
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - Need for Encryption
A large volume of private information is sent over the Internet, including passwords entered into login screens, emails carrying personal information, and tax documents uploaded to servers.
Private data is transmitted over the Internet in packets with the help of the same pathways as public data. Unfortunately, malicious individuals have found methods to intercept this data during its journey across the Internet.
We will explore the importance of encryption and its role in safeguarding sensitive information.
What is Encryption?
Encryption is the process of coding our data to hide its true meaning. Cryptography is the study of data encryption and decryption. Encryption has been safeguarding sensitive data for a long time and was once primarily used by governments and military forces. Encryption secures data both when it is being transmitted across networks and devices and when it is stored on computers and other storage devices. Encryption helps secure sensitive information such as passwords, financial data, and personal details from unauthorized access and manipulation.
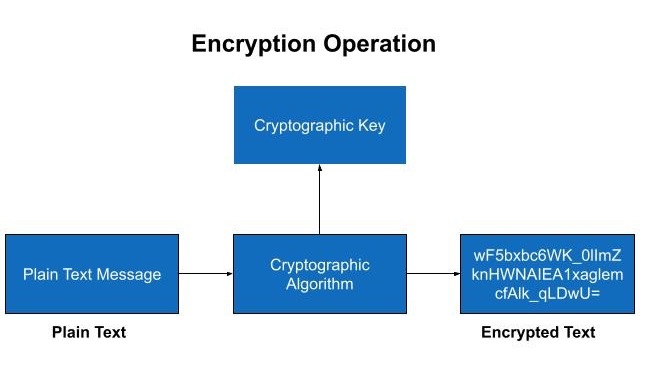
What data should be Encrypted?
Lack of proper data encryption can lead to complex issues. When confidential information gets leaked, it can severely damage your business and data in various ways, such as causing economic disasters, harming your brand, and resulting in a loss of customer trust.
You need to back up all encrypted data. Data encryption should cover both at-rest and in-transit data for complete protection. Below are some categories of data that require encryption −
- Credit Card Details
- Account Passwords
- Social Numbers
- Mobile Phone Numbers
- House Addresses
- Bank Account Details
- Patient Health Details
- And many other confidential details
The Core Principles of Cryptography and Encryption
Encryption is crucial for the protection of various IT assets and private identified data. With this, encryption meets four important principles −
Confidentiality
Encryption makes sure that only authorized parties can access and understand the encrypted data. Encodes the data to prevent it from being understood if it is intercepted by a third party. By changing the plaintext into ciphertext using cryptographic algorithms to secure the private data. For example: It is like having a secret language that only you and your friends understand.
Authentication
It is the process of making the piece of data being claimed by the user belong to it. It verifies the origin of the data that has been encrypted. Digital certificates and cryptographic protocols authenticate users and devices by validating their credentials and confirming their identity before establishing secure communication channels. Authentication prevents impersonation attacks and unauthorized access by ensuring that only trusted entities can decrypt and access encrypted data.
Integrity
Encryption helps maintain the integrity of data by finding any unauthorized changes or modifications. Using techniques like digital signatures and message authentication codes (MACs), encryption ensures that the encrypted data is unchanged during transmission or storage. So we can say, it is like putting a special seal on a letter. If someone tries to open it before it gets to you, you'll know because the seal will be broken.
Nonrepudiation
Nonrepudiation prevents senders from denying they sent the encrypted data. Encryption provides non-repudiation by making sure that parties cannot deny their actions or transactions. For example - It is like getting a receipt when you buy something. If you try to say you didn't buy it later, the receipt proves you did.
Benefits of Cryptography and Encryption for Security
Protecting the confidentiality of digital data kept on computer systems or sent over the internet or other computer networks is the main goal of encryption. It is used to protect many types of data, like private and confidential company information, and military and public records.
- Encrypting data helps organizations reduce their risk of serious penalties, long legal proceedings, revenue loss, and a damaged reputation.
- Many firms use encryption not only to protect their data but also to meet rules that require sensitive data to be protected.
- In rare cases where unauthorized parties or hackers manage to access the data, encryption ensures they are unable to decipher it.
For example, sellers must encrypt consumer credit card data when it is at rest and when it is being sent over public networks, in keeping with the credit Card Industry Data Security Standard.
Challenges in Encryption
Encryption presents several challenges, particularly in managing encryption keys, which are crucial for accessing encrypted data. The process of key management can be complex and poses risks if not handled properly.
- With the help of encryption, the data is safe from attackers, but in some cases, it can stop the owners of the data from being able to access their information.
- If encryption keys are lost or destroyed, owners might never access their data again.
- Hackers might target encryption keys instead of the data itself, making it easy for them to decode information.
- Managing encryption keys is hard because they have to be stored securely, but attackers know where to look.
- There are best practices for managing encryption keys, but they make backup and restore processes complicated.
- Retrieving and transferring keys to a new server can delay recovering data.
- Just setting up a key management system is not enough; managers need a plan to protect it.
- This includes backing up the key management system separately and arranging backups so keys are easy to get in a disaster.