
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - Traditional Ciphers
Traditional ciphers encode messages in a way that only those with the secret key can decode it. Throughout history, it has been used for private communication.
These ciphers were used extensively before the advent of modern computer encryption techniques. Although relatively simple, when used properly, it can also be effective and provide interesting insights into the history of encryption.
Here are a few common types −
Caesar Cipher
Vigenere Cipher
Simple Substitution Cipher
Monoalphabetic and Polyalphabetic Cipher
Transposition Cipher
Playfair Cipher
Earlier cryptographic systems
Before proceeding further, you should know some facts about cryptographic systems −
These systems are all built using symmetric key encryption.
These systems simply offer information confidentiality as a security feature.
In comparison with modern digital systems that handle data as binary numbers, previous systems used alphabets as the basic building block.
These early cryptography schemes are also called Ciphers. In general, a cipher is simply the steps (algorithms) that can be used to perform encryption, and the corresponding decryption.
Now let us discuss the above types of Tranditional Ciphers one by one.
Caesar Cipher
Caesar cipher is a type of substitution cipher in which every letter in the given plaintext is shifted with a certain number of places down or up the alphabet. The shift number is called the key. It is create by Julius Caesar. It is believed that this cipher is to communicate secretly with his generals.
For this type of method both the sender and the receiver should agree on a 'secret shift key' for shifting the alphabet of the given plaintext. The number which can be between 0 and 25 is the key of encryption.
This techniques sometimes used to describe the Shift Cipher when the 'shift of three' is used.
For example - If plaintext is shift of 4:
'A' will become 'E'
'B' will become 'F'
'C' will become 'G'
and so on...
The Caesar cipher is a very simple and easy to understand encryption method. But it is also very easy to break as there are only 25 possible keys which is easy to guess using brute force.
Vigenere Cipher
Vigenere is also a traditional cipher algorithm which uses a text string (Let us say a word) as a key. Then it is used for shifting a number of shifts on the given plaintext.
For example − let us say the key is 'tutor'. In this each alphabet of the key is changed to its respective numeric value: In our case,
t → 20, u → 21, t → 20, o → 15, and r → 18.
Thus, the key is: 20 21 20 15 18.
Vigenere Cipher Steps
First the sender and the receiver decide a key. Let us say the key is 'tutor'. So '20 21 20 15 18' is the Numeric representation of this key.
Now the sender will encrypt the message. And the message is 'This is ethical hacker'. Then it will be arranged as numeric key as follows −

Now we will each plaintext letter by the number written in below the letter:
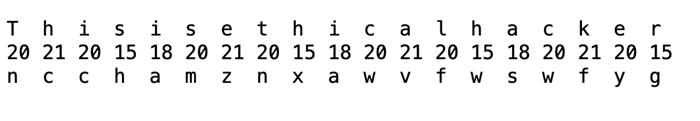
In the above image, every letter of the plaintext is shifted by a different amount and that amount is found by the key. The key should be less than or equal to the size of the message.
In the decryption process, the receiver will use the same key and shifts received cipher text in opposite order to get the plaintext.
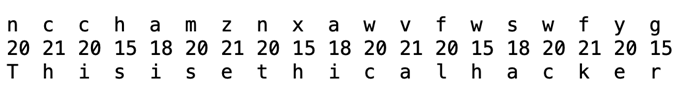
The Vigenere Cipher is designed to tweak the standard Caesar cipher to reduce the efficiency of cryptanalysis on the ciphertext and increase the robustness of the cryptosystem It is much more secure than a regular Caesar cipher.
Throughout history, it was regularly used to protect important political and military information. It is described as an unbreakable cipher due to the difficulty of dividing the secret.
The Vigenere cipher − has two main points
The length of the keyword is the same as the plaintect message. This statement is called varnam cipher. This is more secure than the standard Vigenere cipher. The Vigenere cipher would be a cryptosystem with complete privacy, called a One-time pad.
Simple Substitution Cipher
Simple substitution cipher is a form of encryption in which the letters in Plaintext is replaced by another character in cipher text according to a fixed order. In other words it is a method of encoding with any letter and characters are mapped to other characters.
For example, in Simple Substitution Cipher −
'A' can be replaced by 'X'
'B' can be replaced by 'K'
'C' can be replaced by 'Q'
So on... until each character in the alphabet is replaced by another one.
The key to decrypting a message is knowing the substitution model used. These ciphers are relatively easy to use, but can be break by frequency analysis which requires analyzing the frequency of the characters in the cipher text and removing the mapping.
The simple alternative cipher is a vast improvement over the Caesar cipher. The number of possible keys is enormous (26!) and even modern computer systems do not yet have the ability to comfortably perform brute force attacks to crack the system However, a simple alternative cipher has a simple and common structure system flaws, say choose obvious changes.
Monoalphabetic and Polyalphabetic Cipher
A Monoalphabetic cipher is a type of substitution cipher in which fixed characters are always replaced in the ciphertext which means that every character in the plaintext is always replaced by the same corresponding character in the ciphertext. The replacement remains constant throughout the encryption process.
For example, if 'A' is replaced by 'E' in the encryption process, any occurrence of 'A' in plain text will be replaced by 'E' in ciphertext and if 'B' is replaced by 'F'. replace 'any B ' in plaintext with 'F' in ciphertext.
A Polyalphabetic Cipher is a type of substitution cipher in which plaintext characters are replaced by ciphertext characters varying with the encryption process. This means that characters in the plaintext can be replaced by characters in the ciphertext, depending on the encryption key and the position of the character in the plaintext.
The most popular Polyalphabetic Cipher is the Vigenaire cipher, where the encryption key determines where the letters will be located in the ciphertext. Unlike single-letter ciphers, Polyalphabetic Cipher are more secure because they introduce changes to the encryption scheme, making frequency analysis and other attacks more difficult.
Transposition Cipher
This is a new type of cipher in which the sequence of letters is rearranged in plain text to create ciphertext. They are not replaced by actual plaintext.
An example is a simple column substitution cipher in which simple increments are written in a specific alphabet width. The ciphertext is then read directly as indicated.
For example, the plain text is "The tajmahal is in agra" and the randomly chosen hidden key is Four. We format this text directly in a table with a number of columns including key value. The resulting text is shown below.
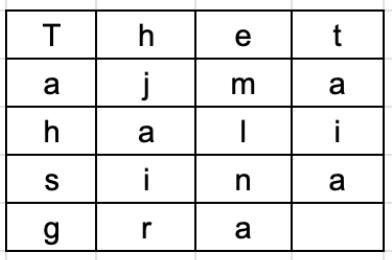
So now we can get the ciphertext just reading columns from first to last by vertically downward. And the ciphertext will be 'Tahsghjairemlnataia'.
Playfair Cipher
The Playfair cipher uses a 5x5 grid of letters unless it is double and usually 'J' for encryption. Messages are encrypted by pairing letters and using rules: if on the same letter, turn right; If it is in one column, turn down; If there are rows and columns, make a triangle and replace them with opposite corners. Decryption follows the opposite rule. Playfair encrypts character pairs, making it more secure than single-character ciphers, but still vulnerable to an attack.