
sechecker Command in Linux
Security-Enhanced Linux (SELinux) provides mandatory access control to secure Linux systems. However, managing and auditing SELinux policies can be complex. This is where sechecker comes in; it allows users to perform predefined modular checks on an SELinux policy.
The sechecker command helps in auditing, verifying, and modifying SELinux policy settings through profiles that group modules together for efficient analysis.
Table of Contents
Here is a comprehensive guide to the options available with the sechecker command −
- Understanding the sechecker Command
- Syntax of sechecker Command
- sechecker Command Options
- How to Install sechecker Command in Linux?
- How to Use sechecker Command in Linux?
- Best Practices to Use sechecker Command
Understanding the sechecker Command in Linux
sechecker is a tool designed to simplify SELinux policy verification. It works by applying predefined checks on a given policy to identify misconfigurations, enforce best practices, and provide insights into security settings. Profiles allow users to group multiple checks and adjust module settings as needed, making it a flexible tool for policy management.
Syntax of sechecker Command in Linux
The general syntax of sechecker command is shown below −
sechecker [-h] [--version] [-o OUTPUT_FILE] [-v] [--debug] config [policy]
sechecker Command Options
The sechecker command support several options that are described below −
| Option | Description |
|---|---|
| -o <path> | This option saves the results to a specified file instead of displaying them on the terminal (stdout). |
| -h, --help | Displays help information and exits. |
| --version | Prints the version number of sechecker and exits. |
| -v, --verbose | Enables detailed output, providing more information about each check. |
| --debug | Enables debugging mode, which helps in troubleshooting errors by providing detailed logs. |
When sechecker finishes running, it provides a return code that indicates the result of the checks. These codes are useful in scripting and automation.
| Return Code | Meaning |
|---|---|
| 0 | All checks passed. Everything is correctly configured. |
| 1 | One or more checks failed. Some security issues were found. |
| 2 | Error in the configuration file. The check configuration contains mistakes. |
| 3 | Other errors, such as policy open error â A system-related issue occurred, like not being able to open a security policy. |
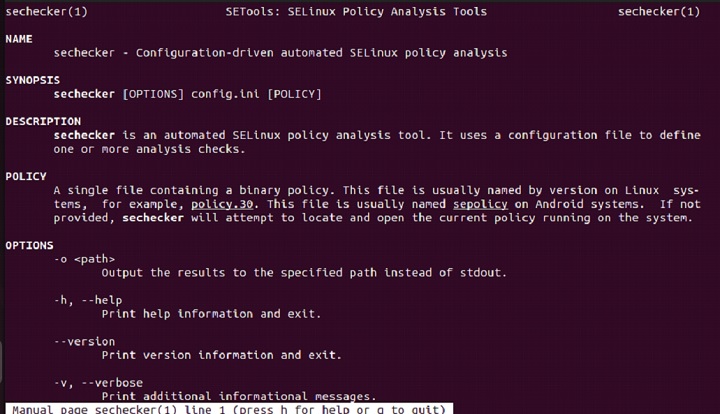
To learn more about secheck command, simply type the following command and hit enter −
man sechecker
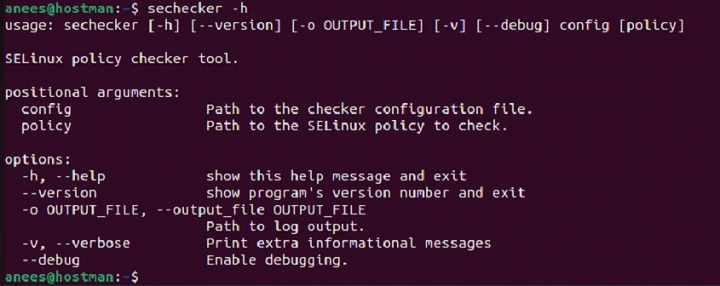
Or alternative, you can access the commandâs help page using -h option −
How to Install sechecker Command in Linux?
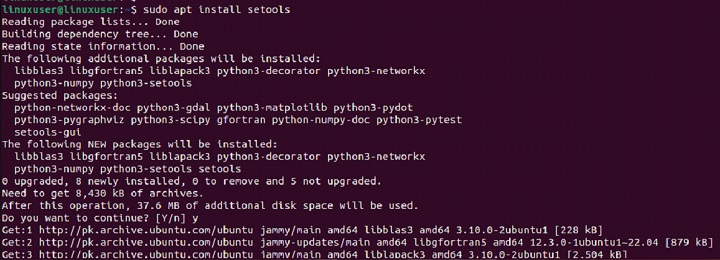
The sechecker command is part of the SETools suite, which provides tools for analyzing and managing SELinux policies. Tonstall sechecker, follow these steps based on your Linux distribution.
For example, Debian users can execute the following command to install sechecker on their systems −
sudo apt install setools
The sechecker command for Red Hat-based systems is available in setools-console package, which can be installed using yum or dnf −
#Installing sechecker on CentOS and RHEL sudo yum install setools-console #Installing sechecker on Fedora sudo dnf install setools-console
On Arch Linux, you can install setools, which includes sechecker, using the official repositories −
sudo pacman -S setools
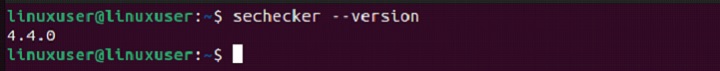
Once installed, check its version using the following command to verify the installation −
sechecker --version
How to Use sechecker Command in Linux?
Letâs go through the following examples to learn how the sechecker tool works in Linux −
- Save the Result to a Specified File
- Verbose Output
- Debugging Configuration Issues
- Checking for Unconfined Domains
- Checking for Read-Only Executables
Save the Result to a Specified File
Let's run the sechecker command with the -o option to save the output to a specified file −
sechecker -o /tmp/sechecker_results.txt my_config.conf
This command runs sechecker with the my_config.conf file and saves the results to /tmp/sechecker_results.txt using the -o option.
Verbose Output
Let's run the sechecker command with the -v option to enable verbose mode while specifying the required config file −
sechecker -v my_config.conf
This will display extra details about what the tool is checking.
Debugging Configuration Issues
The sechecker --debug command runs sechecker in debug mode, providing detailed logs useful for troubleshooting configuration issues −
sechecker --debug my_config.conf
This runs sechecker in debug mode using my_config.conf, helping identify and resolve configuration-related issues.
Checking for Unconfined Domains
In SELinux, an unconfined domain means it has minimal restrictions, making it a security risk. The following check verifies whether the domain_unconfined_type attribute is empty or missing. If found, it will alert the user −
[no_unconfined] check_type = empty_typeattr desc = Verify that the domain_unconfined_type attribute is missing or empty. attr = domain_unconfined_type missing_ok = True
This check ensures the domain_unconfined_type attribute is not empty, describes its purpose, and allows it to pass without error if missing. It shows the following output if domain_unconfined_type is missing or empty −
[WARNING] The domain_unconfined_type attribute is missing or empty.
However, if the attribute is properly defined, it returns the following output −
[OK] The domain_unconfined_type attribute is set.
Checking for Read-Only Executables
This check ensures that all executable files and libraries in SELinux are read-only. Executables should not be writable, as modifications could allow attackers to insert malicious code −
[ro_execs] check_type = empty_typeattr desc = Verify that all executables and libraries are read-only.
If writable executable types are found, the output would be −
[WARNING] Some executables or libraries are not read-only.
However, if all executables are correctly set to read-only, the output will looks like this −
[OK] All executables and libraries are read-only.
Best Practices to Use sechecker Command
Here are some best practices for using sechecker effectively −
- Group-related checks into profiles to streamline policy analysis and management.
- Use -v for detailed output, helping you understand each check's results.
- Use --debug to get detailed logs when diagnosing policy issues.
- Schedule periodic checks to ensure security settings remain intact.
- Save results using -o <file> to maintain logs for future reference.
- Ensure your config file is correctly structured to avoid errors.
- Identify and restrict unconfined domains to minimize security risks.
- Regularly validate that executables and libraries are non-writable.
- Integrate sechecker into scripts or cron jobs for continuous monitoring.
- Keep sechecker and SELinux policies up to date to leverage the latest security improvements.
Conclusion
The sechecker command simplifies SELinux policy verification by identifying misconfigurations, enforcing best practices, and providing insights into security settings. It allows users to group multiple checks into profiles, enabling efficient policy analysis and management.
With its flexible options, such as saving results to a file, enabling verbose output, and running in debug mode, sechecker is a valuable tool for security auditing. Moreover, understanding its return codes helps in automating security checks within scripts. Installation is straightforward across various Linux distributions, ensuring accessibility for system administrators.