
sestatus Command in Linux
The sestatus command in Linux is a vital tool for managing and monitoring SELinux (Security-Enhanced Linux) status and configurations. SELinux is a security module within the Linux kernel that provides a mechanism for supporting access control security policies. It is designed to enhance the security of the system by controlling how processes and users access files, devices, and other resources.
Table of Contents
Here is a comprehensive guide to the options available with the sestatus command −
- Understanding sestatus Command
- How to Use sestatus Command in Linux?
- Understanding SELinux Modes
- Changing SELinux Modes
- Viewing SELinux Contexts
- Managing SELinux Booleans
- Troubleshooting SELinux Issues
Understanding sestatus Command
The sestatus command provides detailed information about the current state of SELinux, including its mode, policy, and various status information.
Basic Syntax
The basic syntax for the sestatus command is as follows −
sestatus [options]
The command can be executed with or without options to display different levels of SELinux status information.
Key Information Provided by sestatus
The sestatus command provides several key pieces of information about the SELinux status −
- SELinux status − Indicates whether SELinux is enabled or disabled.
- SELinuxfs mount − Shows the mount point of the SELinux filesystem.
- Current mode − Displays the current mode of SELinux (enforcing, permissive, or disabled).
- Mode from config file − Displays the mode specified in the SELinux configuration file.
- Policy version − Shows the version of the SELinux policy in use.
- Policy from config file − Displays the SELinux policy specified in the configuration file.
How to Use sestatus Command in Linux?
The sestatus command in Linux provides a quick overview of the current SELinux (Security-Enhanced Linux) status.
Displaying Basic SELinux Status
To display the basic SELinux status information, simply execute the sestatus command without any options.
Example −
sestatus
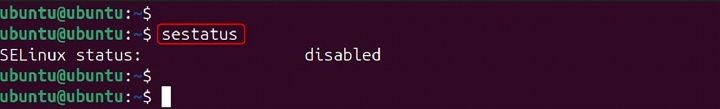
The output will display the current status of SELinux, including whether it is enabled or disabled, the current mode, and policy information.
Displaying Detailed SELinux Status
To display detailed SELinux status information, including additional context and file-related information, use the -v or --verbose option.
Example −
sestatus -v
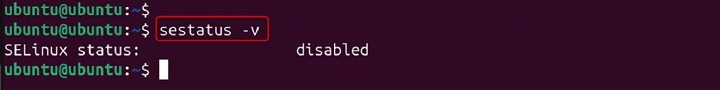
The output will provide more detailed information about the SELinux status, including the status of individual components and security contexts.
Understanding SELinux Modes
SELinux operates in three primary modes, each of which serves a different purpose −
Enforcing Mode
In enforcing mode, SELinux enforces its security policies and denies access to resources that do not comply with the policies. This is the default mode for a secure system.
Permissive Mode
In permissive mode, SELinux does not enforce its security policies. Instead, it logs policy violations for auditing and troubleshooting purposes. This mode is useful for diagnosing and resolving policy issues without affecting system functionality.
Disabled Mode
In disabled mode, SELinux is completely turned off, and no security policies are enforced or logged. This mode is not recommended for production systems as it leaves the system without the additional security provided by SELinux.
Changing SELinux Modes
To change the SELinux mode, you can use the setenforce command. This command allows you to switch between enforcing and permissive modes without rebooting the system.
Switching to Enforcing Mode
Example −
sudo setenforce 1

This command sets the SELinux mode to enforcing.
Switching to Permissive Mode
Example −
sudo setenforce 0

This command sets the SELinux mode to permissive.
To make the change permanent, you need to edit the SELinux configuration file (/etc/selinux/config) and set the SELINUX parameter to either enforcing, permissive, or disabled.
Example −
sudo nano /etc/selinux/config
Change the SELINUX parameter to the desired mode −
SELINUX=enforcing

Save the file and exit the editor.
Viewing SELinux Contexts
SELinux contexts provide detailed information about the security attributes of files, processes, and other resources. You can view the SELinux context of a file using the ls -Z command.
Example −
ls -Z /etc/passwd

The output shows the SELinux context of the /etc/passwd file, including the user, role, type, and level.
Managing SELinux Booleans
SELinux booleans are variables that allow you to modify the behavior of SELinux policies without requiring policy rebuilds. You can list, view, and modify SELinux booleans using the getsebool and setsebool commands.
Listing SELinux Booleans
Example −
getsebool -a

The output will display a list of all SELinux booleans and their current values.
Viewing a Specific Boolean
Example −
getsebool httpd_can_network_connect
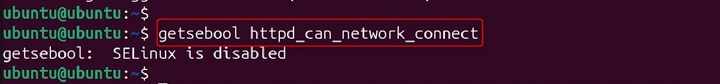
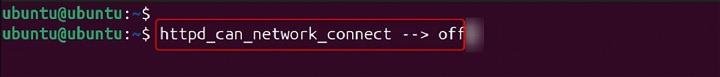
Output −
httpd_can_network_connect --> off
Modifying a Boolean
Example −
sudo setsebool httpd_can_network_connect on
This command sets the httpd_can_network_connect boolean to on, allowing the Apache web server to connect to the network.
To make the change permanent, use the -P option −
Example −
sudo setsebool -P httpd_can_network_connect on
Troubleshooting SELinux Issues
When encountering SELinux-related issues, the following steps can help diagnose and resolve the problems −
Checking SELinux Status
Ensure that SELinux is enabled and in the correct mode using the sestatus command.
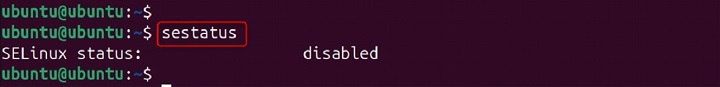
Example −
sestatus
Viewing Audit Logs
SELinux logs policy violations and other relevant information in the audit logs. You can view the audit logs using the ausearch or audit2allow commands.
Example −
ausearch -m avc -ts recent
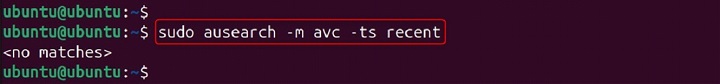
This command searches for Access Vector Cache (AVC) messages in the audit logs, showing recent policy violations.
Generating Policy Modules
If a legitimate access is denied by SELinux, you can generate a policy module to allow the access using the audit2allow command.
Example −
ausearch -m avc -ts recent | audit2allow -M mypolicy sudo semodule -i mypolicy.pp
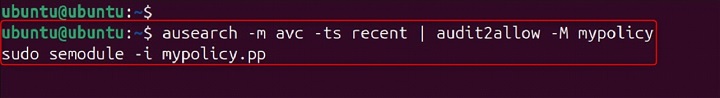
This series of commands generates a policy module named mypolicy based on recent AVC messages and installs the module.
Checking SELinux Status Before a System Upgrade
Before performing a system upgrade, it's important to check the SELinux status to ensure it is in the desired mode.
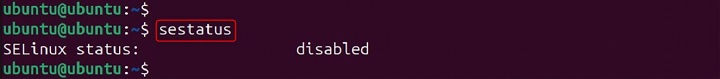
Example −
sestatus
Temporarily Disabling SELinux for Troubleshooting
When troubleshooting issues, you may need to temporarily switch SELinux to permissive mode to identify whether SELinux policies are causing the problem.
Example −
sudo setenforce 0

Viewing SELinux Contexts of Critical Files
To ensure critical system files have the correct SELinux contexts, use the ls -Z command.
Example −
ls -Z /etc/shadow

Modifying SELinux Booleans for Service Configuration
When configuring services, you may need to modify SELinux booleans to allow specific behaviors, such as enabling network connections for the Apache web server.
Example −
sudo setsebool -Phttpd_can_network_connect on
Generating Policy Modules for Custom Applications
For custom applications that require specific access permissions, generate and install SELinux policy modules based on audit logs.
Example −
ausearch -m avc -ts recent | audit2allow -M customapp sudo semodule -i customapp.pp
Conclusion
The sestatus command in Linux displays information such as whether SELinux is enabled or disabled, the current mode (enforcing, permissive, or disabled), the SELinux policy being used, and other relevant details. Essentially, it's a tool to check the operational state of SELinux on your system, helping administrators understand how SELinux is actively securing the system.