
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - Data Encryption Standard
The DES which stands for Data Encryption Standard algorithm, is a symmetric key block cipher created by an IBM team in the early 1970s and some time later it is adopted by the National Institute of Standards and Technology. In this method we divides plaintext into 64-bit blocks and transforms it to ciphertext with the help of 48-bit keys.
As you may know, it is a symmetric-key method, it uses the same key to encrypt and decrypt the data which we have already discussed in the previous chapter. If it were an asymmetrical algorithm, it will require different keys for encryption and decryption.
Some systems can break the DES algorithm. This algorithm uses a 56-bit key. DES uses this key to convert a block of 64-bit plaintext into a block of 64-bit ciphertext.
The DES process has several steps, each of which is referred to as a "round." The number of rounds vary depending on to the size of the key we have used. For example, a 128-bit key takes 10 rounds, a 192-bit key takes 12 rounds, and so on.
History of DES Algorithm
DES is based on the LUCIFER Feistel block cipher, which was invented in 1971 by IBM cryptography researcher Horst Feistel. DES uses 16 rounds of the Feistel structure, with each round using a unique key.
In November 1976, DES was approved as the government encryption standard, which was later reaffirmed in the years 1983, 1988, and 1999.
After a public competition to develop a replacement, the Advanced Encryption Standard (AES) took over as the acknowledged standard in 2002, ending DES's monopoly. In May 2005, the NIST officially revoked FIPS 46-3 (the 1999 reaffirmation), however Triple DES (3DES) is still allowed for sensitive government information until 2030.
Types/Variations of DES
There are two main variations of Data Encryption Standard are as follows −
Double DES
Double DES is a type of encryption in which two instances of DES must be present in the same plaintext. In both scenarios, the plaintext is encrypted with the help of a number of keys. For the purpose of decryption, both keys are required.
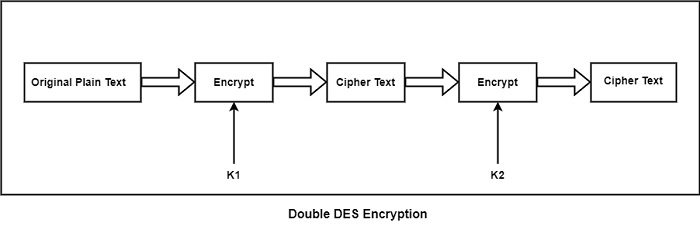
Triple DES
There are two types of Triple DES which are as follows −
Triple DES with Two Keys − In triple DES with two keys there are only two keys K1 used by the first and third process and K2 used in the second process.
Triple DES with Three Key − In Triple DES, the plaintext block P is first encrypted with a key K1 then encrypts with a second key K2 and finally with a third key K3 where K1, K2, and K3 are distinct from each other.
Structure of DES
DES uses 16 round Feistel structure. The block size is 64-bit. Though, key length is 64-bit, DES has an effective key length of 56 bits, since 8 of the 64 bits of the key are not used by the encryption algorithm (function as check bits only). General Structure of DES is depicted in the following illustration −

As DES is based on the Feistel Cipher, all that is required to specify DES is −
- Round function
- Key schedule
- Any additional processing - Initial and final permutation
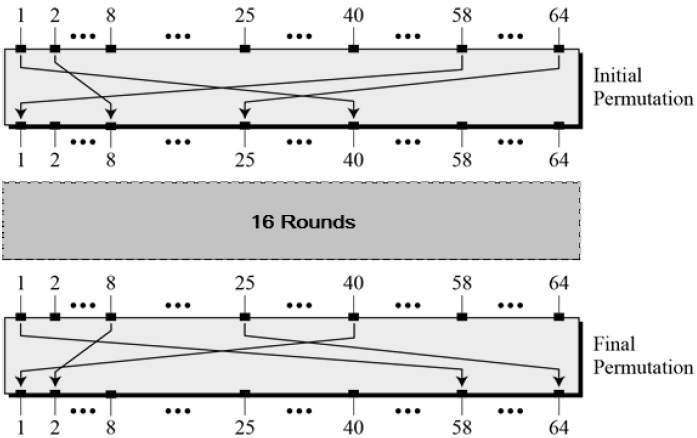
Initial and Final Permutation
The initial and final permutations are straight Permutation boxes (P-boxes) that are inverses of each other. They have no cryptography significance in DES. The initial and final permutations are shown as follows −
Round Function
The heart of this cipher is the DES function, f. The DES function applies a 48-bit key to the rightmost 32 bits to produce a 32-bit output.
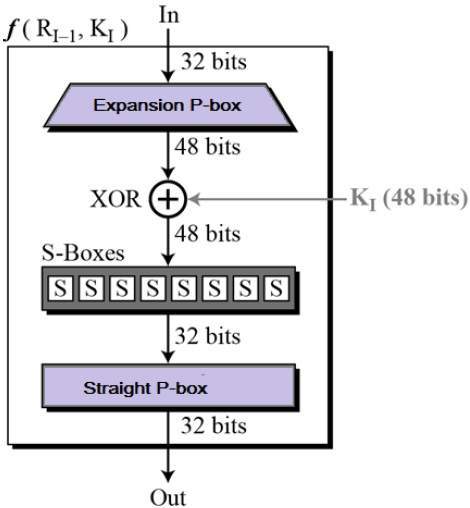
Now let us discuss the above image and its terminologies −
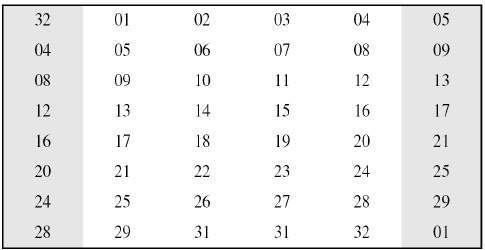
- Expansion Permutation Box − Since right input is 32-bit and round key is a 48-bit, we first need to expand right input to 48 bits. Permutation logic is graphically depicted in the following illustration −
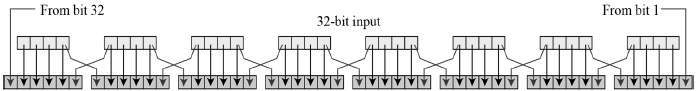
- The graphically depicted permutation logic is generally described as table in DES specification illustrated as shown −
- XOR (Whitener) − After the expansion permutation, DES does XOR operation on the expanded right section and the round key. This is the only type of operation that uses the round key.
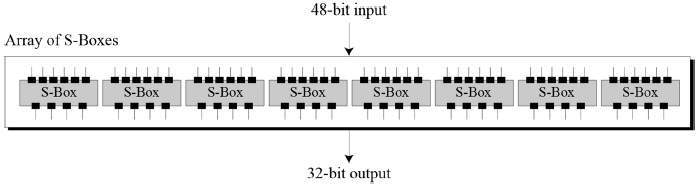
- Substitution Boxes − The S-boxes carry out the real mixing (confusion). Eight S-boxes, each with a 6-bit input and a 4-bit output, are used in DES. Refer the following illustration −
- The S-box rule is illustrated below −
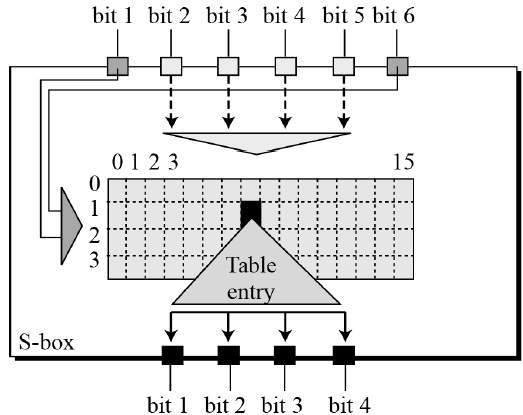
- There are a total of eight S-box tables. The output of all eight s-boxes is then combined in to 32 bit section.
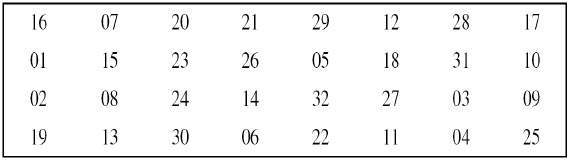
- Straight Permutation − The 32 bit output of S-boxes is then subjected to the straight permutation with rule shown in the following illustration −
Algorithm of DES
The following steps define the algorithm process −
- Step 1 − The 64-bit plaintext block is initially provided to an initial permutation (IP) function to start the process.
- Step 2 − After that, the plaintext undergoes to the initial permutation (IP).
- Step 3 − The first permutation (IP) then generates Left Plain Text (LPT) and Right Plain Text (RPT), which are the two sides of the permuted block.
- Step 4 − The encryption procedure consists of sixteen cycles for each LPT and RPT.
- Step 5 − Lastly, the LPT and RPT become one, and the newly combined block is subjected to a Final Permutation (FP).
- Step 6 − This procedure yields the intended 64-bit ciphertext.
Step 4 of the encryption process can be further divided into five stages − Key transformation, Expansion permutation, S-Box permutation, P-Box permutation, XOR and swap.
We apply the same process for decryption, with the exception we reverse the of 16 round keys.
Next, we will explore the several DES modes of operation to get a better understanding of what DES is.
Key Generation
The round-key generator creates sixteen 48-bit keys out of a 56-bit cipher key. The process of key generation is depicted in the following illustration −
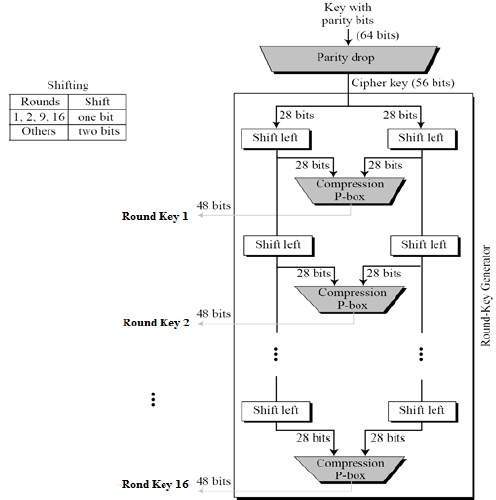
The algorithm implement 16 rounds of encryption and for each round, a unique key is produced. Before transforming to the steps, it is essential to understand that in plaintext the bits are labeled from 1 to 64 where 1 is the most significant bit and 64 is the least significant bit. The process of generating keys are as follows −
- The round key generator produce sixteen 48-bit keys out of a 56-bit cipher key. The cipher key is provided as 64 bit key in which 8 extra bits are parity bits, which are discarded before the actual key generation process begins.
- The parity bit drop process drops the parity bits (bit 8, 16, 24, 32...64) from the 64-bit key and permutes the remaining bit according to the pre-defined rules as display in the parity bit drop table below.
- These remaining 56 bits are generally used for key generation.
- After the permutation, the keys are divided into two 28 bits parts. Each part is changed left one or two bits is depend on the rounds.
- In round 1, 2, 9, and 16 shifting is one bit and in the other rounds it is two bits. The two parts are integrate to build a 56 bit part.
- Thus the compression D-box transform it into 48 bit. These 48 bits are being utilized as a key for a round.
The logic for Parity drop, shifting, and Compression P-box is given in the DES description.
DES Analysis
The DES satisfies both the desired properties of block cipher. These two properties make cipher very strong.
- Avalanche effect − The ciphertext changes significantly in reaction to even minor changes in the plaintext. It can change in one bit of plaintext creates change in some bits of the ciphertext. The advantage of Avalanche effect can be made accessible in securing embedded software wherever DES and AES algorithms are used. The attackers are attempting a lot to smuggle the data saved in the databases.
- Completeness − Completeness effect defines that each bit of the ciphertext required to base on some bits on the plaintext. The diffusion and confusion developed by Dboxes and S-boxes in DES, show a very strong completeness effect. The completeness feature tightness the avalanche concept even more. It needed that change in the ciphertext is consistently distributed for each changed bit of the input plaintext or the key.
During the last few years, cryptanalysis have found some weaknesses in DES when key selected are weak keys. These keys shall be avoided.
DES has proved to be a very well designed block cipher. There have been no significant cryptanalytic attacks on DES other than exhaustive key search.
DES Strength
The strength of DES is as follows −
Use of 56 bit keys − A 56-bit encryption key provides 256 possible keys, making brute force attacks impossible due to the vast number of combinations. Even with a machine performing one DES encryption per microsecond, it would take thousands of years to decrypt the cipher.
Diffie and Hellman suggested the feasibility of a parallel machine with one million encryption units, each capable of one encryption per microsecond. However, decrypting messages may require more than just trying all possible keys, especially if the message is in English plaintext, which can be identified easily. If the text is compressed before encryption, decryption becomes more challenging.
The nature of algorithm − Cryptanalysts can conduct cryptanalysis on the DES algorithm by exploiting its features. They focus on weaknesses in the eight substitution tables, or S-boxes, used in each iteration. While researchers have discovered many regularities and unexpected behaviors in the S-boxes, no one has yet found weaknesses in them.
This ongoing pursuit has led to the identification of numerous irregularities and unexpected behaviors in the S-boxes over the years.
Timing Attacks − A timing attack is a security exploit within a broader class known as side-channel attacks, where an attacker measures the response time of a system to different inputs to extract sensitive data. Kocher designed a timing attack specifically targeting RSA decryption secret keys, primarily used in hardware security tokens like smartcards.
These attacks focus on public key algorithms, extracting information about keys or plaintexts by observing decryption times of multiple ciphertexts. To mitigate timing attacks, techniques like "blinding" are used to ensure consistent computation times regardless of the key or message being processed.
Advantages of DES
The DES method's advantages are −
- The US authority has set it as a standard.
- It works on hardware faster than it does on software.
- Triple DES utilises a highly difficult-to-break 168-bit key.
Disadvantages of DES
The drawbacks or disadvantages of DES are as follows −
- It is an algorithm with weak security.
- It can be break using Brute force attacks.
- There is a DES breaking device on the market called Deep Crack.
Attacks on DES
There are various attacks on DES which are as follows −
Differential Cryptanalysis − The main objective of differential cryptanalysis is to view for statistical distributions and patterns in ciphertext to provide deduce element about the key used in the cipher.
Differential cryptanalysis is a section of study in cryptography that compares the method differences in input associated to the differences in encrypted output. It can be used basically in the study of block ciphers to decide if changes in plaintext result in any non-random outcomes in the encrypted ciphertext.
Related-Key Cryptanalysis − Related-key cryptanalysis consider that the attacker understand the encryption of specific plaintexts not only under the original (unknown) key K, but also below some derived keys K0 = f (K).
In a chosen-related key attack, the attacker defines how the key is to be modified and known-related-key attacks are those where the key difference is acknowledged, but cannot be selected by the attacker.
It can emphasize that the attacker understand or select the relationship between keys, and not only the actual key values.
Related-key cryptanalysis is a factual attack on key-exchange protocols that do not provide key-integrity an attacker can be capable to ip bits in the key without understanding the keypad key-update protocols that update keys utilizing a known function such as K, K + 1, K + 2, etc. Related-key attacks were also utilized against rotor devices such as operators consistently set rotors incorrectly.
Linear Cryptanalysis − Linear cryptanalysis is a general form of cryptanalysis depend on discovering affine approximations to the element of a cipher. Attacks have been produced for block ciphers and stream ciphers. Linear cryptanalysis is one of the two most generally used attacks on block ciphers and the other being differential cryptanalysis.
Linear approximate equations is depend on the best (n-2) round expression, and dependability of the key candidates changed from these equations. The former decrease the number of needed plaintexts, whereas the latter enhance the success rate of the attack.
Brute Force Attack − In cryptanalysis, a brute force attack is an approach of defeating a cryptographic scheme by attempting a huge number of possibilities.
For example, it can be exhaustively working through all possible keys in order to decode a message. The selection of an appropriate key length based on the practical feasibility of implementing a brute force attack.
For symmetric-key ciphers, a brute force attack generally means a brute-force search of the key area; that is, checking all possible keys in order to find the plaintext used to create a specific cipher text.
In a brute force attack, the expected number of trials before the proper key is discovered is similar to half the size of the key space. For instance, if there are 264 possible keys, a brute force attack can generally be normal to discover a key after 263 trials.
Factors Affecting Security of DES
There are some factors which affects the security of DES is as follows −
Weak Keys − Because of the method the initial key is changed to receive a subkey for each round of the algorithm, specific initial keys are weak keys. The initial keys value is divided into two halves and each half is changed independently.
If all the bits in each half are either 0 or 1, thus the key can be used for some cycle of the algorithm is the same for all the cycles of the algorithm. This can appear if the key is completely 1s, completely 0s, or if one half of the key is completely 1s and the other half is completely 0s. So that creates DES less secure.
Algebraic Structure − The DES encryption operation can form a group, and encrypting a group of plaintext blocks with k1 followed by k2 can be equal to encrypting the blocks with k3.
Even worse, DES can be vulnerable to a meet-in-the-middle known-plaintext attack that runs in only 228 steps. If DES were closed then for any k1 and k2 there would be a k3 such that −
Ek2(Ek1(P))=Ek3(P)
Key Length − If there is a possibility to speed up the searching procedure by timespace tradeoff. The possibility of calculating and saving 256 possible results of encrypting an individual plaintext block under each possible key and then to break an unknown key, and it is required to add data blocks into the encryption stream, recover the resulting cipher text and view the key up.
No. of Rounds − No of rounds kept 16 because reduced number of rounds has been strongly attacked. DES with three or four rounds was simply broken .DES with any number of rounds fewer than 16 can be broken with a known plaintext attack more effectively than by a brute-force attack.
Testing and Implementing DES
Implementing DES needs a security provider. Choosing a supplier is an essential first step in the process of implementation, even if there are multiple choices. The language that you work in, like MATLAB, Java, Python, or C, can have an impact on the choice you make.
After choosing a provider, you have to decide whether to build the key that the Key Generator will produce at random using a byte array or plaintext.
Testing the encryption is also important for making sure that it is being used correctly.
Design Issues of DES
Design issues in DES include S-Boxes, D-Boxes, and the number of rounds.
- S-Boxes are used to substitute 48-bit inputs into 32-bit outputs, adding non-linearity and complexity to the encryption process. They follow specific properties such as permutations within rows and non-affine transformations.
- D-Boxes, similar to transposition ciphers, permute input bits from one round to the next, ensuring each S-box input comes from a different S-box output and avoiding repetition within rounds.
- DES employs sixteen rounds of Feistel ciphers, but it's been shown that after eight rounds, each ciphertext becomes a function of every plaintext and key bit, indicating sufficient security.