
- OS - Home
- OS - Overview
- OS - History
- OS - Evolution
- OS - Functions
- OS - Components
- OS - Structure
- OS - Architecture
- OS - Services
- OS - Properties
- Process Management
- Processes in Operating System
- States of a Process
- Process Schedulers
- Process Control Block
- Operations on Processes
- Process Suspension and Process Switching
- Process States and the Machine Cycle
- Inter Process Communication (IPC)
- Remote Procedure Call (RPC)
- Context Switching
- Threads
- Types of Threading
- Multi-threading
- System Calls
- Scheduling Algorithms
- Process Scheduling
- Types of Scheduling
- Scheduling Algorithms Overview
- FCFS Scheduling Algorithm
- SJF Scheduling Algorithm
- Round Robin Scheduling Algorithm
- HRRN Scheduling Algorithm
- Priority Scheduling Algorithm
- Multilevel Queue Scheduling
- Lottery Scheduling Algorithm
- Starvation and Aging
- Turn Around Time & Waiting Time
- Burst Time in SJF Scheduling
- Process Synchronization
- Process Synchronization
- Solutions For Process Synchronization
- Hardware-Based Solution
- Software-Based Solution
- Critical Section Problem
- Critical Section Synchronization
- Mutual Exclusion Synchronization
- Mutual Exclusion Using Interrupt Disabling
- Peterson's Algorithm
- Dekker's Algorithm
- Bakery Algorithm
- Semaphores
- Binary Semaphores
- Counting Semaphores
- Mutex
- Turn Variable
- Bounded Buffer Problem
- Reader Writer Locks
- Test and Set Lock
- Monitors
- Sleep and Wake
- Race Condition
- Classical Synchronization Problems
- Dining Philosophers Problem
- Producer Consumer Problem
- Sleeping Barber Problem
- Reader Writer Problem
- OS Deadlock
- Introduction to Deadlock
- Conditions for Deadlock
- Deadlock Handling
- Deadlock Prevention
- Deadlock Avoidance (Banker's Algorithm)
- Deadlock Detection and Recovery
- Deadlock Ignorance
- Resource Allocation Graph
- Livelock
- Memory Management
- Memory Management
- Logical and Physical Address
- Contiguous Memory Allocation
- Non-Contiguous Memory Allocation
- First Fit Algorithm
- Next Fit Algorithm
- Best Fit Algorithm
- Worst Fit Algorithm
- Buffering
- Fragmentation
- Compaction
- Virtual Memory
- Segmentation
- Paged Segmentation & Segmented Paging
- Buddy System
- Slab Allocation
- Overlays
- Free Space Management
- Locality of Reference
- Paging and Page Replacement
- Paging
- Demand Paging
- Page Table
- Page Replacement Algorithms
- Second Chance Page Replacement
- Optimal Page Replacement Algorithm
- Belady's Anomaly
- Thrashing
- Storage and File Management
- File Systems
- File Attributes
- Structures of Directory
- Linked Index Allocation
- Indexed Allocation
- Disk Scheduling Algorithms
- FCFS Disk Scheduling
- SSTF Disk Scheduling
- SCAN Disk Scheduling
- LOOK Disk Scheduling
- I/O Systems
- I/O Hardware
- I/O Software
- I/O Programmed
- I/O Interrupt-Initiated
- Direct Memory Access
- OS Types
- OS - Types
- OS - Batch Processing
- OS - Multiprogramming
- OS - Multitasking
- OS - Multiprocessing
- OS - Distributed
- OS - Real-Time
- OS - Single User
- OS - Monolithic
- OS - Embedded
- Popular Operating Systems
- OS - Hybrid
- OS - Zephyr
- OS - Nix
- OS - Linux
- OS - Blackberry
- OS - Garuda
- OS - Tails
- OS - Clustered
- OS - Haiku
- OS - AIX
- OS - Solus
- OS - Tizen
- OS - Bharat
- OS - Fire
- OS - Bliss
- OS - VxWorks
- Miscellaneous Topics
- OS - Security
- OS Questions Answers
- OS - Questions Answers
- OS Useful Resources
- OS - Quick Guide
- OS - Useful Resources
- OS - Discussion
Operating System - Deadlock Detection and Recovery
When a deadlock occurs, the operating system can use deadlock detection and recovery methods to handle the deadlock. In this chapter, we will discuss how deadlocks are detected and what the operating system does to recover from a deadlock.
Deadlock Detection in Operating System
The deadlock detection is a mechanism implemented in operating systems to identify deadlocks. It works by periodically running a deadlock detection algorithm in the system. It analyzes the current state of resource allocation and process states to identify if a deadlock has occurred.
There are several algorithms used for deadlock detection, including −
- Resource Allocation Graph (RAG) Algorithm
- Wait-for Graph Algorithm
- Banker's Algorithm for Deadlock Detection
Resource Allocation Graph (RAG) Algorithm
The Resource Allocation Graph (RAG) is a directed graph that represents the allocation of resources to processes and the requests made by processes for resources. In this graph, processes and resources are represented as nodes. Edges from a process to a resource represent a request for that resource, and edges from a resource to a process represent the allocation of that resource to the process.
To detect deadlock using RAG, the operating system looks for cycles in the graph. If a cycle is found, it indicates that a deadlock has occurred among the processes involved in the cycle.
The image below shows a Resource Allocation Graph with a deadlock situation −
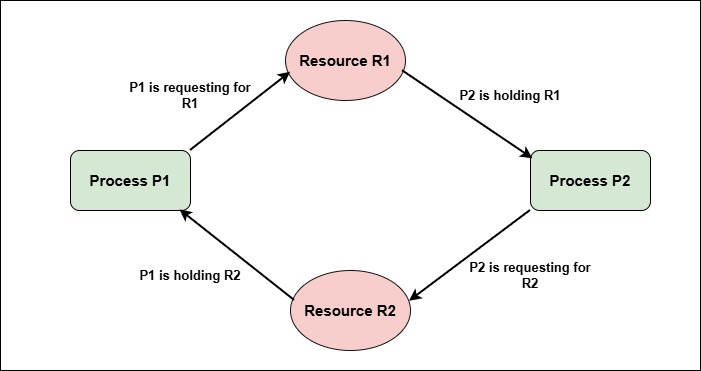
In this example, Process P1 holds Resource R2 and is waiting for Resource R1 to be ready. Meanwhile, Process P2 holds Resource R1 and is waiting for Resource R2 to be ready. This creates a cycle in the graph, P1 -> R1 -> P2 -> R2 -> P1, indicating a deadlock situation.
Note: Operating systems may use algorithms like Topological Sorting or Depth-First Traversal to detect cycles in the Resource Allocation Graph.
Wait-for Graph Algorithm
The Wait-for Graph is a simplified version of the Resource Allocation Graph. In this graph, only processes are represented as nodes, and edges represent the waiting relationships between processes. An edge from process P1 to process P2 indicates that P1 is waiting for a resource held by P2.
To detect deadlock using the Wait-for Graph, the operating system looks for cycles in the graph. If a cycle is found, it indicates that a deadlock has occurred among the processes involved in the cycle.
The image below shows corresponding Wait-for Graph for the previous example −
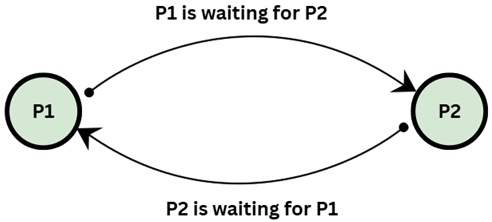
In this wait-for graph, there is a cycle P1 -> P2 -> P1, indicating a deadlock situation between processes P1 and P2.
Note: The RAG and Wait-for Graph algorithms can only be used on systems with single-instance resources. i.e, each resource type has only one instance. For systems with multiple instances of resources, the Banker's Algorithm is used.
Banker's Algorithm
The Banker's Algorithm is used for deadlock detection in systems with multiple instances of resources. It works by simulating the allocation of resources to processes and checking if the system remains in a safe state after the allocation.
To detect deadlock using the Banker's Algorithm, the operating system periodically checks the state of resource allocation and process states. If it finds that the system is in an unsafe state, it indicates that a deadlock has occurred.
Deadlock Recovery in Operating System
Once a deadlock is detected in a system, the operating system take few actions to recover from the deadlock. The section below discusses the approaches used for deadlock recovery -
1. Process Termination
When a deadlock is detected, one way to recover from it is to terminate one or more processes involved in the deadlock. The os will terminate the processes one by one until the deadlock is resolved. The resources held by the terminated processes are then released and can be allocated to other processes.
For example, consider three processes P1, P2, and P3 involved in a deadlock.
P1 - Holding R1, Waiting for R2 P2 - Holding R2, Waiting for R3 P3 - Holding R3, Waiting for R1
To recover from the deadlock, the operating system can terminate process P1. This will release resource R1, allowing process P3 to proceed and complete its execution. Once P3 completes, it releases resource R3, allowing process P2 to proceed and complete its execution as well.
2. Resource Preemption
Another approach to recover from deadlock is to take back the resources from the processes involved in the deadlock. The is called resource preemption. The preempted resources are then allocated to other processes involved in the deadlock. This process continues until the deadlock is resolved.
For example, consider the same three processes P1, P2, and P3 involved in a deadlock as mentioned above.
P1 - Holding R1, Waiting for R2 P2 - Holding R2, Waiting for R3 P3 - Holding R3, Waiting for R1
To recover from the deadlock, the operating system can take back resource R1 from process P1 and allocate it to process P3. So P3 can proceed and complete its execution. Once P3 completes, it releases resource R3, so P2 can complete its execution as well. Finally, P1 can get resource R2 and complete its execution.
Conclusion
Deadlock detection and recovery is an important mechanism in operating systems to ensure that processes can continue executing without getting stuck in a deadlock situation. To detect deadlock, operating systems use algorithms like RAG, Wait-for Graph, and Banker's Algorithm. If there are multiple instances of resources, Banker's Algorithm is used for deadlock detection. Once a deadlock is detected, the operating system can recover from it by terminating processes or preempting resources.