
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
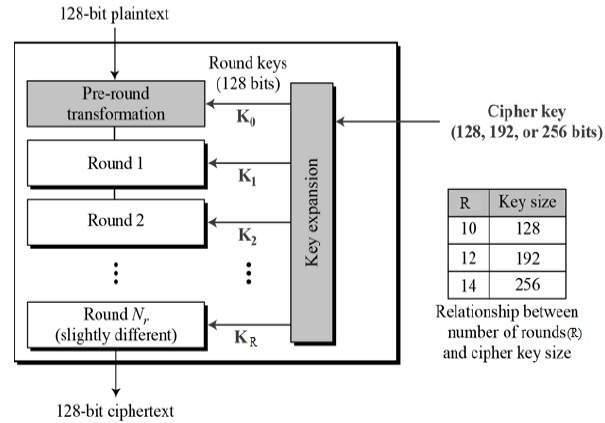
Cryptography - AES Transformation Function
We will now go through each of the four AES transformations one by one. We describe the forward (encryption) algorithm, the inverse (decryption) algorithm, and the stage's rationale for each step.
Substitute Bytes Transformation
The primary phase in the AES encryption process is the Substitute Bytes transformation, or SubBytes. Now we are going to study it −
Purpose
- Making the encryption process non-linear is the goal of the SubBytes transformation.
- Using a pre-made substitution table called the S-box, each byte in the state matrix is changed to a new byte.
- This modification increases the encryption process' resilience to cryptanalysis techniques by introducing confusion.
S−box
- An S-box is a fixed 16x16 matrix with 256 predefined byte values.
- Each byte in the S-box has a value that is determined by a specific mathematical process.
- The S-box's one-to-one mapping of input and output bytes allows for reversibility.
How it Works?
- During the SubBytes transformation, each byte in the state matrix is changed to match a byte from the S-box.
- Every byte in the state matrix is replaced individually, resulting in the creation of a new state matrix.
- This substitution phase improves the encryption process's defence against various kinds of attacks, including differential cryptanalysis, by introducing non-linearity.
Advantages
- SubBytes breaks any symmetries in the plaintext, which adds difficulty to the encryption.
- It increases the diffusion and confusion characteristics required for strong encryption.
- When a preset S-box is used, the inverse S-box ensures a constant and reversible replacement method, which makes it useful for decryption.
As a result, the SubBytes transformation is important to the AES encryption process because it improves the non-linearity and confusion of the encrypted data, hence enhancing its security. It is a crucial component of the well-known AES encryption method that secures private information.
ShiftRows Transformation
The ShiftRows transformation is an important phase in the Advanced Encryption Standard (AES) encryption process. Let us see the working of this transformation −
Purpose
The purpose of the ShiftRows transformation is to produce diffusion in the state matrix, distributing each byte's influence across the matrix. It contributes to creating uncertainty and raising the encryption's complexity, which improves the ciphertext's security.
How it works?
- During the ShiftRows transformation, the bytes in each row of the state matrix are shifted continually to the left.
- The third row is moved by two positions, the fourth row by three positions, and the second row is shifted to the left by one position. The initial row remains unchanged.
- The shifting, which is carried out independently for each row in the state matrix, results in a new state matrix.
Example
Assume that our state matrix is 4x4 −
[a0, a1, a2, a3] [b0, b1, b2, b3] [c0, c1, c2, c3] [d0, d1, d2, d3]
Following the ShiftRows transformation −
[a0, a1, a2, a3] [b1, b2, b3, b0] [c2, c3, c0, c1] [d3, d0, d1, d2]
Advantages
- ShiftRows adds diffusion to the encryption process by rearranging the bytes within each row of the state matrix.
- It increases the overall security of the encryption by making sure that each byte in the state matrix influences several bytes in subsequent encryption rounds.
A key component of the AES encryption process, the ShiftRows transformation adds to the difussion and confusion properties needed for robust encryption. It is essential to maintaining the security of encrypted data since it distributes each byte's impact across the state matrix.
MixColumns Transformation
The MixColumns transformation is an additional step in the AES (Advanced Encryption Standard) encryption process. Let's examine it now −
Purpose
- The MixColumns transformation attempts to add diffusion and strengthen encryption security.
- It operates on the columns of the state matrix by treating each column as a polynomial over a finite field.
- MixColumns provide confusion and make the encryption process resistant to various cryptanalysis techniques.
How it Works?
- During the MixColumns transformation, a fixed matrix transformation is multiplied by each column of the state matrix.
- This transformation requires multiplying each column by a certain matrix and then translating the output modulo a predefined polynomial.
- Each column of the original state matrix is multiplied and reduced independently to create a new state matrix.
Example
Let us consider a matix of 4x4 −
[a0, a1, a2, a3] [b0, b1, b2, b3] [c0, c1, c2, c3] [d0, d1, d2, d3]
After the MixColumns transformation −
[a0', a1', a2', a3'] [b0', b1', b2', b3'] [c0', c1', c2', c3'] [d0', d1', d2', d3']
Advantages
- Diffusion is introduced into the encryption process using MixColumns, which mixes the bytes in each state matrix column.
- It increases overall encryption security by ensuring that each byte in the state matrix affects many bytes in subsequent encryption rounds.
An integral component of the AES encryption process, the MixColumns transformation adds to the diffusionand confusion characteristics needed for strong encryption. By blending the bytes in every state matrix column, it is important for maintaining the security of encrypted data.
AddRoundKey Transformation
The AddRoundKey transformation is also an important step in the AES (Advanced Encryption Standard) encryption process. Let's take a close look at it −
Purpose
- The AddRoundKey transformation adds the encryption key to the encryption process.
- Because of the state matrix and a round key created from the original encryption key, every encryption round now depends on both the plaintext and the encryption key.
- This step integrates the secret key data into the encryption process to ensure that the resulting ciphertext is safely dependent on both the plaintext and the key.
How it Works?
- During the AddRoundKey transformation, each byte in the state matrix is XORed with the corresponding byte of the round key.
- The original encryption key helps to generate the round key that is used in each round through the process of key expansion.
- A separate XOR operation is carried out for each byte in the state matrix, creating a new state matrix.
Example
Let us say we have our state matrix of 4x4 −
[a0, a1, a2, a3] [b0, b1, b2, b3] [c0, c1, c2, c3] [d0, d1, d2, d3]
After the AddRoundKey transformation of the round key −
[k0, k1, k2, k3] [k4, k5, k6, k7] [k8, k9, k10, k11] [k12, k13, k14, k15]
The final state matrix is as follows −
[a0 ⊕ k0, a1 ⊕ k1, a2 ⊕ k2, a3 ⊕ k3] [b0 ⊕ k4, b1 ⊕ k5, b2 ⊕ k6, b3 ⊕ k7] [c0 ⊕ k8, c1 ⊕ k9, c2 ⊕ k10, c3 ⊕ k11] [d0 ⊕ k12, d1 ⊕ k13, d2 ⊕ k14, d3 ⊕ k15]
Advantages
- AddRoundKey makes sure that the plaintext and the encryption key have an impact on every encryption round.
- An additional layer of protection is added by encryption using secret key material, which makes it more difficult for attackers to decrypt the ciphertext without the key.
The AddRoundKey transformation, that includes the secret key material into the encryption process and ensures the security of the generated ciphertext, is an important component of the AES encryption method. It is essential for protecting personal information while it is being moved or kept.