
gpg.ru Command in Linux
The GNU Privacy Guard (GPG) is an essential tool for data encryption and security, especially in the Linux environment. It's a versatile command-line utility that implements the OpenPGP standard, allowing users to encrypt and decrypt data, manage keys, and create digital signatures.
Whether you're a system administrator, a developer, or just a privacy-conscious user, understanding how to use gpg.ru can significantly enhance your data security.
Table of Contents
Here is a comprehensive guide to the options available with the gpg.ru command −
- Understanding the gpg.ru Command
- How to Use gpg.ru Command?
- Options gpg.ru Command
- Examples of gpg.ru Command in Linux
Understanding the gpg.ru Command
Before diving into the practical usage of gpg.ru, it's crucial to understand the concept of key pairs used in encryption. GPG operates on a public-key cryptography system, which involves two keys: a public key and a private key.
The public key is shared with others to encrypt messages or files for you, while the private key remains confidential and is used to decrypt the data encrypted with your public key.
- Encryption − Encrypt files and messages using public-key cryptography.
- Decryption − Decrypt files and messages using private-key cryptography.
- Digital Signatures − Create and verify digital signatures to ensure message authenticity and integrity.
- Key Management − Generate, import, export, and manage public and private keys.
- Password Management − Protect private keys with passwords.
How to Use gpg.ru Command?
The gpg command in Linux is a powerful tool for encrypting, decrypting, and managing digital signatures. It stands for "Gnu Privacy Guard" and is based on the OpenPGP standard.
The gpg.ru command in Linux is a powerful tool for encrypting, decrypting, signing, and verifying data using OpenPGP. It provides a wide range of options to customize its behavior.
Options gpg.ru Command
Here are some of the most common options:
| Encryption Options | Descriptions |
|---|---|
| -v | Verifies a signed file or standard input. |
| -e | Encrypts a file or standard input. |
| -r | Specifies the recipient's public key. |
| -o | Specifies the output file. |
| -c | Creates an armored file (base64-encoded). |
| Decryption Options | Descriptions |
| -d: | Decrypts a file or standard input. |
| -o: | Specifies the output file. |
| Signing Options | Descriptions |
| -s | Signs a file or standard input. |
| -o | Specifies the output file. |
| General Options | Descriptions |
| -k | Lists public keys in the keyring. |
| -a | Adds a public key to the keyring. |
| -c | Creates a new keypair. |
| -d | Deletes a public key from the keyring. |
| -o | Specifies the output file for key operations. |
| -q | Quiet mode (suppress output). |
| -v | Verbose mode (show more information). |
Examples of gpg.ru Command in Linux
In this section, we have a set of examples to demonstrate how you can use the gpg.ru command in Linux −
- Generating Your GPG Keys
- Encrypting and Decrypting Files
- Signing a File
- Verifying a Signature
- Listing keys
- Exporting a key
- Importing a key
- Deleting a key
Generating Your GPG Keys
To begin using GPG, you must generate your key pair. This can be done using the gpg --full-generate-key command, which will guide you through an interactive session to create your keys.
Generate a new key pair:
gpg --gen-key
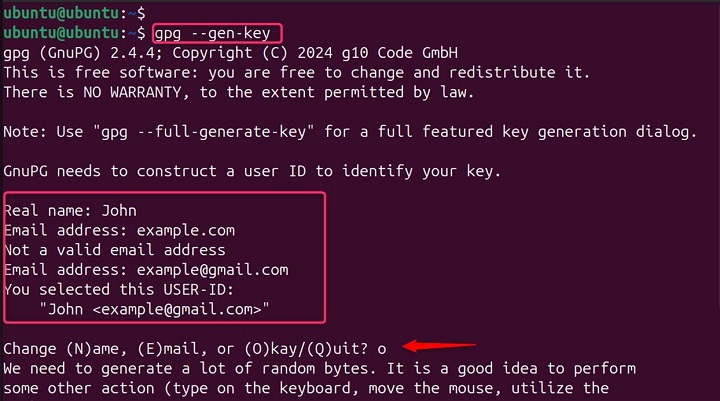
During this process, you'll be prompted to enter details such as your name and email address, which will be associated with your keys. You'll also create a passphrase to protect your private key, adding an extra layer of security.
Encrypting and Decrypting Files
Once you have your keys set up, you can start encrypting files.
Encrypting a File
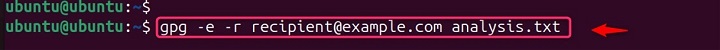
To encrypt a file for someone else, you'll need their public key. You can then use the gpg --encrypt --recipient [email address] [file] command to encrypt the file with their public key. This will encrypt the file file.txt using the public key of recipient@example.com.
gpg -e -r recipient@example.com analysis.txt
Send the encrypted file to the recipient.
Decrypting a File
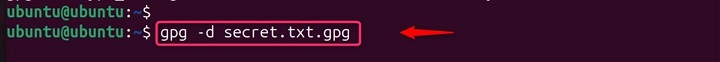
The recipient will use their private key to decrypt the file using the gpg --decrypt [file] command. This will decrypt the encrypted file using your private key.
gpg -d secret.txt.gpg
Advanced GPG Usage
GPG isn't limited to simple file encryption. It also allows you to sign documents to verify their authenticity and integrity. By signing a file with your private key, others can use your public key to confirm that the file indeed came from you and hasn't been tampered with.
Signing a File
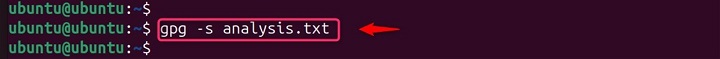
This will sign the file analysis.txt using your private key.
gpg -s analysis.txt
Verifying a Signature
This will verify the signature attached to the file file.txt.sig:
gpg -v file.txt.sig

Listing Keys
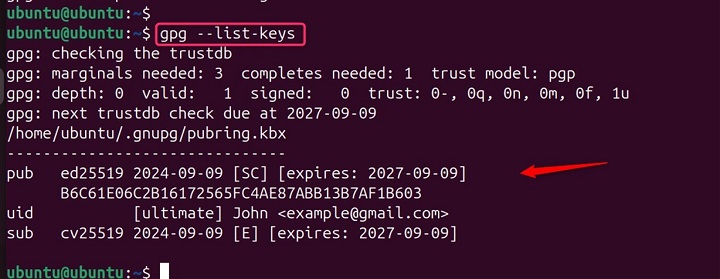
Key management is a critical aspect of using GPG effectively. It's recommended to regularly back up your private key and revocation certificate to recover your key pair in case of data loss.
gpg --list-keys
Exporting a Key
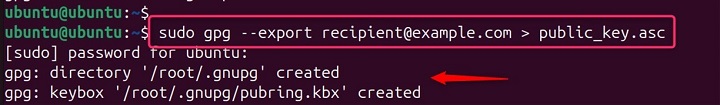
Additionally, you should keep your private key secure and never share it with anyone. Let's explore a key:
gpg --export recipient@example.com > public_key.asc
Keep exploring, practicing, and enhancing your knowledge of GPG and data encryption.
Importing a Key
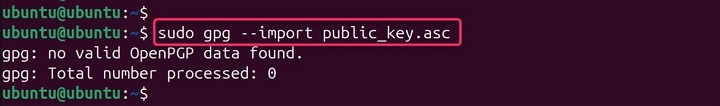
Remember, the key to effective data security is not just having the right tools but also understanding how to use them properly. Let's import a key:
gpg --import public_key.asc
Deleting a Key
Your data's security is worth the effort. Let's delete a key:
gpg --delete-key recipient@example.com
Additional Features
- Password Protection − Protect your private key with a password.
- Keyrings − Store multiple keys in keyrings for easier management.
- Trust Models − Manage trust relationships between different keys.
- Integration with other tools − GPG can be integrated with other applications for secure communication and data exchange.
Conclusion
By understanding and utilizing GPG, you can ensure that your sensitive information remains confidential and tamper-proof. Whether you're sending private emails, storing sensitive files, or verifying the authenticity of documents, GPG provides the security you need in an open-source and widely trusted format.
For those looking to delve deeper into the world of encryption and data security, mastering the gpg command is an excellent starting point. With its robust features and b encryption standards, GPG stands as a cornerstone of digital security in the Linux ecosystem.