
slogin Command in Linux
Secure Shell (SSH) is a cryptographic network protocol used to secure data communication over an unsecured network. The slogin command is an alias for ssh and provides the same functionality. It is primarily used to log into remote machines and execute commands remotely.
Table of Contents
Here is a comprehensive guide to the options available with the slogin command −
- Understanding the slogin Command
- Syntax of slogin Command
- Key Features and Options of slogin Command
- How to Use slogin Command in Linux?
- Examples of slogin Command in Linux
- Secure Shell (SSH) Protocol
- Practical Considerations
Understanding the slogin Command
The slogin (or ssh) command allows users to securely connect to a remote machine over a network. It encrypts the connection between the client and the server, ensuring that all data transmitted is secure and protected from eavesdropping and tampering. This command is widely used for secure remote administration, file transfers, and tunneling.
Syntax of slogin Command
The basic syntax for the slogin command is −
slogin [user@]hostname [command]
Here,
- user − The username to log in as on the remote machine. If omitted, the current username is used.
- hostname − The hostname or IP address of the remote machine.
- command − An optional command to execute on the remote machine.
Key Features and Options of slogin Command
The slogin command comes with a variety of options that provide flexibility and control over the SSH connection. Here are some of the key options −
- -p port − Specifies the port to connect to on the remote host. The default is 22.
- -i identity_file − Specifies the file containing the private key for public key authentication.
- -v, -vv, -vvv − Enable verbose mode, useful for debugging. Multiple vs increase the verbosity level.
- -L [bind_address:]port:host:hostport − Specifies local port forwarding.
- -R [bind_address:]port:host:hostport − Specifies remote port forwarding.
- -X, -Y − Enable X11 forwarding to run graphical applications on the remote machine and display them locally.
- -C − Enables compression of the data.
- -o option − Allows passing configuration options directly to the command.
How to Use slogin Command in Linux?
The slogin (or ssh) command is a versatile tool for securely logging into remote machines and executing commands over a network. It provides various options for specifying usernames, ports, identity files, and more.
By understanding the different options and use cases, you can effectively use slogin to manage remote connections and perform tasks on remote machines.
Examples of slogin Command in Linux
- Basic SSH Login
- SSH Login with a Specified Username
- Running a Command on the Remote Machine
- Connecting to a Remote Machine on a Different Port
- Using an Identity File for Authentication
- Enabling Verbose Mode
- Disabling Host Key Checking
- Enabling X11 Forwarding
- Using Local Port Forwarding
- Using Remote Port Forwarding
Basic SSH Login
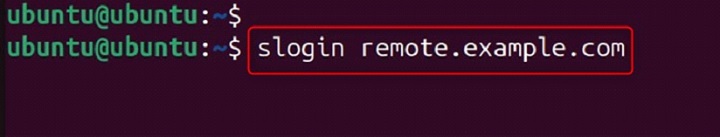
Log in to a remote machine with the hostname remote.example.com as the current user.
slogin remote.example.com
SSH Login with a Specified Username
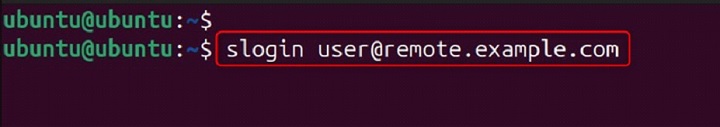
Log in to a remote machine with a specified username.
slogin user@remote.example.com
Running a Command on the Remote Machine
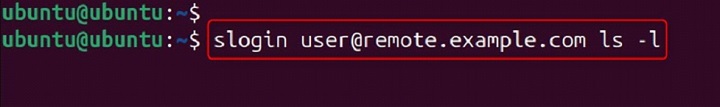
Run a command on the remote machine without logging in interactively.
slogin user@remote.example.com ls -l
Connecting to a Remote Machine on a Different Port
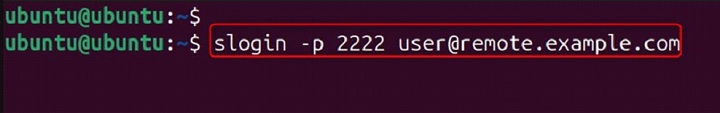
Connect to a remote machine using a different port.
slogin -p 2222 user@remote.example.com
Using an Identity File for Authentication
Specify an identity file (private key) for authentication.
slogin -i /path/to/private_key user@remote.example.com
Enabling Verbose Mode
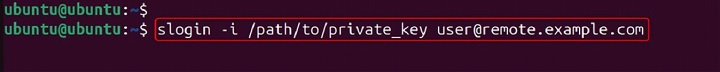
Enable verbose mode to see detailed information about the connection process.
slogin -v user@remote.example.com
Disabling Host Key Checking
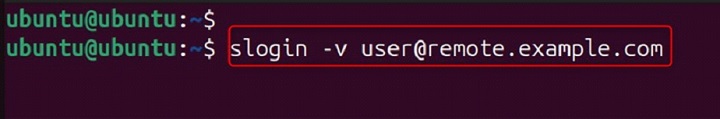
Disable host key checking (not recommended for production environments).
slogin -o StrictHostKeyChecking=no user@remote.example.com
Enabling X11 Forwarding
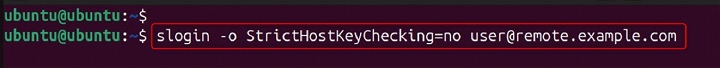
Enable X11 forwarding to run graphical applications on the remote machine and display them locally.
slogin -X user@remote.example.com
Using Local Port Forwarding
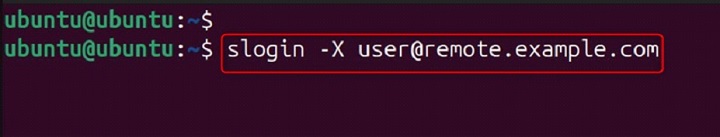
Forward a local port to a port on the remote machine.
slogin -L 8080:localhost:80 user@remote.example.com
Using Remote Port Forwarding
Forward a remote port to a port on the local machine.
slogin -R 8080:localhost:80 user@remote.example.com
Secure Shell (SSH) Protocol
SSH is a protocol used to securely log into remote machines and execute commands over a network. It provides encrypted communication between the client and server, ensuring that data transmitted is secure. SSH replaces older, insecure protocols like Telnet and rlogin.
Authentication Methods
SSH supports various authentication methods −
- Password Authentication − The user enters a password to log in.
- Key-Based Authentication − The user uses a private key to authenticate. This method is more secure than password authentication.
- Two-Factor Authentication − The user uses a combination of password and another authentication factor, such as a time-based one-time password (TOTP).
Configuration Files
- ~/.ssh/config − User-specific configuration file.
- /etc/ssh/ssh_config − System-wide configuration file.
- /etc/ssh/sshd_config − Configuration file for the SSH daemon (server).
Key Management
SSH keys are used for key-based authentication. They consist of a public key and a private key −
- Public Key − Placed on the remote machine in the ~/.ssh/authorized_keys file.
- Private Key − Kept on the local machine and used to authenticate.
Port Forwarding
SSH supports various types of port forwarding, which can be used to tunnel network traffic securely −
- Local Port Forwarding − Forwards a port on the local machine to a port on the remote machine. Example: slogin -L 8080:localhost:80 user@remote.example.com
- Remote Port Forwarding − Forwards a port on the remote machine to a port on the local machine. Example: slogin -R 8080:localhost:80 user@remote.example.com
- Dynamic Port Forwarding − Creates a SOCKS proxy that routes traffic through the SSH server. Example: slogin -D 1080 user@remote.example.com
X11 Forwarding
X11 forwarding allows you to run graphical applications on the remote machine and display them on your local machine. This is useful for administering remote servers that require graphical tools. To enable X11 forwarding, use the -X or -Y options. Example: slogin -X user@remote.example.com.
Compression
The -C option enables compression of the data being transmitted over the SSH connection. This can improve performance, especially on slow network connections. Example: slogin -C user@remote.example.com.
Practical Considerations
- Security − Always use strong, unique passwords and keys. Disable password authentication if possible and use key-based authentication.
- Firewall − Ensure that the SSH port (default: 22) is open on any firewalls between the client and server.
- Host Key Checking − SSH clients check the host key of the remote server to prevent man-in-the-middle attacks. Ensure that host key checking is enabled in production environments.
- Network Configuration − Ensure that both client and server network configurations allow for SSH traffic. This may include setting up Network Address Translation (NAT) or port forwarding on routers.
Conclusion
In summary, we explored various aspects of the slogin command, including its syntax, options, examples, and practical considerations.