
ausearch Command in Linux
ausearch is a command used in Linux to search through audit logs generated by the audit daemon (auditd). These logs contain records of various system events, such as user logins, file access, and system calls.
The ausearch command by default looks in the /var/log/audit/audit.log file. However, you can specify other files if needed. You can also filter the search results based on different criteria, such as event type, time range, userID, and more.
Table of Contents
Here is a comprehensive guide to the options available with the ausearch command −
Syntax of ausearch Command
The basic syntax to use the ausearch command in Linux is provided below −
ausearch [options]
Where −
- ausearch invokes the command.
- [options] specifies different types of flags that can be used to alter the commands behavior.
Options ausearch Command
The ausearch command offers a variety of options to help you filter and search through audit logs effectively. Here are some of the key options −
| Option | Description |
|---|---|
| -a, --event [event ID] | Search for events with a specific audit event ID. |
| --arch [CPU] | Search for events based on the CPU architecture. |
| -c, --comm [Comm Name] | Search for events based on the command-line name. |
| -f [file name] | Search for events related to a specific file. |
| -g [group ID] | Filter events related to a specific group ID. |
| -hn [hostname] | Filter events related to a specific hostname. |
| -i | Interpret numeric values into human-readable text. |
| -if [file name] | Specify a different audit log file to search. |
| -k [key] | Look for events associated with a specific key. |
| -l | Display the list of available message types. |
| -m [message type] | Search for specific types of messages, such as USER_LOGIN or SYSCALL. |
| -n [number] | Limit the number of search results. |
| -p [process ID] | Search for events related to a specific process ID. |
| -r | Reverse the order of the search results. |
| -s [session ID] | Search for events with a specific session ID. |
| -sc [syscall] | Search for events related to a specific system call. |
| -se [success/failure] | Filter events based on success or failure. |
| -sv [syscall value] | Search for events with a specific system call value. |
| -ts [start time] -te [end time] | Search within a specific time range. |
| -ua [username] | Filter events related to a specific user. |
| -x [exit code] | Search for events with a specific exit code. |
In case you want to explore more options, you can open help section from the following command:
ausearch --help
Examples of ausearch Command in Linux
Lets consider the following examples of the ausearch command on a Linux system −
- Searching for All Login Events
- Finding Events Related to a Specific User
- Searching Within a Specific Time Range
- Finding Events Related to a Specific Process ID
- Finding Events Related to a Specific System Call
Searching for All Login Events
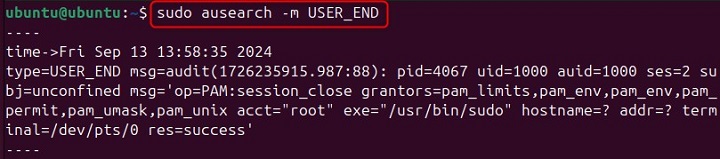
The ausearch command is commonly used to search for all login events. To do this, you can use the -m option with the USER_END message type. Heres how you can do it −
ausearch -m USER_END
This command will display all login events recorded in the audit logs.
Finding Events Related to a Specific User
If you want to find events related to a specific user, you can use the -ua option followed by the username. For example −
sudo ausearch -ua username
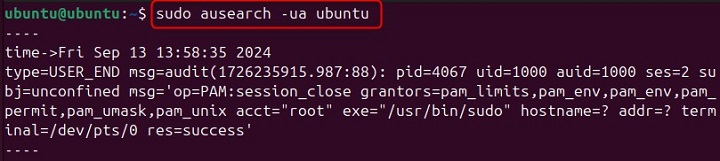
Make sure to replace username with the actual username you want to search for.
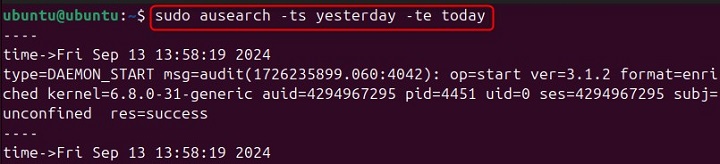
Searching Within a Specific Time Range
You can also search for events within a specific time range by using the -ts (start time) and -te (end time) options. Heres an example −
ausearch -ts yesterday -te today
When you run this command, it will display events that occurred between yesterday and today.
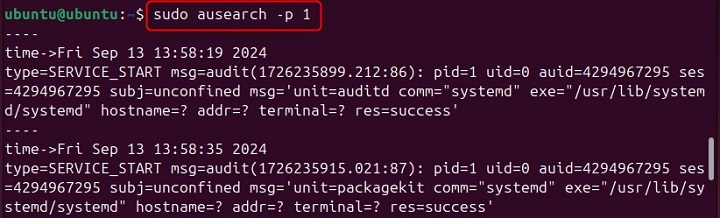
Finding Events Related to a Specific Process ID
To find events related to a specific process ID, you can use the -p option followed by the process ID. For example −
sudo ausearch -p 1
Replace 1 with the actual process ID you want to search for.
Finding Events Related to a Specific System Call
With the ausearch command, you can also search for events related to a specific system call. For this purpose, you must use the -sc option followed by the system call name. Heres an example −
sudo ausearch -sc open
Thats how you can use the ausearch command on your Linux system.
Conclusion
The ausearch command is a powerful utility used for searching through audit logs generated by the audit daemon in Linux. In this tutorial, we explored the syntax of the ausearch command along with its different options such as filtering by user ID, event type, and time range. Apart from that, we have also provided a few examples of the command to help you effectively utilize it to monitor and analyze system activities.