
- Data Comm & Networks Home
- DCN - Overview
- DCN - What is Computer Network
- DCN - Uses of Computer Network
- DCN - Computer Network Types
- DCN - Network LAN Technologies
- DCN - Computer Network Models
- DCN - Computer Network Security
- DCN - Components
- DCN - Connectors
- DCN - Switches
- DCN - Repeaters
- DCN - Gateways
- DCN - Bridges
- DCN - Socket
- DCN - Network Interface Card
- DCN - NIC: Pros and Cons
- DCN - Network Hardware
- DCN - Network Port
- Computer Network Topologies
- DCN - Computer Network Topologies
- DCN - Point-to-point Topology
- DCN - Bus Topology
- DCN - Star Topology
- DCN - Ring Topology
- DCN - Mesh Topology
- DCN - Tree Topology
- DCN - Hybrid Topology
- Physical Layer
- DCN - Physical Layer Introduction
- DCN - Digital Transmission
- DCN - Analog Transmission
- DCN - Transmission media
- DCN - Wireless Transmission
- DCN - Transmission Impairments
- DCN - Multiplexing
- DCN - Network Switching
- DCN - Circuit Switching
- DCN - Packet Switching
- DCN - Message Switching
- Data Link Layer
- DCN - Data Link Layer Introduction
- DCN - Data Link Control & Protocols
- DCN - RMON
- DCN - Token Ring Network
- DCN - Hamming Code
- DCN - Byte Stuffing
- DCN - Channel Allocation
- DCN - MAC Address
- DCN - Address Resolution Protocol
- DCN - Cyclic Redundancy Checks
- DCN - Error Control
- DCN - Flow Control
- DCN - Framing
- DCN - Error Detection & Correction
- DCN - Error Correcting Codes
- DCN - Parity Bits
- Network Layer
- DCN - Network Layer Introduction
- DCN - Network Addressing
- DCN - Routing
- DCN - Routing Table
- DCN - Internetworking
- DCN - Network Layer Protocols
- DCN - Routing Information Protocol
- DCN - Border Gateway Protocol
- DCN - OSPF Protocol
- DCN - Network Address Translation
- DCN - Network Address Translation Types
- Transport Layer
- DCN - Transport Layer Introduction
- DCN - Transmission Control Protocol
- DCN - User Datagram Protocol
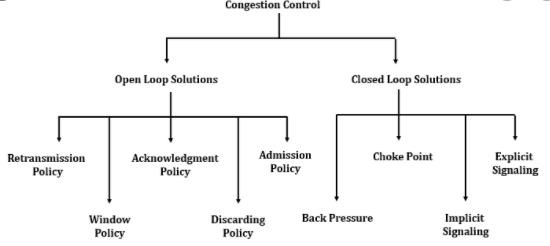
- DCN - Congestion Control
- DCN - Open Loop Congestion Control
- DCN - Closed Loop Congestion Control
- DCN - Congestion Control Algorithms
- DCN - Token Bucket Algorithm
- DCN - TCP Tahoe Algorithm
- DCN - TCP Reno Algorithm
- DCN - TCP New Reno Algorithm
- DCN - TCP BIC Algorithm
- DCN - TCP CUBIC Algorithm
- DCN - TCP Service Model
- DCN - TLS Handshake
- DCN - TCP Vs. UDP
- Application Layer
- DCN - Session Layer
- DCN - Presentation Layer
- DCN - Application Layer Introduction
- DCN - Client-Server Model
- DCN - Application Protocols
- DCN - Network Services
- DCN - Virtual Private Network
- DCN - Load Shedding
- DCN - Optimality Principle
- DCN - Service Primitives
- DCN - Services of Network Security
- DCN - Hypertext Transfer Protocol
- DCN - File Transfer Protocol
- DCN - Secure Socket Layer
- Network Protocols
- DCN - ALOHA Protocol
- DCN - Pure ALOHA Protocol
- DCN - Sliding Window Protocol
- DCN - Stop and Wait Protocol
- DCN - Link State Routing
- DCN - Link State Routing Protocol
- Network Algorithms
- DCN - Shortest Path Algorithm
- DCN - Routing Algorithm
- DCN - Adaptive Routing Algorithms
- DCN - Non-Adaptive Routing Algorithms
- DCN - Leaky Bucket Algorithm
- Wireless Networks
- DCN - Wireless Networks
- DCN - Wireless LANs
- DCN - Wireless LAN & IEEE 802.11
- DCN - IEEE 802.11 Wireless LAN Standards
- DCN - IEEE 802.11 Networks
- Multiplexing
- DCN - Multiplexing & Its Types
- DCN - Time Division Multiplexing
- DCN - Synchronous TDM
- DCN - Asynchronous TDM
- DCN - Synchronous Vs. Asynchronous TDM
- DCN - Frequency Division Multiplexing
- DCN - TDM Vs. FDM
- DCN - Code Division Multiplexing
- DCN - Wavelength Division Multiplexing
- Miscellaneous
- DCN - Shortest Path Routing
- DCN - B-ISDN Reference Model
- DCN - Design Issues For Layers
- DCN - Selective-repeat ARQ
- DCN - Flooding
- DCN - E-Mail Format
- DCN - Cryptography
- DCN - Unicast, Broadcast, & Multicast
- DCN - Network Virtualization
- DCN - Flow Vs. Congestion Control
- DCN - Asynchronous Transfer Mode
- DCN - ATM Networks
- DCN - Synchronous Vs. Asynchronous Transmission
- DCN - Network Attacks
- DCN - WiMax
- DCN - Buffering
- DCN - Authentication
- DCN Useful Resources
- DCN - Quick Guide
- DCN - Useful Resources
- DCN - Discussion
Closed Loop Congestion Control in Computer Network
Network congestion occurs when too many packets are present in a part of the network and the number of incoming packets becomes more than the available resources. Congestion can cause packet delays and packet loss. It can lead to reduced network performance and decreased throughput. Congestion control helps in managing this traffic overload.
There are two main approaches for congestion control: Open loop and Closed loop. This chapter focuses on closed loop congestion control.
What is Closed Loop Congestion Control?
Closed loop congestion control is a congestion recovery method for congestion management. These techniques are designed to detect and handle congestion after it occurs, unlike open loop that prevents congestion in advance.
Characteristics of Closed Loop Congestion Control
Some of the important characteristics of closed loop method are listed below −
- In closed loop congestion control, decisions are made in response to current network conditions. It depends on real-time network state.
- Closed loop techniques use feedback from the network for its current state, unlike open loop congestion control that has no feedback mechanism.
- In closed loop networks, policies are not predefined. They adapt during data transmission based on network conditions. It may change dynamically in response to congestion signals.
Closed loop congestion control is a congestion recovery method to detect and correct congestions after they have occurred.
Closed Loop Congestion Control Techniques
Control policies are applied to detect and correct congestions. It is handled by monitoring network feedback. In this section, let's understand some of the policies of closed loop congestion control −
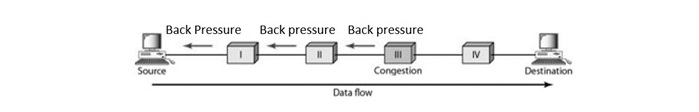
Backpressure
Backpressure is a technique used in virtual circuit networks where a congested node stops accepting packets from upstream nodes. When a node detects congestion, it transfers this information backward to the source, forcing upstream nodes to slow down or stop transmission. It creates a chain reaction that at the end reaches the source.
For example: If a router's buffer is filling up, it can send a signal to the previous router to slow down transmission. This signal propagates backward until it reaches the source. Below is a diagram to demonstrate backpressure.
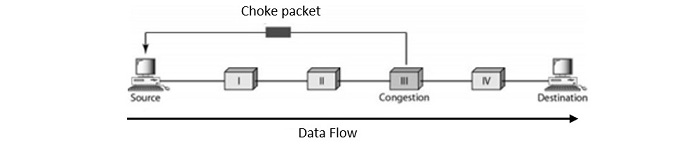
Choke Packet
A choke packet is a special control packet that is sent by a router to source for informing it about congestion. When a router faces congestion, it will send a choke packet to the source, requesting it to reduce its transmission rate.
The source node when receives the choke packet, it reduces its transmission rate. When the congestion is handled, the router stops sending choke packets and the source increase its transmission rate slowly. It involves:
- Congestion Detection − The router monitors its queue length and detects when congestion occurs.
- Choke Packet Generation − On detecting congestion, the router sends a choke packet back to the source.
- Rate Reduction − The source reduces its transmission rate on receiving the choke packet.
Implicit Signaling
In implicit signaling, the source monitors the network behavior to detect congestion without receiving any explicit congestion signal. The source checks for indications such as packet loss, increased delay, or timeout events.
Given below are some common indicators used in implicit signaling −
- Packet Loss − On packet loss, the source assumes congestion and reduces its transmission rate.
- Increased Round Trip Time (RTT) − Longer delays indicate congestion in the network.
- Timeout Events − When the acknowledgments don't arrive and takes more than expected time during data transmission, then it is considered as congestion.
Explicit Signaling
In explicit signaling, routers explicitly send signal to the source or destination about congestion. Routers set special bits in packet headers for indicating congestion. It provides information faster as compared to implicit signaling.
Some of the common explicit signaling mechanisms are mentioned below −
- Explicit Congestion Notification (ECN) − It uses bits in the IP header to signal congestion. Routers mark packets when congestion is detected.
- Forward Explicit Congestion Notification (FECN) − In FECN, congestion information is sent in the forward direction to inform the destination.
- Backward Explicit Congestion Notification (BECN) − In BECN, congestion information is sent in the backward direction to inform the source.
Pros and Cons of Closed Loop Congestion Control
The advantages of closed loop congestion control are listed below −
- It can adapt dynamically to any change in network conditions.
- It utilizes available network capacity efficiently.
- It detects and recovers from congestion automatically.
- It performs better in variable traffic conditions.
Since closed loop congestion control is a reactive method, it responds to real network state instead of predictions.
The limitations of closed loop congestion control are as follows −
- Closed loop congestion control is more complex to design and implement compared to open loop.
- It has higher overhead because of monitoring and feedback mechanisms.
- Delayed response as congestion detection takes time.
Applications of Closed Loop Congestion Control Technique
Closed loop congestion control techniques are used in many networking scenarios. Here are some real-world applications of closed loop congestion control −
- TCP congestion control is fundamental to all internet data transfers including web browsing, file downloads, and email.
- Modern data center congestion control protocols use explicit feedback mechanisms for low latency communication.
- Adaptive bitrate streaming uses closed loop feedback to adjust video quality based on network conditions.
- Cloud applications use congestion control to ensure reliable data transfer between distributed servers and clients.
Difference between Open Loop and Closed Loop Congestion Control
The following table highlights the difference between open and close loop congestion control techniques −
| Open Loop Congestion Control | Closed Loop Congestion Control |
|---|---|
| It uses preventive method to prevent congestion before it occurs. | It uses reactive method to handle congestion after it's detected. |
| It doesn't monitor current network conditions. | It continuously monitors network conditions to adjust the traffic flow accordingly. |
| It does not use any feedback mechanism. | It uses feedback mechanism. |
| It uses static or pre-defined policies. These policies remains fixed during data transmission. | It uses dynamic policies to adapt to real-time change in network conditions. |
| In this, decisions are made during network design or when connection is established. | In closed loop, decisions are made during data transmission based on current network state. |
| It is simple to implement with less overhead. | It is complex to implement with higher overhead since it monitors and has feedback. |
| It may under utilize network capacity. | It has better resource utilization. |
| Examples: retransmission policy, window policy, admission control, and traffic shaping. | Examples: TCP congestion control (like Slow Start, Congestion Avoidance), and Explicit Congestion Notification (ECN) |
| It is used in predictable traffic patterns and for real-time applications. | It is useful in variable traffic patterns. |
| Since it has static policies, it cannot recover from unexpected congestion conditions. | It is adaptive so it can detect and recover from congestion. |
Conclusion
Closed loop congestion control is a reactive method. It implements congestion detection and recovery policies after congestion occurs. It has dynamic policies and can adapt to real-time network conditions using feedback mechanisms.
Closed loop congestion control is more complex to implement with higher overhead as compared to open loop. Closed loop methods are useful in variable traffic patterns and in applications where adaptive performance is important.