
- Data Comm & Networks Home
- DCN - Overview
- DCN - What is Computer Network
- DCN - Uses of Computer Network
- DCN - Computer Network Types
- DCN - Network LAN Technologies
- DCN - Computer Network Models
- DCN - Computer Network Security
- DCN - Components
- DCN - Connectors
- DCN - Switches
- DCN - Repeaters
- DCN - Gateways
- DCN - Bridges
- DCN - Socket
- DCN - Network Interface Card
- DCN - NIC: Pros and Cons
- DCN - Network Hardware
- DCN - Network Port
- Computer Network Topologies
- DCN - Computer Network Topologies
- DCN - Point-to-point Topology
- DCN - Bus Topology
- DCN - Star Topology
- DCN - Ring Topology
- DCN - Mesh Topology
- DCN - Tree Topology
- DCN - Hybrid Topology
- Physical Layer
- DCN - Physical Layer Introduction
- DCN - Digital Transmission
- DCN - Analog Transmission
- DCN - Transmission media
- DCN - Wireless Transmission
- DCN - Transmission Impairments
- DCN - Multiplexing
- DCN - Network Switching
- DCN - Circuit Switching
- DCN - Packet Switching
- DCN - Message Switching
- Data Link Layer
- DCN - Data Link Layer Introduction
- DCN - Data Link Control & Protocols
- DCN - RMON
- DCN - Token Ring Network
- DCN - Hamming Code
- DCN - Byte Stuffing
- DCN - Channel Allocation
- DCN - MAC Address
- DCN - Address Resolution Protocol
- DCN - Cyclic Redundancy Checks
- DCN - Error Control
- DCN - Flow Control
- DCN - Framing
- DCN - Error Detection & Correction
- DCN - Error Correcting Codes
- DCN - Parity Bits
- Network Layer
- DCN - Network Layer Introduction
- DCN - Network Addressing
- DCN - Routing
- DCN - Routing Table
- DCN - Internetworking
- DCN - Network Layer Protocols
- DCN - Routing Information Protocol
- DCN - Border Gateway Protocol
- DCN - OSPF Protocol
- DCN - Network Address Translation
- DCN - Network Address Translation Types
- Transport Layer
- DCN - Transport Layer Introduction
- DCN - Transmission Control Protocol
- DCN - User Datagram Protocol
- DCN - Congestion Control
- DCN - Open Loop Congestion Control
- DCN - Closed Loop Congestion Control
- DCN - Congestion Control Algorithms
- DCN - Token Bucket Algorithm
- DCN - TCP Tahoe Algorithm
- DCN - TCP Reno Algorithm
- DCN - TCP New Reno Algorithm
- DCN - TCP BIC Algorithm
- DCN - TCP CUBIC Algorithm
- DCN - TCP Service Model
- DCN - TLS Handshake
- DCN - TCP Vs. UDP
- Application Layer
- DCN - Session Layer
- DCN - Presentation Layer
- DCN - Application Layer Introduction
- DCN - Client-Server Model
- DCN - Application Protocols
- DCN - Network Services
- DCN - Virtual Private Network
- DCN - Load Shedding
- DCN - Optimality Principle
- DCN - Service Primitives
- DCN - Services of Network Security
- DCN - Hypertext Transfer Protocol
- DCN - File Transfer Protocol
- DCN - Secure Socket Layer
- Network Protocols
- DCN - ALOHA Protocol
- DCN - Pure ALOHA Protocol
- DCN - Sliding Window Protocol
- DCN - Stop and Wait Protocol
- DCN - Link State Routing
- DCN - Link State Routing Protocol
- Network Algorithms
- DCN - Shortest Path Algorithm
- DCN - Routing Algorithm
- DCN - Adaptive Routing Algorithms
- DCN - Non-Adaptive Routing Algorithms
- DCN - Leaky Bucket Algorithm
- Wireless Networks
- DCN - Wireless Networks
- DCN - Wireless LANs
- DCN - Wireless LAN & IEEE 802.11
- DCN - IEEE 802.11 Wireless LAN Standards
- DCN - IEEE 802.11 Networks
- Multiplexing
- DCN - Multiplexing & Its Types
- DCN - Time Division Multiplexing
- DCN - Synchronous TDM
- DCN - Asynchronous TDM
- DCN - Synchronous Vs. Asynchronous TDM
- DCN - Frequency Division Multiplexing
- DCN - TDM Vs. FDM
- DCN - Code Division Multiplexing
- DCN - Wavelength Division Multiplexing
- Miscellaneous
- DCN - Shortest Path Routing
- DCN - B-ISDN Reference Model
- DCN - Design Issues For Layers
- DCN - Selective-repeat ARQ
- DCN - Flooding
- DCN - E-Mail Format
- DCN - Cryptography
- DCN - Unicast, Broadcast, & Multicast
- DCN - Network Virtualization
- DCN - Flow Vs. Congestion Control
- DCN - Asynchronous Transfer Mode
- DCN - ATM Networks
- DCN - Synchronous Vs. Asynchronous Transmission
- DCN - Network Attacks
- DCN - WiMax
- DCN - Buffering
- DCN - Authentication
- DCN Useful Resources
- DCN - Quick Guide
- DCN - Useful Resources
- DCN - Discussion
Open Loop Congestion Control in Computer Network
Congestion in computer networks occurs when too many packets are present in a part of the network. The number of incoming packets becomes more than the available resources. Due to congestion, it can cause packet delay, reduces the performance of a network, decreased throughput, increased delay and packet loss. Congestion control helps in managing this traffic overload.
There are two main approaches for congestion control: Open loop and Closed loop. This chapter focuses on open loop congestion control.
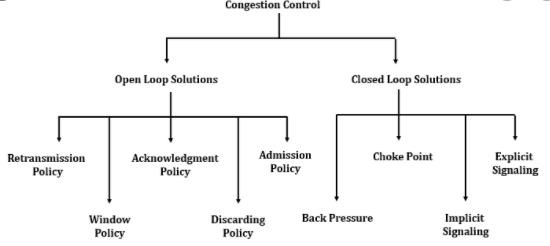
What is Open Loop Congestion Control?
Open loop congestion control is a congestion prevention method for congestion management. These techniques are designed to prevent congestion before it actually occurs, rather than correcting it after detection.
Characteristics of Open Loop Congestion Control
Some of the important characteristics of open loop method are highlighted below −
- In open loop congestion control, decisions are made in advance. It does not depend on response to current network conditions.
- Open loop techniques do not depend on feedback from the network for its current state, unlike closed loop congestion control.
- In open loop, rules are set during network design or during connection establishment. It remains fixed during data transmission and can not be changed.
Open loop congestion control is a congestion prevention method that avoids congestion completely, instead of solving the congestion problem after it has occurred.
Open Loop Congestion Control Techniques
Control policies are applied to prevent congestion before it takes place. Congestion is handled either by the source or the destination. In this section, we have highlighted some of the major policies of open loop congestion control.
Retransmission Policy
During transmission, when packets are lost or get corrupted, the sender may retransmit them. The retransmission should be designed in such a way that there should not be excess retransmission. This can worsen congestion. So, the timer should be set accordingly for congestion prevention while maintaining the efficiency.
For example: If a sender uses too short timeout period, then it might retransmit packets that are simply delayed and not lost. This will add duplicate packets and make the network even more congested.
Window Policy
Window policy controls the number of packets that is sent at a time using a fixed window size. The window size represents number of packets that can be in transit before receiving acknowledgments. It is useful in preventing the sender from overwhelming the network.
The window size should be chosen carefully as smaller window reduces chance of congestion but it may under utilize available bandwidth. Similarly, a larger window gives maximum throughput but there is chance of congestion.
There are three approaches to implement window-based congestion control −
- Sender Window − The sender window limits the amount of data a sender can transmit before receiving acknowledgment.
- Receiver Window − The receiver window represents the buffer space available to receiver.
- Selective Acknowledgment − The selective acknowledgement allows efficient use of the window. It acknowledges specific received packets only.
Acknowledgment Policy
The acknowledgement policy is imposed by the receiver and it may affect congestion. If the receiver does not acknowledge every packet it receives, it may slow down the sender and help prevent congestion. A receiver may send an acknowledgment only if it has a packet to be sent or a special timer expires. A receiver may decide to acknowledge only N packets at a time.
It uses the following techniques −
- Delayed ACK − In this technique, the receiver waits to combine multiple acknowledgments instead of acknowledging every single packet immediately.
- Cumulative ACK − It acknowledges all packets up to a sequence number with a single message.
- Selective ACK − It only acknowledges specific received packets.
Discarding Policy
A discarding policy by the routers prevents congestion and at the same time may not harm the integrity of the transmission. When buffers become full, routers may discard packets based on priority rules instead of accepting every packet.
Some of the common discarding policies are mentioned below −
- Tail Drop − In tail drop, newly arriving packets are discarded when buffers are full.
- Random Early Detection − It randomly drop packets before buffers fill completely. This indicates senders to slow down sending the packets.
- Priority Based Discard − It starts dropping packets with lower priority.
Admission Policy
Admission policy controls which connections should be allowed into the network. It allows or denies new traffic based on available resources. When network is already heavily loaded, new connections are blocked. It is a quality-of-service mechanism, that prevents congestion in virtual circuit networks. For example: A video streaming service can be denied admission to a network if it would cause delays for current voice calls.
Admission policy uses the following mechanisms −
- Connection Admission Control (CAC) − In virtual circuit networks, the network decides whether to accept a new connection based on current load.
- Quality of Service (QoS) Guarantees − New connections are accepted only if the requirements can be satisfied without degrading current traffic.
- Traffic Contracts − In this, users specify their traffic characteristics, and the network allows them only if resources are available.
Open Loop Congestion Control: Pros and Cons
The advantages of using open loop congestion control are listed below −
- It doesn't need any feedback from the network, hence it is simple and easier to design and implement.
- Lower overhead as congestion detection is not needed and there is no feedback messages.
- It avoids congestion problems before they affect performance.
- Open loop congestion control is suitable for real-time applications.
Here are the limitations of using open loop congestion control −
- It is static and hence cannot adapt to any change in network conditions.
- It may under utilize the network capacity.
- Its scope is limited as it may not handle all congestion conditions.
Applications of Open Loop Congestion Control Technique
Open loop congestion control techniques are used in various networking scenarios. Some of its real-world applications are listed here −
- QoS Networks − Open loop techniques such as admission control and traffic shaping are important in networks providing Quality of Service (QoS) guarantees.
- Multimedia Streaming − Traffic shaping algorithms deliver smooth and consistent audio and video.
- Network Design − Buffer sizing, link capacity planning, and routing policies are examples of open loop policies made during network design.
Difference between Open Loop and Closed Loop Congestion Control
The following table compares and contrasts the features of Open Loop and Closed Loop congestion control techniques −
| Open Loop Congestion Control | Closed Loop Congestion Control |
|---|---|
| It uses preventive method to prevent congestion before it occurs. | It uses reactive method to handle congestion after it's detected. |
| It doesn't monitor current network conditions. | It continuously monitors network conditions to adjust the traffic flow accordingly. |
| It does not use any feedback mechanism. | It uses feedback mechanism. |
| It uses static or pre-defined policies. These policies remains fixed during data transmission. | It uses dynamic policies to adapt to real-time change in network conditions. |
| In this, decisions are made during network design or when connection is established. | In closed loop, decisions are made during data transmission based on current network state. |
| It is simple to implement with less overhead. | It is complex to implement with higher overhead since it monitors and has feedback. |
| It may under utilize network capacity. | It has better resource utilization. |
| Examples: retransmission policy, window policy, admission control, and traffic shaping. | Examples: TCP congestion control (like Slow Start, Congestion Avoidance), and Explicit Congestion Notification (ECN) |
| It is used in predictable traffic patterns and for real-time applications. | It is useful in variable traffic patterns. |
| Since it has static policies, it cannot recover from unexpected congestion conditions. | It is adaptive so it can detect and recover from congestion. |
Conclusion
Open loop congestion control is a proactive method that implements congestion preventive policies and attempts to stop congestions before they could take place. It has static policies and cannot adapt to real-time network conditions.
Open loop congestion control is simple to implement with low overhead. Open loop methods are useful in predictable traffic patterns and in real-time applications where consistent performance is important.