
iptables-restore Command in Linux
The iptables-restore command restores previously saved IP firewall rules. The rules are individual instructions that specify how to handle network packets that pass through a system. Each rule consists of conditions that define which packets it applies to and an action or target that defines what to do with those packets.
The iptables-restore and ip6tables-restore are used to restore IP and IPv6 tables from data provided through standard input (STDIN) or from a file. To read from a file, use the redirection operator, or specify the file directly as an argument.
Table of Contents
Here is a comprehensive guide to the options available with the iptables-restore command in Linux −
- Syntax of iptables-restore Command
- iptables-restore Command Options
- Examples of iptables-restore Command in Linux
Syntax of iptables-restore Command
The syntax of the Linux iptables-restore command is as follows −
iptables-restore [options] [file]
The [options] argument is used to specify various options that change the command's behavior. The [file] argument takes the rules file to restore.
Similarly, the syntax for restoring IPv6 rules is given below −
ip6tables-restore [options] [file]
iptables-restore Command Options
The options of the iptables-restore command are listed below −
| Flags | Options | Description |
|---|---|---|
| -c | --counter | To restore all packets and byte counters |
| -h | --help | To display help about the command |
| -n | --noflush | To avoid flushing content of previous table contents (default is flush) |
| -t | --test | To parse and construct the ruleset without committing |
| -v | --verbose | To get the detailed output |
| -V | --version | To display the command version |
| -w seconds | --wait=seconds | To wait for the xtables lock; optional seconds to limit wait time |
| -M modprobe | --modprobe=modprobe | To specify the path to the modprobe program (By default, iptables-restore will inspect /proc/sys/kernel/modprobe to determine the executable's path) |
| -T name | --table name | To Restore only the specified table, ignoring others in the input stream |
Examples of iptables-restore Command in Linux
This section demonstrates the usage of the iptables-restore command in Linux with examples −
Restoring Rules from the Existing Rules File
To restore the rules from the saved rules file, use the iptables-restore command in the following way −
sudo iptables-restore /usr/local/etc/iptables.rule
The output will generally not display any information if the command executes successfully, as iptables-restore typically runs silently without providing output for successful operations.
Similarly, to restore, IPv6 rules, use −
sudo ip6tables-restore /usr/local/etc/iptables.rule
Note that the iptables rules file can be saved anywhere on the system.
Testing Ruleset before Applying
To test the ruleset before applying, use the -t or --test option with iptables-restore command −
sudo iptables-restore -t /usr/local/etc/iptables.rule
Restoring Rules with Packets and Byte Counters
To restore IP tables while preserving the packet and byte counters, use the -c or --counter options −
sudo iptables-restore -c /usr/local/etc/iptables.rule
By using packet and byte counters, network administrators can gain insights into traffic patterns, optimize performance, and enforce security policies more effectively.
Restoring Rules without Flushing Previous Table Content
To restore the rules without flushing the previous table content, use the -n or --noflush option −
sudo iptables-restore -n /usr/local/etc/iptables.rule
Note that by default the iptables-restore command flushes the content of the table.
Restoring Rules while Waiting for the xtables Lock
The xtables lock is a mechanism used in Linux's netfilter framework which includes iptables, ip6tables, and nftables to prevent concurrent modifications of the firewall rules. When the iptables-restore or ip6tables-restore command is executed, it attempts to acquire the xtables lock. If the lock is available, the command proceeds with its operation.
Suppose the lock is unavailable (meaning another process is currently modifying the rules). In that case, the command can either terminate with an error or wait for the lock to be freed, depending on the specified -w or --wait option.
To wait indefinitely, use the -w or --wait option −
sudo iptables-restore -w /usr/local/etc/iptables.rule
To wait for 20 seconds only, use the 20 with the -w or --wait option −
sudo iptables-restore -w 20 /usr/local/etc/iptables.rule
Restoring Rules by Specifying the modprobe Program
The modprobe command is used with iptables-restore command to ensure that the necessary kernel modules are loaded before applying firewall rules.
By default, iptables-restore will inspect /proc/sys/kernel/modprobe to determine the executable's path. However, to specify a different location use the -M or --modprobe option −
sudo iptables-restore -M /usr/local/bin/modprobe /usr/local/etc/iptables.rule
Restoring Rules of a Specific Table
To restore only a specific table such as filter, nat, raw, mangle, or security use the -T or --table option −
sudo iptables-restore -T nat /usr/local/etc/iptables.rule
Restoring Rules with Verbose Output
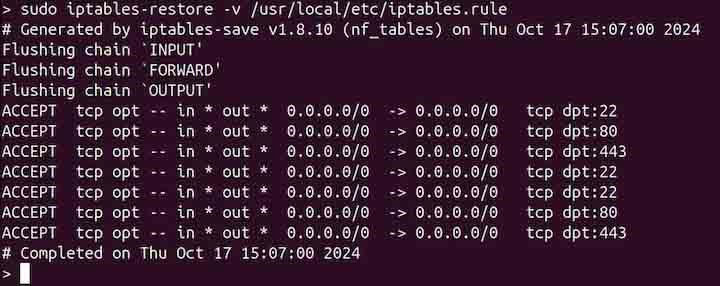
To display the verbose output while restoring rules, use the -v or --verbose option −
sudo iptables-restore -v /usr/local/etc/iptables.rule
Conclusion
The iptables-restore is a command-line tool for managing IP firewall rules in Linux. This command restores complex sets of rules quickly and efficiently, ensuring that network packet handling adheres to specified security policies.
Understanding the syntax and available options, such as preserving packet counters, testing rules before applying them, and specifying the modprobe program, allows for customized firewall configurations to meet specific needs. Additionally, utilizing the ip6tables-restore command facilitates similar management of IPv6 rules.