
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - Stream Cipher
A stream cipher encrypts text by applying a key and algorithm to each bit of a data stream one by one. In contrast, block ciphers process data in blocks of multiple bits at once. Stream ciphers are mainly used to encrypt one byte (8 bits) at a time.
Since stream ciphers are linear, messages are encrypted and decrypted with the help of the same key. And, while cracking them is difficult, hackers will have to manage to do it.
In this, a keystream, a random series of bits, is generated from a key. To encrypt the data stream, each bit is XORed with an equivalent bit from the keystream.
How does it work?
Stream ciphers make use of a common key (symmetric key) to code their data. Encryption and decryption processes of the data are handled by this symmetric key. Unlike public-key ciphers, stream ciphers utilize one key for encryption as well as decryption, eliminating the need for different keys for each task (for instance, using one key to encrypt and another to decrypt).
Cryptographic methods generally conceal data from unauthorized access by scrambling it. However, stream ciphers differ by processing data bit-by-bit, unlike block ciphers that operate on collections of data known as blocks.
Stream ciphers involve
Plaintext − The original message to be encrypted.
Keystreams − Random sequences of characters (e.g., numbers, letters, symbols) that replace the plaintext characters.
Ciphertext − The encrypted message. Key generation is a complex mathematical operation, but modern computers can perform it quickly.
In a stream cipher, individual bits of plaintext are inputted and subjected to a mathematical operation. The result is jumbled text which needs the right key to decode.
Using the proper key, the receiver can reverse the process and convert the scrambled text back to its plaintext.
In stream cipher encryption, the key known as a one-time pad is exceptionally secure due to its unique property. It is designed to be equivalent in length to the message being encrypted, ensuring that an attacker cannot mathematically decipher the message without having the original key.
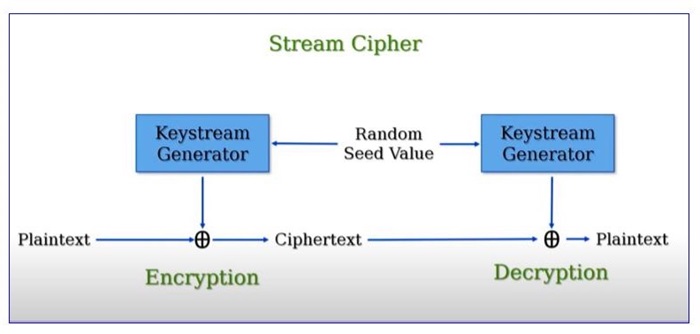
Keystream Generation
Let us see at a basic example of keystream creation with the help of an XOR-based stream cipher.
Let's say we have the below data −
Key: 101011
Initialization Vector (IV): 110100
To create a stream of encrypted data (keystream):
Set up the encryption algorithm with a secret key and initialization vector (IV).
If needed, adjust the key and IV to be the same length as the message being encrypted.
Combine the key and IV using an exclusive OR (XOR) operation to generate the keystream.
Here is the step by step process −
Key: 101011
IV: 110100
Keystream: 011111
Now, let us say we have a plaintext message as: 1100101.
To encrypt this plaintext using the keystream −
Plaintext: 1100101
Keystream: 011111
Ciphertext: 1011010
To decrypt the ciphertext, we would use the same keystream −
Ciphertext: 1011010
Keystream: 011111
Plaintext: 1100101
This example explains how to generate a keystream, which is then used to encode and decode a message, using a key and an initialization vector. For better safety, more complex methods and bigger key sizes are used in real-world applications.
Categories of Stream Ciphers
Stream ciphers fall into two main categories with slightly different mechanisms −
Synchronous Stream Ciphers − Employ a secret key to produce key streams independent of the plaintext and ciphertext.
Self-Synchronizing Stream Ciphers − Utilize a secret key and additional randomization to enhance security against hacking.
Alternative encryption options is Block cipher which divides messages into smaller blocks and applies an encryption algorithm to each block.
Advantages of Stream Cipher
Here are some benefits of Stream Cipher:
Speedy Encryption and Decryption: Stream ciphers encrypt and decrypt data at single bit or byte speeds, making them ideal for real-time communication and demanding applications.
Low Hardware Requirements: Stream ciphers can be easily implemented in simple performance (such as XOR) hardware, allowing them to be implemented efficiently on a variety of devices and systems.
Selective Access: Stream ciphers provide the ability to decrypt particular parts of encrypted data selectively, which is useful when needing to access or modify specific portions without decrypting the entire message.
Disadvantages of Stream Cipher
Below are some disadvantages of Stream Cipher technique −
Vulnerability to Known Plaintext Attacks − Known plaintext attacks are harmful to stream ciphers. An attacker can identify the encryption keystream when they have pieces of both the plaintext and the ciphertext, which include the encrypted message. This can potentially expose the protected data.
Lack of Diffusion − Stream ciphers have poor diffusion. When the plaintext changes slightly, the ciphertext also changes only slightly. This makes it easier for attackers to study patterns and possibly restore the original message even without knowing the encryption key.
Popular Stream Ciphers
Some popular stream ciphers are −
RC4 − Because it was quick and easy to use, RC4 was earlier widely used in the SSL/TLS and WEP/WPA protocols, but it was out of date due to security vulnerabilities.
Salsa20 − Salsa20, developed by Daniel J. Bernstein, is known for its efficiency and safety. Applications like secure communications and disk encryption frequently use it.
ChaCha − ChaCha is a newer version of Salsa20, designed with better diffusion and protection against certain attacks. It's often used in protocols like TLS and VPNs.
HC-128 − Hongjun Wu's stream cipher offers excellent efficiency along with robust security. It works effectively in devices with limited capabilities, like cell phones.
Grain − Martin Hell and Thomas Johansson developed this lightweight stream cipher. It is particularly efficient when implemented in hardware, making it ideal for use in applications such as RFID tags and sensor networks.