- Splunk - Home
- Splunk - Overview
- Splunk - Environment
- Splunk - Interfaces
- Splunk - Data Ingestion
- Splunk - Source Types
- Splunk - Basic Searching
- Splunk - Field Searching
- Splunk - Time Range Search
- Splunk - Sharing and Exporting
- Splunk - Search Language
- Splunk - Search Optimization
- Splunk - Transforming commands
- Splunk - Reports
- Splunk - Dashboards
- Splunk - Pivot & Datasets
- Splunk - Lookups
- Splunk - Schedules and Alerts
- Splunk - Knowledge Management
- Splunk - Subseraching
- Splunk - Search Macros
- Splunk - Event Types
- Splunk - Basic Chart
- Splunk - Overlay chart
- Splunk - Sparklines
- Splunk - Managing Indexes
- Splunk - Calculated Fields
- Splunk - Tags
- Splunk - Apps
- Splunk - Removing Data
- Splunk - Custom Chart
- Splunk - Monitoring Files
- Splunk - Sort Command
- Splunk - Top Command
- Splunk - Stats Command
- Splunk Useful Resources
- Splunk - Quick Guide
- Splunk - Useful Resources
- Splunk - Discussion
Splunk - Basic Search
Splunk has a robust search functionality which enables you to search the entire data set that is ingested. This feature is accessed through the app named as Search & Reporting which can be seen in the left side bar after logging in to the web interface.
On clicking on the search & Reporting app, we are presented with a search box, where we can start our search on the log data that we uploaded in the previous chapter.
We type the host name in the format as shown below and click on the search icon present in the right most corner. This gives us the result highlighting the search term.
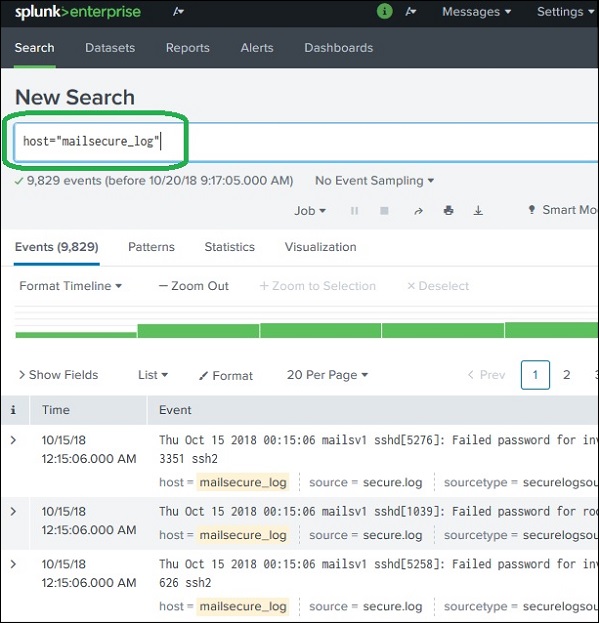
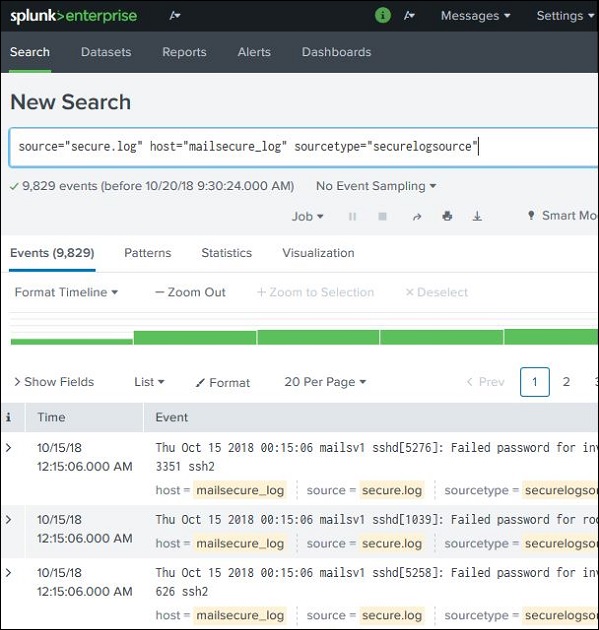
Combining Search Terms
We can combine the terms used for searching by writing them one after another but putting the user search strings under double quotes.
Using Wild Card
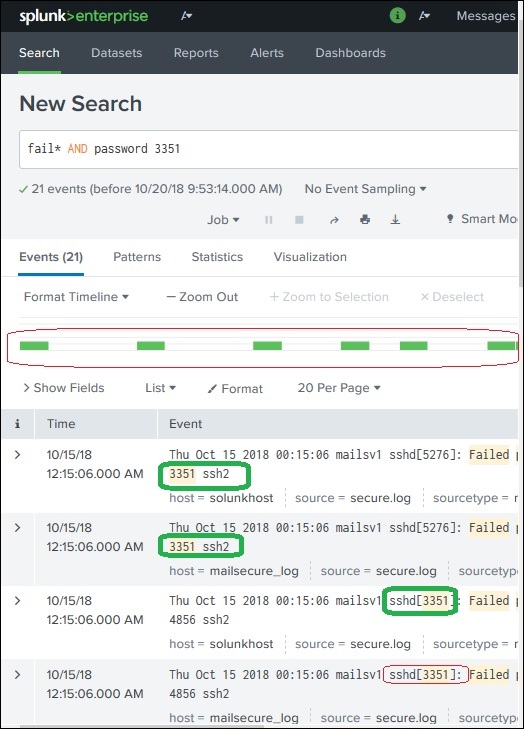
We can use wild cards in our search option combined with the AND/OR operators. In the below search, we get the result where the log file has the terms containing fail, failed, failure, etc., along with the term password in the same line.
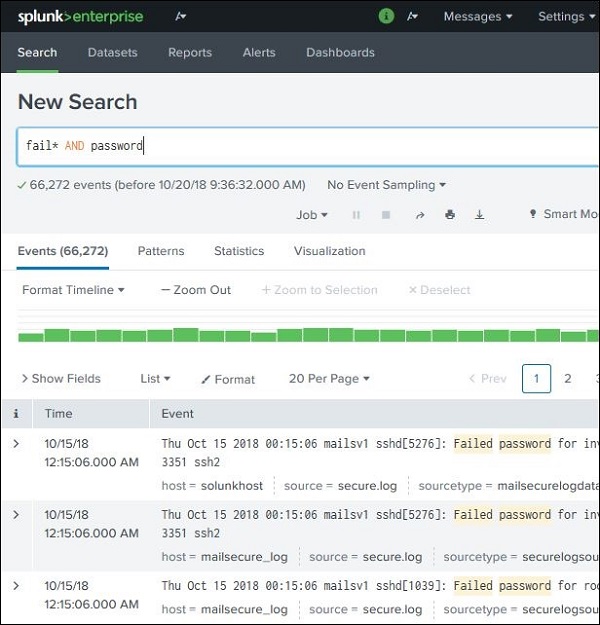
Refining Search Results
We can further refine the search result by selecting a string and adding it to the search. In the below example, we click over the string 3351 and select the option Add to Search.
After 3351 is added to the search term, we get the below result which shows only those lines from the log containing 3351 in them. Also mark how the time line of the search result has changed as we have refined the search.