
- Data Comm & Networks Home
- DCN - Overview
- DCN - What is Computer Network
- DCN - Uses of Computer Network
- DCN - Computer Network Types
- DCN - Network LAN Technologies
- DCN - Computer Network Models
- DCN - Computer Network Security
- DCN - Components
- DCN - Connectors
- DCN - Switches
- DCN - Repeaters
- DCN - Gateways
- DCN - Bridges
- DCN - Socket
- DCN - Network Interface Card
- DCN - NIC: Pros and Cons
- DCN - Network Hardware
- DCN - Network Port
- Computer Network Topologies
- DCN - Computer Network Topologies
- DCN - Point-to-point Topology
- DCN - Bus Topology
- DCN - Star Topology
- DCN - Ring Topology
- DCN - Mesh Topology
- DCN - Tree Topology
- DCN - Hybrid Topology
- Physical Layer
- DCN - Physical Layer Introduction
- DCN - Digital Transmission
- DCN - Analog Transmission
- DCN - Transmission media
- DCN - Wireless Transmission
- DCN - Transmission Impairments
- DCN - Multiplexing
- DCN - Network Switching
- DCN - Circuit Switching
- DCN - Packet Switching
- DCN - Message Switching
- Data Link Layer
- DCN - Data Link Layer Introduction
- DCN - Data Link Control & Protocols
- DCN - RMON
- DCN - Token Ring Network
- DCN - Hamming Code
- DCN - Byte Stuffing
- DCN - Channel Allocation
- DCN - MAC Address
- DCN - Address Resolution Protocol
- DCN - Cyclic Redundancy Checks
- DCN - Error Control
- DCN - Flow Control
- DCN - Framing
- DCN - Error Detection & Correction
- DCN - Error Correcting Codes
- DCN - Parity Bits
- Network Layer
- DCN - Network Layer Introduction
- DCN - Network Addressing
- DCN - Routing
- DCN - Routing Table
- DCN - Internetworking
- DCN - Network Layer Protocols
- DCN - Routing Information Protocol
- DCN - Border Gateway Protocol
- DCN - OSPF Protocol
- DCN - Network Address Translation
- DCN - Network Address Translation Types
- Transport Layer
- DCN - Transport Layer Introduction
- DCN - Transmission Control Protocol
- DCN - User Datagram Protocol
- DCN - Congestion Control
- DCN - Open Loop Congestion Control
- DCN - Closed Loop Congestion Control
- DCN - Congestion Control Algorithms
- DCN - Token Bucket Algorithm
- DCN - TCP Tahoe Algorithm
- DCN - TCP Reno Algorithm
- DCN - TCP New Reno Algorithm
- DCN - TCP BIC Algorithm
- DCN - TCP CUBIC Algorithm
- DCN - TCP Service Model
- DCN - TLS Handshake
- DCN - TCP Vs. UDP
- Application Layer
- DCN - Session Layer
- DCN - Presentation Layer
- DCN - Application Layer Introduction
- DCN - Client-Server Model
- DCN - Application Protocols
- DCN - Network Services
- DCN - Virtual Private Network
- DCN - Load Shedding
- DCN - Optimality Principle
- DCN - Service Primitives
- DCN - Services of Network Security
- DCN - Hypertext Transfer Protocol
- DCN - File Transfer Protocol
- DCN - Secure Socket Layer
- Network Protocols
- DCN - ALOHA Protocol
- DCN - Pure ALOHA Protocol
- DCN - Sliding Window Protocol
- DCN - Stop and Wait Protocol
- DCN - Link State Routing
- DCN - Link State Routing Protocol
- Network Algorithms
- DCN - Shortest Path Algorithm
- DCN - Routing Algorithm
- DCN - Adaptive Routing Algorithms
- DCN - Non-Adaptive Routing Algorithms
- DCN - Leaky Bucket Algorithm
- Wireless Networks
- DCN - Wireless Networks
- DCN - Wireless LANs
- DCN - Wireless LAN & IEEE 802.11
- DCN - IEEE 802.11 Wireless LAN Standards
- DCN - IEEE 802.11 Networks
- Multiplexing
- DCN - Multiplexing & Its Types
- DCN - Time Division Multiplexing
- DCN - Synchronous TDM
- DCN - Asynchronous TDM
- DCN - Synchronous Vs. Asynchronous TDM
- DCN - Frequency Division Multiplexing
- DCN - TDM Vs. FDM
- DCN - Code Division Multiplexing
- DCN - Wavelength Division Multiplexing
- Miscellaneous
- DCN - Shortest Path Routing
- DCN - B-ISDN Reference Model
- DCN - Design Issues For Layers
- DCN - Selective-repeat ARQ
- DCN - Flooding
- DCN - E-Mail Format
- DCN - Cryptography
- DCN - Unicast, Broadcast, & Multicast
- DCN - Network Virtualization
- DCN - Flow Vs. Congestion Control
- DCN - Asynchronous Transfer Mode
- DCN - ATM Networks
- DCN - Synchronous Vs. Asynchronous Transmission
- DCN - Network Attacks
- DCN - WiMax
- DCN - Buffering
- DCN - Authentication
- DCN Useful Resources
- DCN - Quick Guide
- DCN - Useful Resources
- DCN - Discussion
Congestion Control Algorithms
In computer networks, congestion occurs when the number of incoming packets becomes more than the available resources. Congestion leads to various problems like: it reduces the performance of a network, decreased throughput, increased delay and packet loss.
To solve the problem of congestion, we use congestion control methods in order to avoid, detect, and handle congestion in a network for maintaining the network performance. Congestion control methods reduces the delay, minimize packet loss, and maximize throughput.
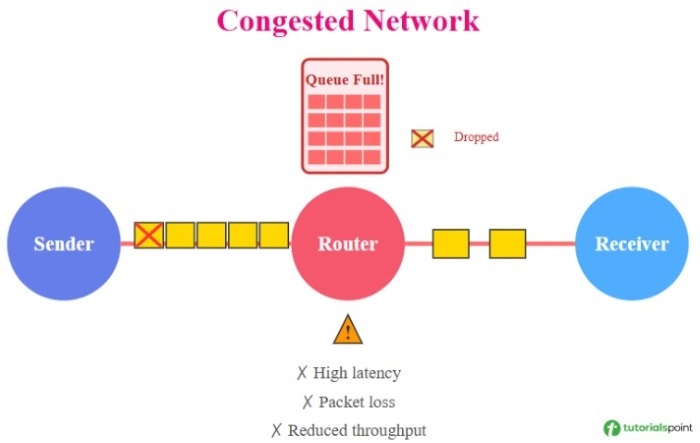
There are various types of congestion control algorithms −
- Leaky Bucket Algorithm
- Token Bucket Algorithm
- TCP Tahoe Algorithm
- TCP Reno Algorithm
- TCP New Reno Algorithm
Let's discuss each of these congestion control methods one by one.
Leaky Bucket Algorithm
The leaky bucket algorithm is a congestion control algorithm that is used for traffic shaping in computer networks. It controls the rate at which packets are sent into the network. In leaky bucket algorithm, incoming packets are stored in a buffer or bucket and are transmitted at a fixed rate. If the bucket becomes full or get overloaded and new packets arrive, then new packets are dropped. Below is an image of how leaky bucket algorithm works.
In this animation below, you can see that packets are coming at variable rate but are transmitted at a constant rate. Once the bucket is full or overloaded, the packets are dropped −
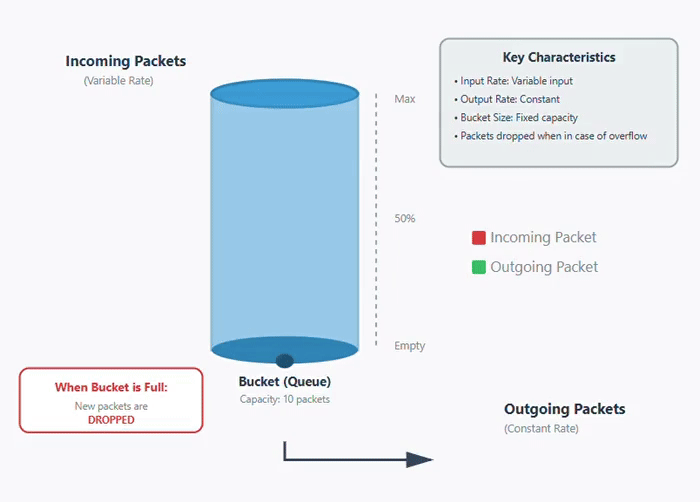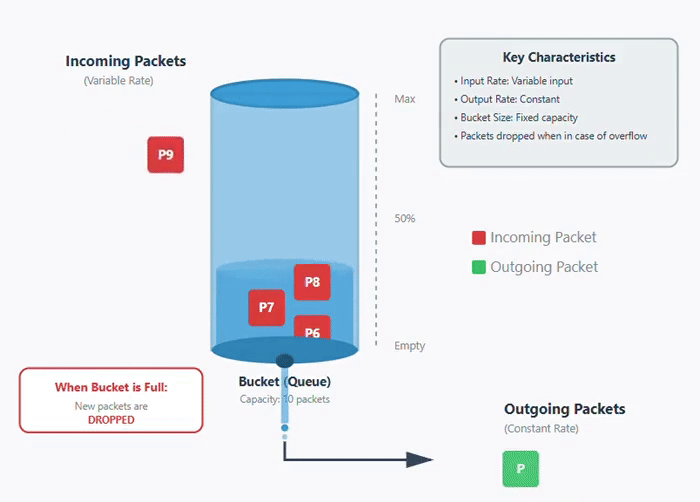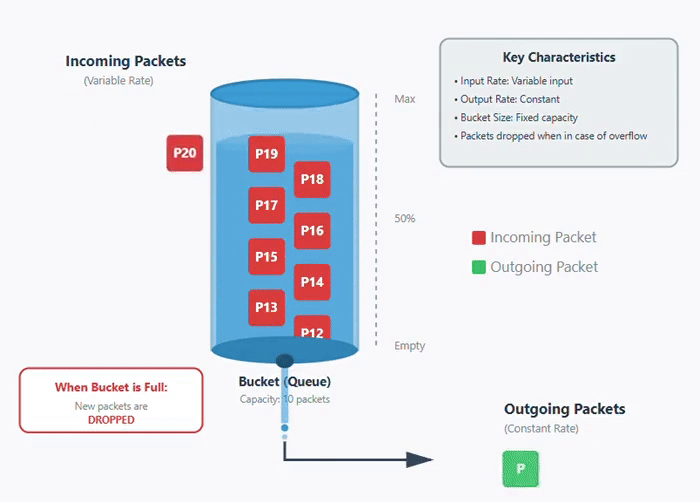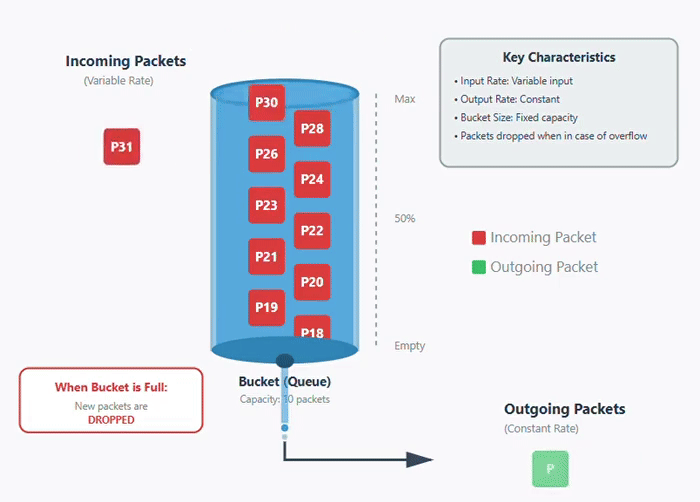
Working of Leaky Bucket Algorithm
It works on the principle of a leaky bucket that have a hole at the bottom. In a leaky bucket, the water gets stored in the bucket, but exits at a fixed rate through the leak. Similarly, the packets are stored in buffer where buffer size is limited and packets are transmitted at fixed rate as shown above in the figure.
Leaky bucket algorithm provides a constant output rate and it is simple to implement. On the downside, it may cause delay and low throughput if the outgoing rate is set too low.
Token Bucket Algorithm
Token Bucket Algorithm is a congestion control algorithm that is used for traffic shaping like leaky bucket algorithm. It limits the transmission rate of packets and helps in maintaining consistent data transmission. Tokens are generated at a constant rate and are stored in a bucket of limited capacity. Packets are only sent if tokens available is more than the size of the packet. It is Used in QoS, VoIP, and Video streaming. Below is an image of how token bucket algorithm works.
Given below is an example of token bucket algorithm. The tokens are generated at the rate of 2 per second. The maximum capacity of the bucket is of 10 tokens and currently there are 5 available tokens. A packet of size 3 arrives and since 3 < 5, the packet will be sent. Now the token remaining in the bucket is 2 and if a packet of size greater than 2 comes, then it will be dropped.
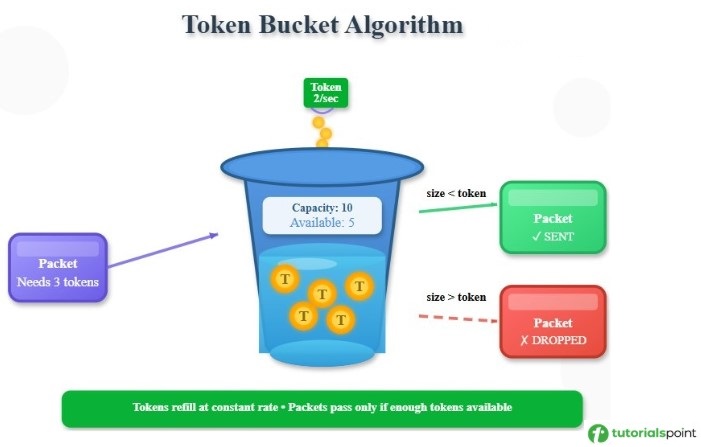
Working of Token Bucket Algorithm
Here are the steps of Working of token bucket algorithm −
- Tokens are added into a bucket at a constant rate. For example: "r" tokens per second.
- The maximum capacity of the bucket is fixed, i.e., "B" tokens.
- For sending a packet, number of tokens equal to the packet size is removed.
- If token size is greater than the packet size, then the packet is sent. Otherwise, the packet is either delayed or discarded.
The token bucket algorithm is more flexible than the leaky bucket. It provides better network utilization. It is useful in networks that handle multimedia and variable traffic. On the flipside, it is more complex than leaky bucket. When the token bucket becomes empty, packets have to wait that increases the delay.
Difference Between Leaky Bucket and Token Bucket Algorithm
Here are some differences between leaky bucket and token bucket algorithm −
| Leaky Bucket Algorithm | Token Bucket Algorithm |
|---|---|
| The output rate is fixed and constant. | The output rate is variable. |
| It works well for constant bit rate traffic. | It works well for variable bit rate traffic. |
| Packets are transmitted at fixed intervals. | If tokens are available, packets are transmitted immediately. |
| It is less flexible. | It is more flexible compared to leaky bucket. |
| It has higher delay. | It has less delay. |
| It is used for audio streaming and constant video streaming. | It is used for multimedia applications, cloud services, and APIs with rate limits. |
TCP Tahoe Algorithm
TCP Tahoe is one of the earliest congestion control algorithms used in Transmission Control Protocol (TCP) that automatically adjusts its packet sending rate based on the network conditions. It assumes a packet loss as a sign of network congestion and drastically reduces the data transmission rate.
The primary objective of TCP Tahoe was to provide a reliable and efficient approach to controlling congestion in computer networks. This involved detecting network congestion and implementing mechanisms to reduce data transmission rates to prevent packet loss.
TCP Tahoe algorithm is a simple and stable congestion control mechanism. It increases the reliability of data transmission. On the downside, it suffers from inefficient bandwidth utilization as window size drops to 1 MSS. It treats a packet loss like a congestion. We will discuss this algorithm in detail in a later chapter.
TCP Reno Algorithm
TCP Reno is an improved version of the TCP Tahoe algorithm. One major feature of TCP Reno is its fast recovery phase from packet loss using 3 duplicate ACKs. When a packet loss occurs, it does not retransmitting all unacknowledged packets. It only retransmits the lost packets with new packets. This reduces the delays in data transmission and improves network throughput.
The primary aim of TCP Reno algorithm is to provide a fast and efficient data transfer over congested networks. TCP Reno algorithm is more efficient than TCP Tahoe algorithm. It performs better in case of single packet loss. On the negative side, when multiple packet loss occurs in a single window, fast recovery fails. In case of multiple packet loss, it assumes there is a congestion.
We will cover this algorithm independently in a later chapter of this tutorial.
TCP New Reno Algorithm
TCP New Reno is an improved version of the TCP Reno algorithm. The improved feature of TCP New Reno is its extended fast recovery phase that can handle multiple packet losses within a single window.
On multiple packet losses, it does not exit fast recovery phase after retransmitting single lost packet. It retransmits all lost packets in the same window before returning to congestion avoidance phase. This reduces the data transmission delay. It solves the limitations of TCP Reno of not handling multiple packet loss in same window and improves network throughput.
TCP New Reno algorithm can handle multiple packet losses in a single window. It provides better throughput. On the downside, this algorithm is complex to implement and it suffers from slow recovery when too many packets are lost.
This is just an overview of TCP New Reno; we have covered this algorithm in detail in a later chapter.
TCP Tahoe vs TCP Reno vs TCP New Reno
The following table captures the major differences among TCP Tahoe, TCP Reno, and TCP New Reno algorithms −
| TCP Tahoe | TCP Reno | TCP New Reno |
|---|---|---|
| There isn't any fast recovery phase to handle packet losses. | It has a fast recovery phase to recover from single packet losses. | It has an enhanced/extended fast recovery phase to handle multiple packet losses. |
| It reduces the congestion window to 1 MSS and enters slow start phase. | It does not performs well when multiple losses occur. It exits fast recovery phase after transmitting only single packet loss. | It remains in fast recovery phase until all lost packets are retransmitted. |
| It restarts from 1 MSS after any loss so it recovers slowly. | It recovers fast for single packet loss but slow for multiple losses. | It recovers fast for both single and multiple packet losses in the same window. |
| Less throughput. | Moderate throughput. | Maximum throughput. |
| It is used in networks with low packet loss rates and simple network topologies. | It is used in networks with single packet losses and moderate congestion scenarios | It is used in networks with high packet loss rates. |
Conclusion
Congestion control algorithms are used to avoid, detect, and handle congestion in a network for maintaining the network performance. There are various algorithms that is discussed in this chapter along with their working, advantages and limitations. This chapter covers leaky bucket algorithm, token bucket algorithm, TCP Tahoe, TCP Reno, and TCP New Reno algorithms.