
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - Double DES
In the previous chapter we saw what is data encrytption standard in this chapter we will see detailed information about Double DES.
Double DES is a type of encryption where the same plaintext is encrypted using a pair of DES. Different keys are provided in both cases to encrypt the plaintext. Learning double DES is easy.
Double DES uses two keys, k1 and k2. For it to obtain the encrypted text, it can apply DES to the original plaintext using k1. With a different key, k2, it can apply DES to the encrypted text this time. The encrypted text that is displayed is the final output.
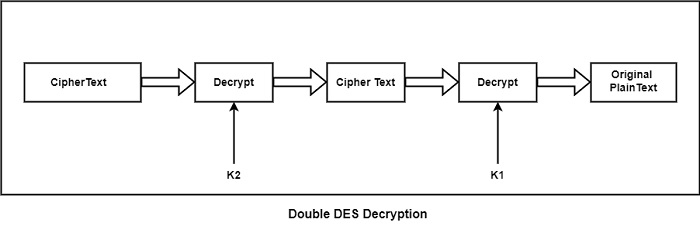
How does Double DES Work?
To create the singly encrypted ciphertext, first use the key K2 to decrypt the double encrypted cipher-text block. The original plaintext block can be retrieved by decrypting this ciphertext block with key K1.

If it is capable of using a single-bit key, then 0 and 1 are the two available keys. There are four possible key values, like (00, 01, 10 and 11), if it can use a two-bit key.
In most cases, the cryptanalyst must implement 2n operations in order to try out every possible key if it can use an n-bit key. The cryptanalyst will have to make 22nn attempts to crack the key if it is possible to use two distinct keys, each with n bits.
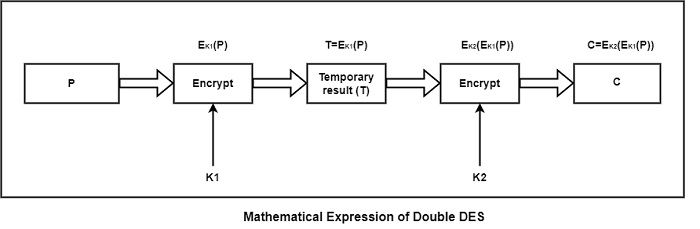
Think about a message's P (plain-text block) and C (corresponding final cipher-text block) as the two basic elements of information that the cryptanalyst is aware of. Double DES stated numerically, as seen in the figure.
The result of the first encryption is known as T and is indicated as T = Ek1(P) [i.e., encrypt the block P with key K1]. After this encrypted block is encrypted with another key K2, it indicate the result as −
C = Ek2(Ek1(P))
[i.e., encrypt the already encrypted block T, with a different key K2, and call the final ciphertext as C].
Meet in Middle Attack
In the double DES can be destroyed by known plaintext attack known as meet-in-themiddle attack.
Given a plaintext P and two encryption keys K1 and K2, ciphertext C is produced as C = Ek2(Ek1, (m)) decryption needed that the keys be used in reverse order −
P = Dk1(Dk2, (C))

A Meet-in-the-Middle (MitM) Attack is a type of cryptanalytic attack where the attacker need some type of space or time tradeoff to support the attack. MITM attempt can decrease the amount of difficulty needed to perform the assault in its original state.
Merkle and Hellman introduced the terms of meet-in-the-middle attack. This attack contains encryption from one end and decryption from another and connecting the result in the middle, therefore is the name meet-in-the-middle.
MITM can create the form of dividing the target connection into two so that each element can be addressed independently. It can mean changing an attack requiring X amount of time into one requiring Y time and Z space. The goal is to significantly decrease the effort required to implement a brute-force attack.
Meet-in-the-Middle attackers try to reconcile the difficulty contained in a high cryptanalytic attack by meeting in the middle, or halving the area of what they are analyzing to create the effort applicable or reasonable in their view.
The main aim of an attack is to steal personal information, including login credentials, account details and credit card numbers. Targets are frequently the users of monetary applications, SaaS businesses, e-commerce sites and other websites where logging in is needed.
Data acquired at the time of an attack can be used for several goals, such as identity theft, unapproved fund transfers or an illicit password change.
There are two keys including K1 and K2 are used for encrypt plaintext P into ciphertext C and the similar K1 and K2 are used for decryption. The intermediate text produced by first encryption and of first decryption, M should be the similar i.e., the two relationship must hold.
Let us say a cryptanalyst have a previous pair of P and C then it can use all possible values (256) of K1 and record all values of M. Similarly for all values of K2 access all M and thus compare these M's of K1 and K2 and discover a pair of K1 and K2 for which M is same.
If only one such pair occur then K1 and K2 are the desired keys. If more than one pair exists for which K1 and K2 are equal, another intercepted plaintext/ciphertext pair is utilized.
Advantages
The Double DES (Data Encryption Standard) method of data encryption involves quickly performing the DES algorithm twice. The following are Double DES's advantages −
- Enhanced Security − By doubling the length of the key, Double DES improves the security of DES and makes it more difficult for attackers to decrypt encrypted data via brute-force attacks.
- Compatibility with Current Systems − Double DES can be implemented with current DES hardware and software, making it a simple option for businesses who currently use DES.
- Widely Studied − Due to the in-depth study and analysis that DES has received over the years, double DES can be applied and understood with the help of a variety of information and resources.
Disadvantages
- Vulnerable to Meet-in-the-Middle Attack − Double DES is vulnerable to a meet-in-the-middle attack, which involves an attacker intercepting the ciphertext and trying every key for the first encryption and decryption phases while storing the intermediate results. They then try each key for the second encryption stage until they find one that corresponds with the previously saved results. Therefore, the effective key length decreases to 112 bits, significantly weakening the theoretical 168-bit key length.
- Performance Overhead − Because double DES encryption takes more time and computing power than single DES encryption, it may have a performance overhead.
- Limited Key Length − While double DES has doubled the key length compared to single DES, it has a relatively limited key length (112 effective bits after calculating for the meet-in-the-middle attack). This may not be enough for handling sophisticated attacks, especially with the development of more powerful computing technologies.