusively.
sudo sshd -6
This runs the sshd daemon, restricting it to process only IPv6 requests.
Customize Ephemeral Key Size
To enhance security for older systems using protocol version 1, adjust the size of the temporary keys generated by the SSH server.
sudo sshd -b 2048
Here, the -b 2048 option sets the size of the server key to 2048 bits instead of the default 1024 bits.
Redirect Logs to Standard Error
For situations where you donât want logs written to the system log (e.g., /var/log/auth.log), you can redirect them to the standard error stream.
sudo sshd -e
This command ensures that sshd sends all output directly to stderr instead of the default system log files.
Test Configuration with Specific Parameters
If you need to test your server configuration for a specific user, host, and IP address combination, you can specify those parameters explicitly.
sudo sshd -T -C user=admin,host=example.com,addr=192.168.X.X
This runs the SSH server in extended test mode (-T) and simulates a connection for the user admin coming from the IP 192.168.X.X to the host example.com.
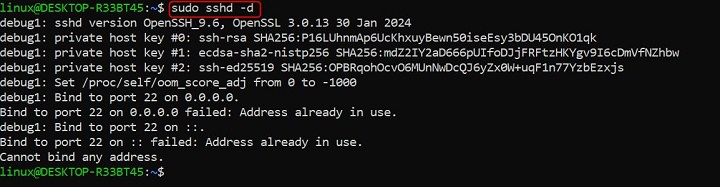
Run sshd in Debug Mode
When troubleshooting issues with the SSH server, such as failed connections or authentication problems, enabling debug mode provides detailed logging.
sudo sshd -d
This command starts the SSH server in debug mode, outputting verbose logs about its operations directly to the terminal.
Conclusion
The sshd command is a cornerstone of secure server management, offering administrators control over remote connections with extensive options for configuration and debugging. Its versatility allows you to tailor the SSH server to specific network environments, security policies, and use cases.
From forcing IPv4/IPv6 connections to reducing client grace time and validating configurations, mastering sshd ensures a robust and secure SSH environment.