
ssh-copy-id Command in Linux
The ssh-copy-id utility is a handy tool that copies your SSH public key to a remote host. This provides secure and passwordless authentication when you connect using SSH. ssh-copy-id streamlines the process of adding your public key to the remote host's ~/.ssh/authorized_keys file so that you don't have to do it yourself.
The main goal of ssh-copy-id is to automate and make SSH key-based authentication on remote hosts secure. It adds the proper key to the authorized_keys file without deleting or interfering with previously existing keys.
Table of Contents
Here is a comprehensive guide to the options available with the ssh-copy-id command −
Syntax of ssh-copy-id Command
The general syntax for the ssh-copy-id command is as follows −
ssh-copy-id [options] [user@hostname]
Where −
- [options] − Flags to customize the behavior of ssh-copy-id.
- [user@hostname] − The username and address of the remote server where the public key will be copied.
ssh-copy-id Command Options
Following is a list of various flags that can be used along with the ssh-agent command.
| Option | Description |
|---|---|
| -i identity_file | Lets you provide a specific SSH public key file to copy onto the remote server. |
| -f | Forcefully adds the key onto the remote server without determining whether it exists or not. |
| -n | Does a dry run to echo out the keys that would have been copied onto the remote server, but does not perform any operations. |
| -s | Uses SFTP mode to download, modify, and re-upload the authorized_keys file on the remote server instead of executing commands directly. |
| -t target_path | Specifies the path on the remote system where the keys should be added. Defaults to ~/.ssh/authorized_keys. |
| -p port, -o ssh_option | Passes the port (-p) or other SSH options (-o ssh_option) directly to the SSH command used internally by ssh-copy-id. |
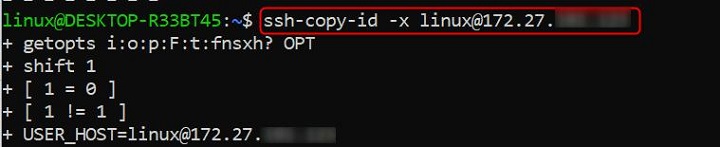
| -x | Enables debugging mode by setting the shell's -x flag, displaying the actual commands executed by the ssh-copy-id script. |
| -h, -? | Displays a summary of usage instructions and available options for the ssh-copy-id command. |
Examples of ssh-copy-id Command in Linux
Following are a few practical examples of ssh-copy-id command on Linux system −
- Copy a Specific Public Key File to a Remote Server
- Force Adding the Key Without Checking
- Perform a Dry Run
- Use SFTP Mode for Key Installation
- Specify a Custom Path for Keys
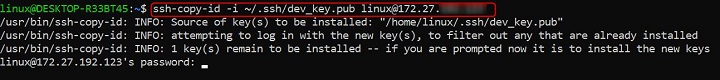
Copy a Specific Public Key File to a Remote Server
If you have more than one SSH key, you will probably copy a specific key rather than the default key.
ssh-copy-id -i ~/.ssh/my_key.pub user@X.X.X.X
This copies the my_key.pub file to the user's ~/.ssh/authorized_keys file on the remote server X.X.X.X.
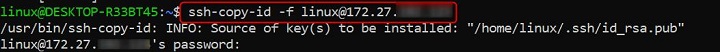
Force Adding the Key without Checking
When you are suspecting the key may already be present but still want to force it to be added, you can do so.
ssh-copy-id -f user@X.X.X.X
The key is added to the remote server's authorized_keys file without checking for duplicates, ensuring it is present.
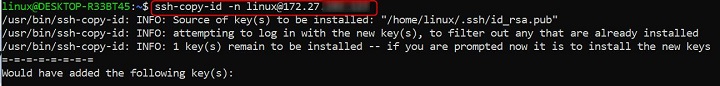
Perform a Dry Run
Before making changes, you can simulate the command to see what would happen without copying the key.
ssh-copy-id -n user@X.X.X.X
The command prints the public key(s) that would have been copied to the remote server but does not modify the authorized_keys file.
Use SFTP Mode for Key Installation
Some servers restrict command execution, requiring you to use SFTP mode instead.
ssh-copy-id -s user@X.X.X.X
The ~/.ssh/authorized_keys file is downloaded, modified locally, and then re-uploaded to the server using SFTP.
Specify a Custom Path for Keys
By default, keys are added to ~/.ssh/authorized_keys, but you can choose a different location.
ssh-copy-id -t ~/.ssh/custom_keys user@X.X.X.X
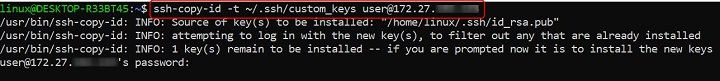
The key is added to the ~/.ssh/custom_keys file on the remote server instead of the default path.
Conclusion
The ssh-copy-id command is an essential tool for establishing SSH key-based authentication effectively and securely. Whether copying individual keys, debugging operations, or emulating changes, its versatility makes it a must-have for administrators and developers. By understanding these options, you can customize SSH key management to meet varied environments and workflows.