
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - Triple DES (Data Encryption Standards)
The speed of exhaustive key searches against DES after 1990 began to cause discomfort amongst users of DES. However, users did not want to replace DES as it takes an enormous amount of time and money to change encryption algorithms that are widely adopted and embedded in large security architectures.
The pragmatic approach was not to abandon the DES completely, but to change the manner in which DES is used. This led to the modified schemes of Triple DES (sometimes known as 3DES).
It should be noted that there are two versions of Triple DES: 2-key Triple DES (2TDES) and 3-key Triple DES (3TDES).
What is Triple DES?
Triple Data Encryption Algorithm, often known as Triple DES, TDEA and 3DES is an encryption method that encrypts a single piece of text using three separate versions of DES. In the first, each key used is unique; in the second, two keys are same and one is different; and in the third, every key is similar. These are the different key selecting methods that are used.
Triple DES was first introduced in 1998. For a longer effective key length, it runs the DES cipher algorithm three times over each data block.
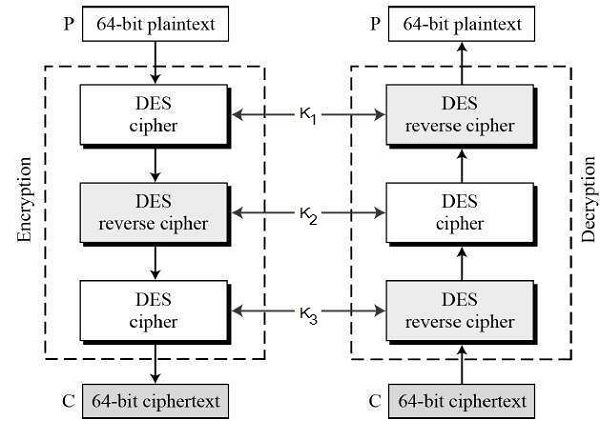
Encryption Process of Triple DES
- The three stages of Triple DES operation are Encrypt-Decrypt-Encrypt (EDE). It functions by using a key bundle, made up of three 56-bit keys (K1, K2, and K3).
- Initially K1 is used for encryption; K2 is then used for decryption; and K3 is used for the final encryption. There is a two-key Triple DES version where K1 is used for the first and end steps but the same algorithm is done three times. In 2015, this two-key version was discontinued.
- Because of the limitation to use double enciphering, the algorithm is executed three times. Meet-in-the-middle attacks are a type of attacks that encrypt from one end, decrypt from the other, and search for collisions, or keys resulting in the same outcome in both directions. Double DES, or any other cipher run twice, would only be twice as strong as the base cipher if memory were enough.
- In simple terms, the double cipher is going to have a shorter key and be equally powerful as the identical cipher run once.
- Not only this, but encrypting twice with two keys is equivalent to encrypting once with an alternate key if the cipher combines together. However determining the other key is not simple, using every single key in a brute-force attack will result to the discovery of the third key.
- So multiple encrypting is a waste of time if the cipher is a group.
- An operator and a set have a connection known as a group. They form a group if their behaviour with addition is nearly the same as that of integers.
- A group is also formed if you continue to encrypt a block and it finishes a full circuit over the set of potential blocks.
- DES does not belong to a group. But DES has popular structural characteristics that lead some to maintain that it's not definitely not a group, in other words, it can be a group.
- For example, there are known DES loops in which you can get stuck in an indefinite loop by continuously encrypting with the same key.
Encryption Modes
Triple DES allows the DES algorithm to be used in each of the three rounds in either direction, for encryption or decryption. As a result, Triple DES has eight different possible modes.
| Mode | Encryption Sequence |
|---|---|
| DDD | Decrypt-Decrypt-Decrypt |
| DDE | Decrypt-Decrypt-Encrypt |
| DED | Decrypt-Encrypt-Decrypt |
| DEE | Decrypt-Encrypt-Encrypt |
| EDD | Encrypt-Decrypt-Decrypt |
| EDE | Encrypt-Decrypt-Encrypt |
| EED | Encrypt-Encrypt-Decrypt |
| EEE | Encrypt-Encrypt-Encrypt |
If there was a better choice, you are unlikely to want to use EEE or DDD mode for the same structural reasons that you could not want to use EED, DEE, DDE, or EDD. The most effective compositions are EDE or DED due to the weak nongroupness of DES. EDE additionally makes more sense. You have to clarify how Triple DES begins with decryption if you decide to use DED.
Modules of Triple DES
There are some modules of Triple DES which are as follows −
- Admin Login − In this project, admin can get in the username and password to validate himself to access the account panel modules.
- User Login − In this module, users can get in their username and password to authenticate themselves to access their account panel modules.
- User Registration Module − In this module, users can get in their username and password and address, mobile, email id to register themselves to access the account panel modules.
- Create Message Module for Admin − In this module, admin can choose the username and then enter the message along with the subject and also the input encryption key which can be used for encrypt the message and the subject and then send it to the selected user and message and subject are both saved into the user inbox.
- Check Suspicious Mails for Admin − In this module, admin can verify the suspicious mails which is not generally stored into the user inbox rather than marked as suspicious status and sent it to the admin as suspicious mails with the user element.
- Data Dictionary for Admin − In this module, admin can add the suspicious words into current data dictionary to detect more directly and efficiently the suspicious mails sent by the users.
- View Data Dictionary for Admin − In this module, admin can see the suspicious words exists into the data dictionary and also has access to remove the suspicious words from the current data dictionary of suspicious words.
- View Users List for Admin − In this module, admin can see the registered users and their full element and has access to remove the users if any of the registered users are discovered to do the suspicious event on the website.
- Create Message Module for Users − In this module, users can choose the other users and then enter the message forward with the subject and then send it to the selected user and message and subject are both saved into that inbox of taking user and at back end of the website. Suspicious mail detection module is processed which is identified the sent mails marked as suspicious or normal.
- Inbox Module for Users − In this module, users can see the inbox messages which are sent by the users those who are already registered if the user is any registered user then this message will be checked without any decryption module and also has access to remove that mail.
Security of Triple DES
The Triple DES method uses keys to encrypt data in order to secure it. Triple DES can be used in two different ways. The first method must be highly secure because it uses three different keys. It is not as safe as we figured out, however, due to a manner in which attackers can get in. It is similar to a door having three locks on it, but an attacker can still get in easily.
The second approach is weak because one of the keys is the same as the first. Think it as if a door had two locks, just one of which is simple to open. Because of this, it is no longer recommended to use because it is not very secure.
Also, there is an issue with Triple DES when multiple pieces of data are secured by the same key. This is similar to having a too short code, which makes it easy for someone to decipher. The problem exists in TLS and OpenVPN systems.
Triple DES is no longer advised because to these problems, and it is no longer present in more recent iterations of security programs like OpenSSL.
Advantages
Here are some advantages of the Triple DES −
- As compared to the triple-layered encryption to the original DES, security is enhanced.
- 3DES allows for smooth migrations through preserving connectivity with current DES implementations.
- By setting each of all three keys to the same value, 3DES can be used for a single DES with respect to backward compatibility.
- 3DES is widely used and integrated with a wide range of hardware, protocols, and applications.
Disadvantages
Below are some disadvantages of Triple DES which we have to consider while using it −
- The slower speed of 3DES compared to recent encryption methods like AES decreases processing efficiency.
- Even while 3DES is more powerful than DES, its efficient key length is limited, especially if three 56-bit keys are used.
- In scenarios with limited resources, the triple encryption process reduces performance because it needs more computing power.
- 3DES has a lower security margin than more recent encryption methods like AES, but being more secure than DES.
Implementation of Triple DES
The following applications can secure data with Triple DES −
Botan, Bouncy Castle, cryptlib, Crypto++, Libgcrypt, Nettle, OpenSSL, wolfSSL, Trusted Platform Module (TPM).
But keep in mind that in their most recent revisions, some of these programs may not have Triple DES as a default option. It is important that you confirm its availability in the particular version you are using.