
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
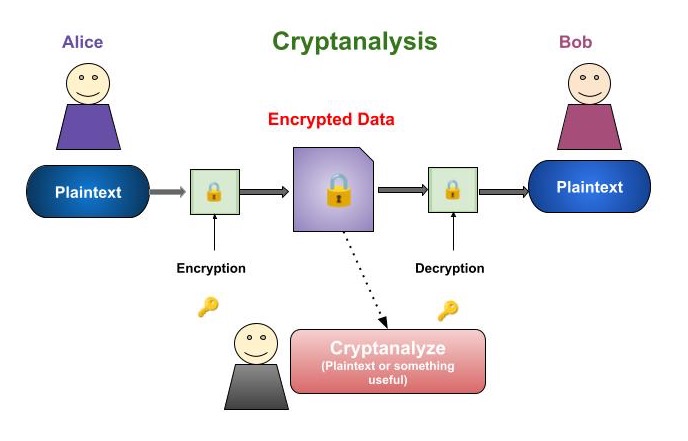
Cryptosystems - Cryptanalysis Techniques
Before deep dive into cryptanalysis techniques let us first discuss what exactly cryptanalysis is, who are cryptanalysts and what are their roles and responsibilities.
The study of decrypting and examining encrypted text and messages without the need for a key is known as cryptanalysis. It's a combination of study and exercise.
It is based on the assumption that experts in mathematics, physics and cryptanalysis are unaware of the process and miss the necessary keys for encryption and decryption
It is also a way to easily view the content of a transaction when you don't have access to a decryption key.
Who are Cryptanalysts?
The codes are interpreted by cryptanalysts. The term "cryptoanalysis" is derived from the Greek words krypts (means "hidden") and analein (means "analysis"). As a cryptanalyst, you are in charge of decoding or decrypting data to understand cryptic signals, even if you do not have the encryption key.
Role and Responsibilities of Cryptanalysts
In order to access data that would otherwise be difficult to read, a cryptoanalyst will examine ciphers, codes, and encryption systems to learn how they operate.
Your specific responsibilities as a crypto analyst will vary depending on the company and organization you work for.
The following are some real-world cryptoanalyst positions and responsibilities −
Gathering, analysing, and processing data
Analyse scrambled intercepts
Make use of encrypted resources
Debugging software programmes
Find the cryptography algorithms' flaws.
Create new cryptanalysis tools.
Develop strategies to exploit vulnerabilities in computer networks.
How is Cryptanalysis performed?
While the aim of cryptanalysis is to find weaknesses in cryptographic algorithms or find alternative ways around them, cryptographers use cryptanalysts' knowledge to improve, replace, or enhance weak techniques.
The term "cryptology," which is defined as the mathematical study of codes, ciphers, and related algorithms, includes both cryptography, which focuses on developing and improving encryption ciphers and other procedures, and cryptanalysis focuses on decoding encrypted data.
Researchers may create attack strategies that fully overcome an encryption method, making it possible to decrypt ciphertext that has been encrypted using that algorithm without requiring the encryption key. Sometimes, cryptanalysis's findings identify problems with the design or application of the technique, which reduces the quantity of keys that need to be tried on the target ciphertext.
The methods for cryptanalysis differ based on the kind of cipher used. This previously stated, one way to break into simple substitution ciphers is to figure out which letters are most commoonin the message and then compare the result to a list of the most common letters in the English language. Another encryption technique is called a transposition cipher, which reorders the message's characters without altering them. These ciphers are vulnerable to "anagramming" approaches, which involve experimenting with different letter combinations and looking for patterns or words that are simple to identify in the results.
Cryptanalysis Techniques & Attacks
A cryptographic system must be attacked in order to identify its vulnerabilities. We refer to them as cryptanalytic attacks. The nature of the algorithm and an understanding of the general characteristics of the plaintext which may be Java code or a conventional English document are prerequisites for the attacks. Therefore, before attempting to take advantage of the attacks, one should be aware of the nature of the plaintext.
There are a wide variety of cryptanalysis attack techniques. However, the two most widely used methods are −
Ciphertext-Only Attack
A potential attacker does not know the encryption algorithm being used, the plaintext data, or any cryptographic key data other than the at least one encrypted message that they have access to. When intelligence agencies try to decipher encrypted messages from a target, they frequently encounter this challenge. However, because there is not much target data, this attack is difficult to execute.
Known Plaintext Attack(KPA)
When it comes to implementation, this attack is simpler than the ciphertext-only attack. The analyst probably has access to some or all of the plaintext of the ciphertext when they use a known plaintext attack. Finding the key that the target used to encrypt the communication and using it to decrypt it are the cryptanalyst's goals. The attacker can decrypt any message encrypted with that particular key once they have found it. Attackers using known plaintext techniques must be able to decipher all or part of an encrypted message, or even only the format of the original plaintext.
Here are some additional techniques and types that cybersecurity professionals may need to be aware of −
Differential Cryptanalysis Attack(DCA)
This particular variant of the plaintext attack targets block ciphers that examine plaintext in pairs instead of the one at a time. Using this method enables the analyst to figure out how the algorithm in problem works when it encounters various data types.
Man-in-the-Middle Attack(MITM)
When an intruder manages to get into a normally secure channel used by two parties to exchange keys, an attack takes place. The key exchange is carried out by the cryptanalyst with each end-user, who thinks they are carrying it out with each other. As a result, the people concerned are utilising a key that the attacker is aware of without realising it.
Differential Cryptanalysis
A cryptanalyst using differential cryptanalysis can access pairs of messages that are closely related, differing only by a single letter or bit, along with their encrypted versions. This enables the attacker to investigate how modifications made to the source text affect the ciphertext produced by the algorithm.
Chosen Plaintext Attack(CPA)
When an analyst uses a selected plaintext attacks, they can either use the encryption device or already know the encryption. The selected plaintext can then be encrypted using the intended algorithm by the cryptanalyst in order to obtain information about the key.
Side-Channel Attack(SCA)
Side-channel attacks depend on data obtained from the actual system used for encryption and decryption. Rather than using the plaintext that is going to be encrypted or the ciphertext that is produced during the encryption process, this attack makes use of data related to the target system's power consumption or response time to queries.
Dictionary Attack(DC)
Usually, a lot of people use passwords that are either whole words or easily guessed alphanumeric combinations. By encrypting every word in a dictionary and determining whether the hash produced by this process matches the encrypted password stored in a SAM file format or another password file, analysts take advantage of this pattern.
Cryptanalysis Tools
A number of tools are used in cryptanalysis. Here are a few examples −
Cryptol
It is an open-source tool for cryptanalysis that was first created by the US National Security Agency. It helps users to examine and keep an eye on how cryptographic methods are operating. With its help, users can write programmes that define algorithms or ciphers and see how they work.
Ganzua
A skeleton key or lockpick is called a Ganzua in Spanish. Analysts can define nearly arbitrary cipher and plain alphabets with this open-source, multi-platform Java programme. Users will also be able to solve cryptograms that are not in English thanks to this feature.
CrypTool
It offers web portals and e-learning courses so users can study cryptanalysis methods and cryptographic algorithms. In addition, it provides an easy way of learning cryptographic techniques and lets users test and evaluate various algorithms.