
ssh command in Linux
The ssh command is a core utility in the OpenSSH package that enables users to create secure and encrypted links to remote systems. It provides secure communication across possibly insecure networks and is extensively utilized for remote system administration, file transfer, and tunneling. With its b encryption, ssh offers a secure way to access and manage remote servers.
The primary purpose of the ssh command is to provide secure communication between systems. It does this by encrypting the data that flows between the server and the client, thereby disallowing interception or access by unauthorized parties. Through password-based or key-based authentication, ssh provides a dynamic solution for command execution and remote login.
Table of Contents
Here is a comprehensive guide to the options available with the ssh command −
- Syntax of the ssh Command
- Options Available for the ssh Command
- Configuration of ssh
- Files Used by ssh
- Examples of the ssh Command in Linux
Syntax of the ssh Command
The syntax for the ssh command is straightforward, which is as follows −
ssh [options] [user@hostname]
Here's what it entails −
- [options] − Flags to customize the behavior of the ssh command.
- [user@hostname] − Specifies the username and hostname of the remote machine you want to connect to.
Options Available for the ssh Command
The ssh command provides a variety of options to customize and control your SSH connections. Here are some commonly used options −
| Options | Description |
|---|---|
| -p port | Specifies the port number to connect to on the remote server. The default port for SSH is 22, but this option allows connection to servers configured to listen on a different port. |
| -i identity_file | Defines the private key file to use for authentication. |
| -l login_name | Specifies the username to log in as on the remote machine. |
| -L local_port:host:host_port | Enables local port forwarding, mapping a port on your local machine to a specified port on a remote server or host. |
| -R remote_port:host:host_port | Enables remote port forwarding, allowing connections from a port on the remote server to be forwarded to a specified port on a local machine or another host. |
| -C | Activates compression for data transfer, which is especially useful on slower networks, as it improves performance by reducing transmitted data. |
| -t | Allocates a pseudo-terminal for interactive command execution. |
| -X | Enables X11 forwarding to run GUI applications from the remote server and display them on your local machine. |
| -O option | Passes custom configuration options directly to the SSH command. |
| -v, -vv, -vvv | Enables verbose mode for debugging SSH connections. |
| -N | Does not execute any remote commands. |
Configuration of ssh
Configuring the ssh command involves editing the global client configuration file located at /etc/ssh/ssh_config. This file contains parameters that determine the behavior of ssh connections. Adjusting these configurations allows users to customize their SSH experience, optimize security, and enable additional features such as key-based authentication or host-based authentication.
Some commonly used parameters include −
- HostbasedAuthentication yes − Enables host-based authentication for seamless connectivity.
- Port 22 − Specifies the port to use for SSH connections.
- IdentityFile ~/.ssh/id_rsa − Points to the private key file for key-based authentication.
Files Used by ssh
Several files are crucial for the operation of the ssh command, particularly in the context of key-based authentication. These include −
- Private Key Files − Located in ~/.ssh/ (e.g., id_rsa, id_ecdsa), these are used to prove the identity of the user. They must be kept secure and accessible only to the owner.
- Public Key Files − Also found in ~/.ssh/ (e.g., id_rsa.pub, id_ecdsa.pub), these are shared with remote servers to establish trust.
Additionally, server-side files such as host keys (found in /etc/ssh/) play a critical role in verifying the server's authenticity during a connection.
Examples of the ssh Command in Linux
Letâs explore a few practical examples of the ssh command on Linux system −
- Connect to Remote Server
- Using a Custom Port
- Running a Command on a Remote Server
- Using SSH Keys for Authentication
- Debugging SSH Issues
- Port Forwarding with SSH
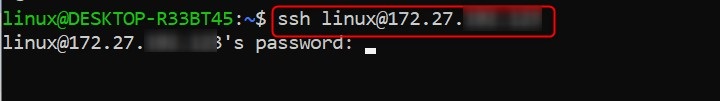
Connect to a Remote Server
Before starting, you must know the username and hostname of the remote server you want to connect to. The ssh command makes it easy to access the server securely by encrypting the communication.
ssh user@remote-server
This command initiates a connection to the remote server using the default port (22) and prompts for the password of the specified user. Once authenticated, you'll be logged into the remote machine.
Using a Custom Port
Some servers are configured to listen for SSH connections on ports other than the default (22), either for security reasons or organizational purposes. The -p option allows you to specify the custom port.
ssh -p 2222 user@remote-server
Here, you instruct the ssh client to connect using port 2222, ensuring compatibility with the server's settings.
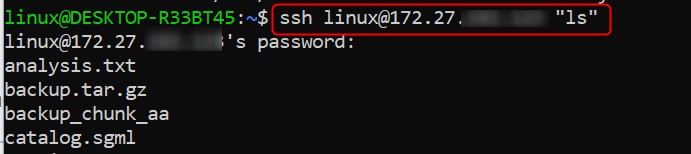
Running a Command on a Remote Server
You may not always need to log in interactively; sometimes you just want to execute a specific command on the remote server. The ssh command lets you do this by including the desired command in quotation marks.
ssh user@remote-server "ls"
This example retrieves a detailed list of files and directories within /var/www on the remote server and displays it directly in your local terminal.
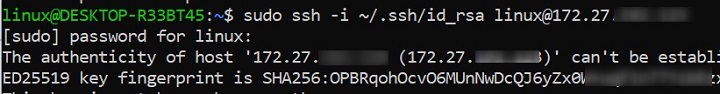
Using SSH Keys for Authentication
Authenticating with SSH keys is a secure alternative to passwords. If you have a private key stored locally and a public key on the remote server, ssh can use the keys for authentication.
ssh -i ~/.ssh/id_rsa user@remote-server
With this command, the -i option specifies the private key file to use for logging in. This approach is particularly useful for automated connections or frequent logins.
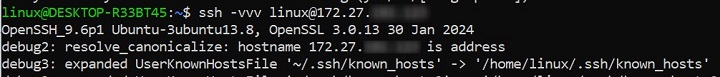
Debugging SSH Issues
If you're encountering problems with SSH connections, enabling verbose mode provides detailed output about the connection process. This can help identify configuration or authentication issues.
ssh -vvv user@remote-server
The -vvv option increases verbosity, providing step-by-step debugging information that can pinpoint the source of the issue.
Port Forwarding with SSH
Port forwarding allows you to securely access a service on a remote server by mapping it to a port on your local machine. This is often used for applications running on remote servers.
ssh -L 8080:localhost:80 user@remote-server
This example forwards traffic from your local machineâs port 8080 to the remote serverâs port 80, enabling access to the remote service as if it were hosted locally.
Conclusion
The ssh command is an essential utility for securely connecting and controlling remote servers in contemporary computing. It provides reliable encryption to maintain privacy and data integrity while communicating over potentially insecure networks.
Equipped with flexible features such as key-based authentication, port forwarding, and the capability to execute remote commands, the ssh command makes operations easier for system administrators, developers, and companies.
By controlling its options and setup, users are able to maximize security while improving efficiency. For secure, hassle-free remote access and control, the ssh command is still the foundation of solid SSH-based solutions.