
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptosystems - Brute Force Attack
What is the Brute Force Attack?
Brute force attacks are hacking strategies that use trial and mistakes to crack passwords, login credentials and encryption keys. It is a easy but dependable way to benefit unauthorized get entry to non-public accounts and organizations systems and networks. The hacker tries multiple usernames and passwords, often using a computer to try multiple connections, until he finds the correct login information.
The name "brute force" comes from attackers who use extreme force to try to gain access to users' accounts. Despite older methods of cyber-attack, phishing attacks are tried and tested, and remain a favorite method for hackers.
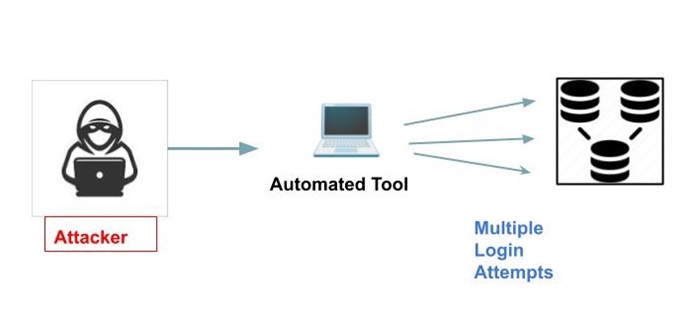
How does a brute force attack work?
The process of brute force attacks includes an automated or manual trial and error technique, wherein the attacker uses a combinations of letters, numbers and logos to guess accurate authentication information.
Target selection − The attacker selects the target system or account he wants to gain access to. This could be a website, email account, network server, or other system that requires authentication.
Password generation − The attacker generates passwords in an attempt to counter the target. This can be done manually by setting up the passwords that can be entered, or automatically using software tools that can generate passwords and test them at high speed.
Password testing − The attacker begins testing each created password against the target system. This can be accomplished via the system's login page or authentication method. If the password is wrong, the attacker proceeds to the next phase. If everything is right, you will be granted access to the system or account.
Iterations − The process continues until the attacker determines the proper password or has exhausted all available possibilities. Depending on the complexity of the password and the speed of the attacker's equipment, this system can take seconds to days or even longer.
Access − If an attacker well guesses the password, they may gain unauthorized get admission to to the targeted gadget or account.They can then execute hostile behaviors to steal resources or undermine system security by stealing important information.
Brute force attacks are often used as a last resort when other methods of gaining access, such as exploiting vulnerabilities or social engineering, fail and are often automated to accelerate the process there to win is the big one. But because of the number of possible combinations, force attacks can be time-consuming and resource-intensive, especially for systems with strict security measures in place.
Types of Brute Force Attacks
Brute force attacks can take different forms depending on the target and the specific security mechanisms in place. Here are some common brute force attacks.
Password Brute Force − This is the weakest form of brute force attack. the attacker systematically tries every possible combination of characters until a valid password is found. This can be done manually, but it's limited to software tools that can run fast and test thousands or millions of passwords per second. Password brute force attacks are often used against login pages on websites, email accounts, or other systems that require authentication.
Credential stuffing − In this type of attack, the attacker uses a listing of username and password pairs acquired from previous information breaches or leaks. They then attempt those combinations in opposition to various on-line services or web sites, hoping that some customers have reused their credentials across more than one money owed. Since many human beings use the identical password for one of a kind money owed, credential stuffing can be quite successful in gaining unauthorized access to numerous bills.
Dictionary attacks − Instead of testing every combination of characters, dictionary attacks rely on a random list of common words, phrases, or phrases . Using a dictionary enables an attacker to significantly reduce the number of attempts needed to guess a password, since only the entries in a list have to be looked up. Dictionary attacks tend to be more efficient than they are used aggressively, especially when users choose a word that is easy or easy to guess.
Reverse brute force attack − In a reverse brute force attack, the attacker already has a specific password in mind and tries to find out a username or account associated with it This is in contrast to traditional brute force attacks, where in which the attacker tries passwords starting with the username. Reverse brute-force attacks are rare but can be used in situations where the attacker has obtained the password through other means, such as social engineering or a data breach, and wants to know what accounts he has on it.
Hybrid brute force attack − A combination of a dictionary attack and a simple brute force attack. an attacker uses two methods to identify a login account, starting with a known username. Using a list of possible words to test combinations of letters, letters, and numbers.
Each brute force attack has its own advantages and limitations, attackers can choose the most appropriate strategy based on their target system and security policy but all brute force attacks have the same goal of gaining unauthorized access through a system that they will speculate or try combinations until they succeed.
Notable Brute Force Attacks
There have been many notable threat attacks over the years, targeting systems and organizations. Here are a few examples −
LinkedIn − Hackers breached the famous commercial enterprise networking online website LinkedIn and stole 6 million person passwords in 2012. Attackers used a combination of brute force and dictionary attacks to crack passwords. As a result, LinkedIn needed to reset affected user passwords and implement robust secrutiy features to prevent brute force attacks.
Sony PlayStation Network (PSN) − A security breach on the Sony PlayStation Network peaked in 2011 affecting more than 77 million users with personal information, including usernames and a use including passwords. The breach resulted in massive outages for PSN and significant damage to Sony's reputation.
WordPress − Over the years, WordPress, a well-known content management system (CMS), has been the victim of numerous brute force attacks. In an attempt to take over a WordPress website, attackers often target these sites and attempt to guess the admin password. Large botnets are sometimes used for malicious attacks, causing severe damage WordPress websites.
These are just a few examples of notable malicious attacks, but they let us know the widespread impact and possible consequences of such a security breach. Organizations should implement strong security measures, including password, including strong policies and multifactor authentication, to protect against brute force attacks and other security threats.
Objective of Hackers
Hackers use brute force attacks for getting unauthorized access to systems, accounts, or sensitive data. The particular objectives and benefits of these attacks differ depending on the target and attacker's goals.
Here are some most common objectives of hackers using in brute force attacks −
Unauthorized Access − The primary goal of many malicious attacks is to gain unauthorized access to systems, accounts, or networks. Hackers can systematically guess passwords and target user accounts, employee accounts, or sensitive databases until they find the right one. Once they gain access, hackers can steal sensitive information, alter data, or do other malicious things.
Data Theft − Hackers can execute brute force attacks intent on stealing valuable data, such as personal information, financial records, or intellectual property Gaining unauthorized access to systems or databases provides attackers can extract sensitive data for purposes such as identity theft, financial fraud, or espionage.
Exploitation − In some cases, hackers can conduct brutal attacks to exploit resources or vulnerabilities in targeted systems. For example, attackers can try to gain access to a web server or cloud infrastructure to host malicious content, send spam emails, or launch distributed denial-of-service (DDoS) attacks against other targets
Credential Stealing − Another target of a malicious attack is credential stealing, where attackers use stolen or exposed credentials to gain unauthorized access to multiple accounts on different platforms or services Hackers using a username and password types derived from analyzing existing data breaches Accounts can be compromised with a number of them with minimal effort, usually monetary gain or valuable information gained.
Summary
In this chapter we have mentioned the brute force attack and the way it works. So a brute force attacks is a hacking method wherein attackers guess passwords or encryption keys to advantage unauthorized access to programs. We have additionally seen remarkable examples of brute force attacks involving breaches on LinkedIn, Sony PlayStation Network (PSN), and WordPress, highlighting the significant impact of protection breaches. The primary goal of criminals who use brute force is to benefit unauthorized access to, thieve data, take advantage of vulnerabilities, or upload documents with a purpose to advantage cash or access treasured statistics.
Organizations should enforce strong safety features, like robust password rules and multi-factor authentication, to shield towards brute force attacks and different protection threats. Critical attacks are a serious cybersecurity risk that should be treated with powerful security measures.