
svcgssd Command in Linux
The Linux svcgssd command is a crucial component of the RPCSEC_GSS security protocol, which provides authentication and security for Remote Procedure Call (RPC)-based services, particularly Network File System (NFS).
Table of Contents
Here is a comprehensive guide to the options available with the svcgssd command −
- Understanding the svcgssd Command
- How to Use svcgssd Command in Linux?
- Understanding RPCSEC_GSS and GSS-API
- Installing and Configuring svcgssd Command
- Syntax and Options of svcgssd Command
- Examples of svcgssd Command in Linux
- Troubleshooting for svcgssd Command Issues
- Security Considerations of svcgssd Command
Understanding the svcgssd Command
The rpc.svcgssd command in Linux is a server-side daemon that plays a crucial role in implementing the RPCSEC_GSS security protocol. This protocol is used to provide authentication and encryption for Remote Procedure Call (RPC) services, particularly in environments where Network File System (NFS) is deployed. The daemon facilitates secure communication between RPC clients and servers by handling the establishment of security contexts.
Before any RPC requests can be exchanged using RPCSEC_GSS, the client must first authenticate with the server, and rpc.svcgssd ensures that this process is managed efficiently. It interacts with the Linux kernel through the /proc filesystem, allowing it to communicate security credentials and maintain secure sessions
What is svcgssd Command?
The svcgssd daemon is responsible for handling server-side authentication for RPC-based services using the GSS-API (Generic Security Services Application Programming Interface). It ensures that NFS servers can authenticate clients securely using Kerberos or other GSS-based authentication mechanisms.
Why is svcgssd Command Important?
- Provides Secure Authentication: Ensures that only authorized clients can access NFS shares.
- Supports Kerberos Authentication: Works with Kerberos 5 to provide b security.
- Handles Security Contexts: Establishes and maintains authentication sessions between clients and servers.
- Integrates with NFS: Works alongside rpc.gssd to secure NFS mounts.
How to Use svcgssd Command in Linux?
The rpc.svcgssd daemon supports various options that allow users to customize its behavior. For instance, running the command with the -f flag forces it to operate in the foreground, sending output directly to stderr instead of logging it via syslogd. The -v option increases verbosity, providing detailed debugging information, and can be specified multiple times to further enhance logging.
Additionally, the -r flag increases the verbosity of the RPCSEC_GSS library, while the -i flag does the same for the NFS ID mapping library. Users can also specify a principal using the -p option, which overrides the default nfs/FQDN@REALM credential. These options provide administrators with flexibility in configuring the daemon to suit their security and debugging needs
Understanding RPCSEC_GSS and GSS-API
Configuration for rpc.svcgssd can be managed through the /etc/nfs.conf file, where users can define parameters such as principal names, verbosity levels, and debugging settings. The [svcgssd] section of this file allows administrators to set values equivalent to command-line options, ensuring consistent behavior across system reboots.
For example, setting verbosity=2 in the configuration file is equivalent to using -v on the command line. This approach simplifies management, especially in enterprise environments where standardized security configurations are necessary. By leveraging configuration files, administrators can maintain a secure and efficient RPCSEC_GSS setup without manually specifying options each time the daemon is started
What is RPCSEC_GSS?
RPCSEC_GSS is an extension of RPC that allows secure authentication and encryption using the GSS-API. It is commonly used in NFSv4 to provide b authentication and data integrity.
How Does GSS-API Work?
GSS-API provides a standardized interface for authentication mechanisms like Kerberos. It allows applications to −
- Establish secure sessions.
- Authenticate users and services.
- Encrypt and verify data integrity.
Installing and Configuring svcgssd Command
Installation − Most Linux distributions include svcgssd as part of the NFS utilities package. If missing, install it using −
For Debian-based systems −
sudo apt update && sudo apt install nfs-utils
For Red Hat-based systems −
sudo yum install nfs-utils
Configuration − The main configuration file for svcgssd is /etc/nfs.conf. Modify the [svcgssd] section to set authentication parameters.
[svcgssd] principal = nfs/server.example.com@EXAMPLE.COM verbosity = 2 rpc-verbosity = 2 idmap-verbosity = 2
Apply changes −
sudo systemctl restart nfs-server
Syntax and Options of svcgssd Command
The primary use case for rpc.svcgssd is in securing NFS communications, particularly when Kerberos authentication is required. NFS servers rely on this daemon to authenticate clients and establish encrypted sessions, preventing unauthorized access to shared files.
Without rpc.svcgssd, the kernel would be unable to process security contexts, leading to failed authentication attempts and potential security vulnerabilities. This daemon is essential for organizations that require b authentication mechanisms for their distributed file systems, ensuring that sensitive data remains protected during transmission
Basic Syntax −
|
rpc.svcgssd [options] |
Common Options −
Option Description −
- -f Runs svcgssd in the foreground (logs to stderr).
- -v Increases verbosity (can be used multiple times).
- -r Enables RPC debugging.
- -i Enables ID mapping debugging.
- -p principal Specifies the Kerberos principal for authentication.
- -n Uses system default credentials instead of nfs/hostname@REALM.
Examples of svcgssd Command in Linux
Checking svcgssd Status
To verify if svcgssd is running −
sudo systemctl status rpc-svcgssd
Running svcgssd in Debug Mode
To troubleshoot authentication issues −
sudo rpc.svcgssd -f -v -r
This runs svcgssd in the foreground with verbose logging.
Configuring Kerberos Authentication
Modify /etc/krb5.conf −
[libdefaults] default_realm = EXAMPLE.COM dns_lookup_kdc = true dns_lookup_realm = false
Restart svcgssd −
sudo systemctl restart rpc-svcgssd
Checking Active Security Contexts
To list active authentication sessions −
cat /proc/net/rpc/auth
Troubleshooting for svcgssd Command Issues
Issue 1 − Clients Cannot Authenticate
Solution − Check logs for errors −
journalctl -u rpc-svcgssd grep error
Ensure Kerberos tickets are valid −
klist
If expired, renew −
kinit -V nfs/server.example.com@EXAMPLE.COM
Issue 2 − svcgssd Fails to Start
Solution − Verify configuration −
cat /etc/nfs.conf grep svcgssd
Restart the service −
sudo systemctl restart rpc-svcgssd
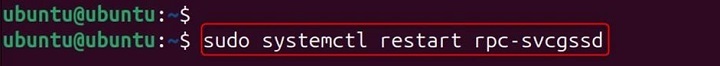
Issue 3: NFS Clients Cannot Mount Secure Shares
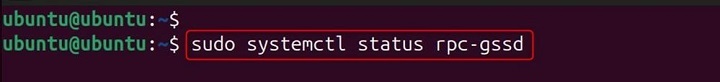
Solution − Ensure rpc.gssd is running on the client −
sudo systemctl status rpc-gssd
Check /etc/fstab for correct mount options −
server:/export /mnt nfs sec=krb5
Security Considerations of svcgssd Command
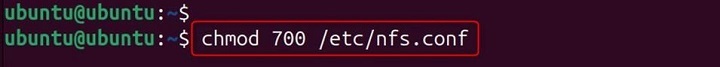
Restricting Access to svcgssd − Ensure only authorized users can access the daemon −
chmod 700 /etc/nfs.conf
Enforcing b Authentication: Use Kerberos encryption −
sec=krb5p
This ensures encrypted communication between clients and servers.
Conclusion
The svcgssd command is a critical component for securing NFS authentication using RPCSEC_GSS and Kerberos. By properly configuring and troubleshooting svcgssd, administrators can ensure secure and efficient access to NFS shares.
In summary, rpc.svcgssd is a critical component of Linux's RPCSEC_GSS implementation, enabling secure authentication and encryption for RPC-based services like NFS. Its configurable options and integration with the /etc/nfs.conf file provide administrators with the tools needed to fine-tune security settings.
By managing security contexts and facilitating encrypted communication, rpc.svcgssd ensures that RPC clients and servers can interact securely. Understanding its functionality and configuration is essential for system administrators working with NFS and other RPC-based services, as it plays a key role in maintaining a secure and efficient network environment