
semanage Command in Linux
The semanage command is a powerful utility in the SELinux (Security-Enhanced Linux) toolset. It is used to manage SELinux policies and configurations, including setting file contexts, modifying port labels, managing user mappings, and more. In this comprehensive guide, we will explore the semanage command, its various options, and provide detailed examples to illustrate its usage.
Table of Contents
Here is a comprehensive guide to the options available with the patch command −
- Understanding semanage Command
- Key Options Used with semanage Command
- How to Use semanage Command in Linux?
- Troubleshooting Tips of semanage Command
Understanding semanage Command
This command is essential for administrators who need to maintain and modify SELinux security policies on their systems.
Basic Syntax
The basic syntax for the semanage command is as follows −
semanage [options]
The command can be executed with various options to perform different operations related to SELinux policy management.
Example −
semanage -h
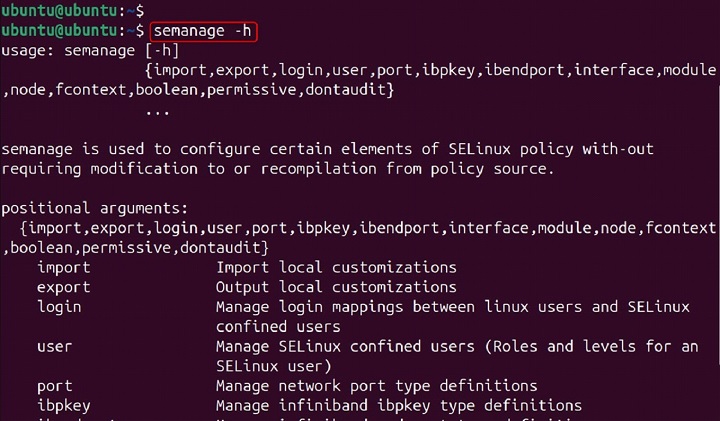
Key Options Used with semanage
Let's now understand the Key Options used with the semanage command −
semanage fcontext
The semanage fcontext command is used to manage file context rules in SELinux. It allows you to add, modify, delete, and list file context rules.
Example −
sudo semanage fcontext -a -t httpd_sys_content_t "/var/www/html(/.*)?"
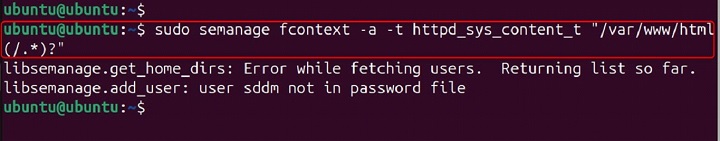
In this example, the semanage fcontext -a command adds a new file context rule. The -t httpd_sys_content_t option specifies the type httpd_sys_content_t. The "/var/www/html(/.*)?" argument specifies the path and regular expression for the files and directories to which this rule applies.
semanage port
The semanage port command is used to manage port labeling rules in SELinux. It allows you to add, modify, delete, and list port labels.
Example −
sudo semanage port -a -t http_port_t -p tcp 8080
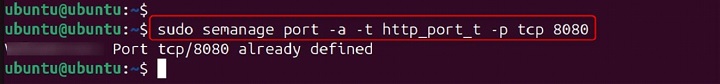
In this example, the semanage port -a command adds a new port label rule. The -t http_port_t option specifies the type http_port_t. The -p tcp option specifies the protocol tcp. The 8080 argument specifies the port number.
semanage user
The semanage user command is used to manage SELinux user mappings. It allows you to add, modify, delete, and list user mappings.
Example −
sudo semanage user -a -L s0-s0:c0.c1023 -R "staff_r sysadm_r" newuser_u
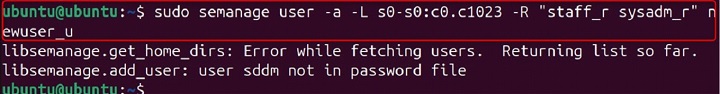
In this example, the semanage user -a command adds a new SELinux user mapping. The -L s0-s0:c0.c1023 option specifies the level range. The -R "staff_r sysadm_r" option specifies the roles. The newuser_u argument specifies the SELinux user.
semanage boolean
The semanage boolean command is used to manage SELinux booleans. It allows you to enable, disable, and list SELinux booleans.
Example −
sudo semanage boolean -m --on httpd_enable_homedirs
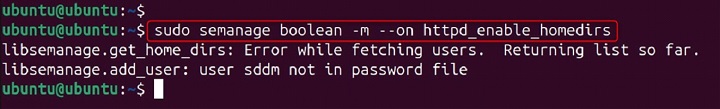
In this example, the semanage boolean -m command modifies an existing SELinux boolean. The --on option enables the boolean. The httpd_enable_homedirs argument specifies the boolean to be enabled.
semanage login
The semanage login command is used to manage SELinux login mappings. It allows you to add, modify, delete, and list login mappings.
Example −
semanage login -a -s user_u johndoe
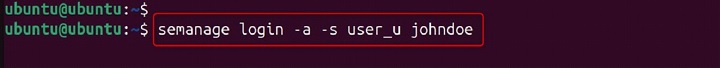
In this example, the semanage login -a command adds a new login mapping. The -s user_u option specifies the SELinux user user_u. The johndoe argument specifies the Linux user johndoe.
How to Use semanage Command in Linux?
Let's explore some practical examples to demonstrate the use of the semanage command in different scenarios.
Adding a File Context Rule
To add a new file context rule for a specific directory and its contents, use the semanage fcontext command.
Example −
sudo semanage fcontext -a -t httpd_sys_content_t "/var/www/html(/.*)?"
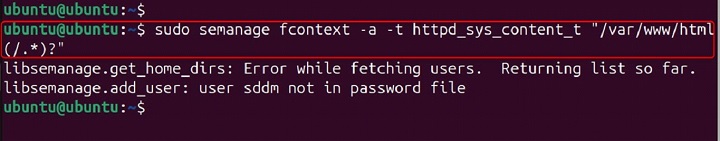
In this example, the semanage fcontext command adds a file context rule to assign the httpd_sys_content_t type to files and directories under /var/www/html.
Restoring Default File Contexts
After adding a file context rule, you need to apply the rule to the actual files and directories using the restorecon command.
Example −
restorecon -R /var/www/html
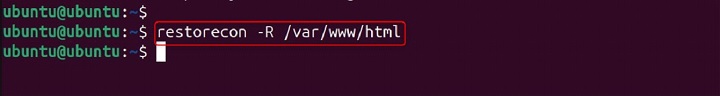
This restores the default SELinux security context for the /var/www/html directory and its contents based on the newly added file context rule.
Adding a Port Label Rule
To add a new port label rule for a specific port, use the semanage port command.
Example −
sudo semanage port -a -t http_port_t -p tcp 8080
In this example, the semanage port command adds a port label rule to assign the http_port_t type to port 8080 using the tcp protocol.
Modifying a User Mapping
To add a new SELinux user mapping for a specific Linux user, use the semanage user command.
Example −
sudo semanage user -a -L s0-s0:c0.c1023 -R "staff_r sysadm_r" newuser_u
In this example, the semanage user command adds a new SELinux user mapping for the SELinux user newuser_u with a level range of s0-s0:c0.c1023 and roles staff_r and sysadm_r.
Enabling an SELinux Boolean
To enable an SELinux boolean, use the semanage boolean command.
Example −
sudo semanage boolean -m --on httpd_enable_homedirs
In this example, the semanage boolean command enables the httpd_enable_homedirs boolean, allowing the HTTP daemon to serve content from users' home directories.
Automating SELinux Policy Management
You can create scripts to automate the process of managing SELinux policies and contexts.
Example Script −
#!/bin/bash # Add a file context rule semanage fcontext -a -t httpd_sys_content_t "/var/www/html(/.*)?" # Restore default SELinux context restorecon -R /var/www/html # Add a port label rule semanage port -a -t http_port_t -p tcp 8080 # Add a user mapping semanage user -a -L s0-s0:c0.c1023 -R "staff_r sysadm_r" newuser_u # Enable an SELinux boolean semanage boolean -m --on httpd_enable_homedirs
Save this script as manage_selinux_policies.sh and make it executable −
chmod +x manage_selinux_policies.sh
You can then run the script to automate SELinux policy management tasks −
./manage_selinux_policies.sh
Troubleshooting Tips of semanage Command
If you encounter issues while using the semanage command, consider the following troubleshooting tips −
Verify SELinux Status
Ensure that SELinux is enabled and check the current mode using the sestatus and getenforce commands.
Example −
getenforce
Check SELinux Logs
Check the SELinux logs for any error messages or warnings related to the semanage command and SELinux policies. The logs can provide valuable information for diagnosing and resolving issues.
Example −
tail -f /var/log/audit/audit.log
Review SELinux Policies
Review the SELinux policies to ensure that they are correctly configured and that the necessary permissions are granted.
Example −
sudo semanage fcontext -l
Conclusion
To effectively use the semanage command, it is important to understand the basic concepts of SELinux policies, including security contexts, types, roles, and booleans. For advanced users, the semanage command can be used in conjunction with other tools and scripts to automate SELinux policy management tasks and integrate with system administration processes.