
- OS - Home
- OS - Overview
- OS - History
- OS - Evolution
- OS - Functions
- OS - Components
- OS - Structure
- OS - Architecture
- OS - Services
- OS - Properties
- Process Management
- Processes in Operating System
- States of a Process
- Process Schedulers
- Process Control Block
- Operations on Processes
- Process Suspension and Process Switching
- Process States and the Machine Cycle
- Inter Process Communication (IPC)
- Remote Procedure Call (RPC)
- Context Switching
- Threads
- Types of Threading
- Multi-threading
- System Calls
- Scheduling Algorithms
- Process Scheduling
- Types of Scheduling
- Scheduling Algorithms Overview
- FCFS Scheduling Algorithm
- SJF Scheduling Algorithm
- Round Robin Scheduling Algorithm
- HRRN Scheduling Algorithm
- Priority Scheduling Algorithm
- Multilevel Queue Scheduling
- Lottery Scheduling Algorithm
- Starvation and Aging
- Turn Around Time & Waiting Time
- Burst Time in SJF Scheduling
- Process Synchronization
- Process Synchronization
- Solutions For Process Synchronization
- Hardware-Based Solution
- Software-Based Solution
- Critical Section Problem
- Critical Section Synchronization
- Mutual Exclusion Synchronization
- Mutual Exclusion Using Interrupt Disabling
- Peterson's Algorithm
- Dekker's Algorithm
- Bakery Algorithm
- Semaphores
- Binary Semaphores
- Counting Semaphores
- Mutex
- Turn Variable
- Bounded Buffer Problem
- Reader Writer Locks
- Test and Set Lock
- Monitors
- Sleep and Wake
- Race Condition
- Classical Synchronization Problems
- Dining Philosophers Problem
- Producer Consumer Problem
- Sleeping Barber Problem
- Reader Writer Problem
- OS Deadlock
- Introduction to Deadlock
- Conditions for Deadlock
- Deadlock Handling
- Deadlock Prevention
- Deadlock Avoidance (Banker's Algorithm)
- Deadlock Detection and Recovery
- Deadlock Ignorance
- Resource Allocation Graph
- Livelock
- Memory Management
- Memory Management
- Logical and Physical Address
- Contiguous Memory Allocation
- Non-Contiguous Memory Allocation
- First Fit Algorithm
- Next Fit Algorithm
- Best Fit Algorithm
- Worst Fit Algorithm
- Buffering
- Fragmentation
- Compaction
- Virtual Memory
- Segmentation
- Paged Segmentation & Segmented Paging
- Buddy System
- Slab Allocation
- Overlays
- Free Space Management
- Locality of Reference
- Paging and Page Replacement
- Paging
- Demand Paging
- Page Table
- Page Replacement Algorithms
- Second Chance Page Replacement
- Optimal Page Replacement Algorithm
- Belady's Anomaly
- Thrashing
- Storage and File Management
- File Systems
- File Attributes
- Structures of Directory
- Linked Index Allocation
- Indexed Allocation
- Disk Scheduling Algorithms
- FCFS Disk Scheduling
- SSTF Disk Scheduling
- SCAN Disk Scheduling
- LOOK Disk Scheduling
- I/O Systems
- I/O Hardware
- I/O Software
- I/O Programmed
- I/O Interrupt-Initiated
- Direct Memory Access
- OS Types
- OS - Types
- OS - Batch Processing
- OS - Multiprogramming
- OS - Multitasking
- OS - Multiprocessing
- OS - Distributed
- OS - Real-Time
- OS - Single User
- OS - Monolithic
- OS - Embedded
- Popular Operating Systems
- OS - Hybrid
- OS - Zephyr
- OS - Nix
- OS - Linux
- OS - Blackberry
- OS - Garuda
- OS - Tails
- OS - Clustered
- OS - Haiku
- OS - AIX
- OS - Solus
- OS - Tizen
- OS - Bharat
- OS - Fire
- OS - Bliss
- OS - VxWorks
- Miscellaneous Topics
- OS - Security
- OS Questions Answers
- OS - Questions Answers
- OS Useful Resources
- OS - Quick Guide
- OS - Useful Resources
- OS - Discussion
Operating System - Direct Memory Access
Input/Output operations (I/O) are an important part of an operating system. I/O operations allows communication between the CPU and other devices such as keyboards, mouse, printers, and storage drives. There are various I/O techniques like programmed I/O, interrupt I/O and direct memory access(DMA) out of which DMA does not need CPU continuously.
What is DMA I/O?
Direct Memory Access (DMA) is a technique in which a dedicated hardware (DMA Controller) is used to handle the data transfer between memory and I/O devices. In DMA, CPU initiates the transfer, and configures the DMA controller with required parameters. It makes DMA method independent of CPU. Using DMA, the data can be directly transferred to/from devices to the main memory.
Characteristics of DMA I/O
The key features/characteristics of Direct Memory Access are mentioned below −
- It requires CPU only at the start and at the end.
- It uses a dedicated hardware DMA controller.
- It transfers data directly from I/O device to/from memory.
- It can transfer large amount of data at a time unlike Programmed I/O that transfers a single Byte/character at a time.
- Increase CPU efficiency and reduces CPU overhead as the CPU is required at only beginning and end of the transfer.
- It is used in disk I/O, graphics devices, network packets, audio/video streaming.
How Does Direct Memory Access (DMA) Work?
The working of Direct Memory Access (DMA) is given below in 7 steps −
- In the beginning, the CPU configures the DMA controller and provides parameters such as: memory address, I/O device, and transfer size.
- Then, I/O device sends a DMA request signal to the DMA controller when data is ready to transfer.
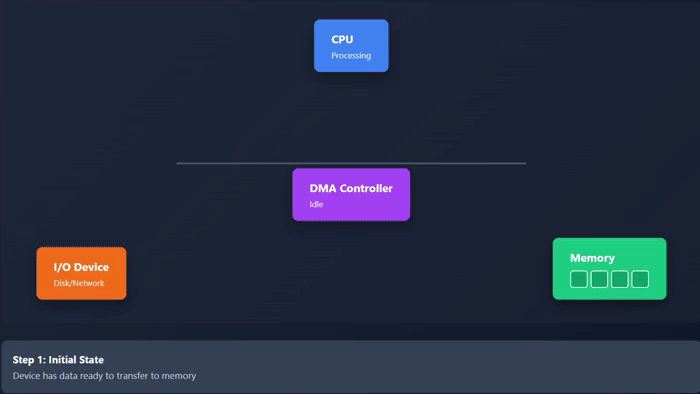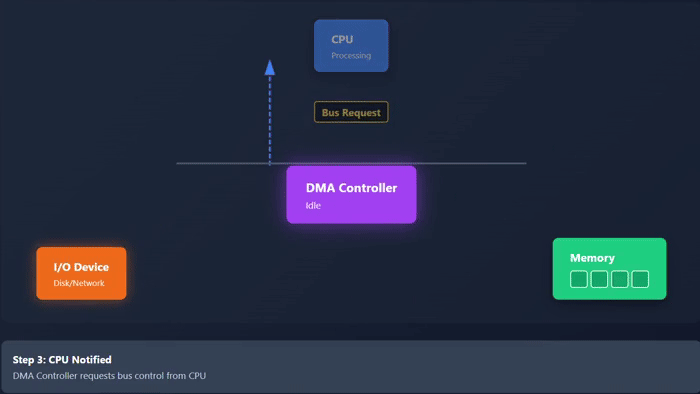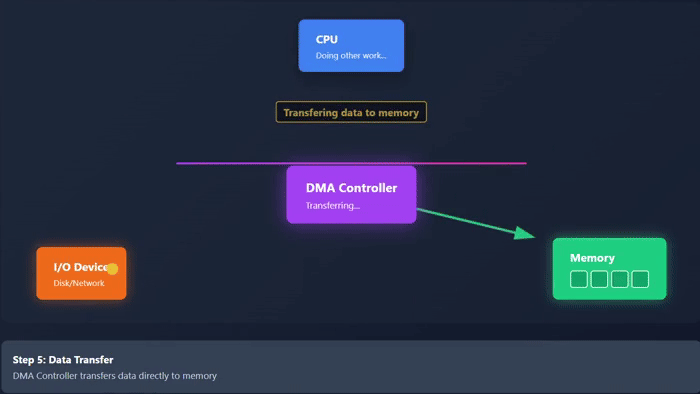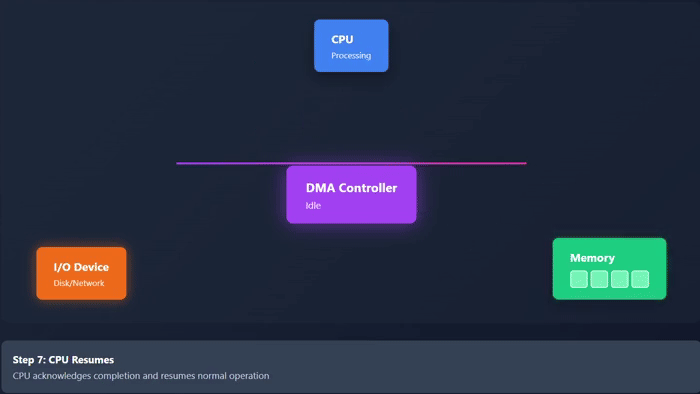
- The DMA controller then requests CPU for control of system bus.
- The CPU grants bus control to the DMA controller.
- Then, DMA controller transfers data directly between memory and I/O device.
- When transfer of all the data is completed, then DMA controller gives the access of bus back to the CPU.
- At the end, the DMA controller sends an interrupt signal to the CPU. It represents that the transfer is completed.
Take a look at the following animation. It depicts visually how the DMA works −
DMA Controller
A DMA(Direct Memory Access) controller is a special hardware that transfers data directly between memory and I/O devices without any involvement of CPU. It has four components which are listed below −
- Address Register − It stores the memory address from where the data should be read or written to.
- Data Register − It is used to temporarily store the data being transferred between memory and I/O device.
- Control Logic − It manages the complete transfer process like receiving commands from the CPU, processing signals from devices, and controlling the address and data buses.
- Count Register − It keeps a track of number of bytes that are remaining to transfer.
- Control Register − It specify mode of transfer, direction, and other parameters.
Transfer Modes in DMA
There are three different modes of transfer used by DMA which are as follows −
- Burst Mode − In burst mode, DMA transfers a complete block of data in one go.
- Cycle Stealing Mode − In this mode, DMA transfers one byte/word at a time and then releases the bus.
- Transparent Mode − In the transparent mode, DMA uses bus only when CPU is not using it. It is the slowest transfer mode.
Differences Between Programmed, Interrupt-Initiated and DMA I/O
The differences between Programmed I/O, Interrupt-Initiated I/O and Direct Memory Access(DMA) is mentioned below −
| Programmed I/O | Interrupt-Initiated I/O | Direct Memory Access |
|---|---|---|
| It uses concept of polling for implementation. | It uses interrupts. | It uses a hardware DMA controller. |
| It is used in simple devices and for small amount of data transfers. | It is used in Keyboards, mouse, ports. | It is used in disk drives, network cards, graphics cards, and for large data transfers. |
| There is no interrupts in this. | In this one interrupt per byte/word transferred. | One interrupt in needed at the end of transfer. |
| Example: Simple sensors, LEDs, basic displays. | Example: Keyboard, mouse, serial/parallel ports. | Example: Hard disks, SSDs, network cards, sound cards, GPUs |
| CPU efficiency is very low due to polling. | CPU efficiency is moderate. | CPU is highly efficient since CPU is not involved. |
Advantages of DMA
The advantages of Direct Memory Access(DMA) are as follows −
- Data transfer is faster in DMA compared to Programmed and Interrupt-Initiated I/O.
- Less CPU overhead as DMA controller handles the complete task and CPU is required only at the beginning and at the end.
- Improved multitasking as CPU can perform other task and at the same time I/O operation can occur concurrently.
- Best for high-speed devices.
- Low latency since CPU is not involved and everything is managed by a dedicated DMA controller.
Disadvantages of DMA
The disadvantages of Direct Memory Access(DMA) are as follows −
- High cost due to extra hardware (DMA controller).
- CPU operations may slow down as DMA controller has access of Bus.
- More complex to design and implement.
- It is hard to debug.
- It is not suitable for small data transfers.
Applications of Direct Memory Access
Here are some of the real-world application of DMA −
- It is used in hard drives and SSDs to transfer data.
- It is used in Network interface cards(NIC) for moving the packet data between network buffers and main memory.
- It is used in graphics cards for transferring the texture data, frame buffers, and commands between memory and video memory.
- It is used in sound cards to stream audio data continuously, for smooth playback without any latency.
Conclusion
Direct Memory Access (DMA) is a technique in which a dedicated hardware (DMA Controller) is used to handle the data transfer between memory and I/O devices. This chapter provides a detailed explanation of DMA, its characteristics, DMA controller, working, transfer modes, differences from programmed and interrupt-initiated I/O, real-life implementation, advantages, and disadvantages of DMA.