
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - Double Strength Encryption
In the same way that technology changes, hackers and criminal organizations also change strategies to gain unauthorized access to sensitive data. For example, with cyber criminals getting better at their hacking activities, a single level of encryption is no longer enough in protecting your files. This is where double encryptions come in. We will see what exactly double strength encryption is, how it works and its importance towards having a secure online privacy.
What is Double Strength Encryption?
As the name suggests double encryption means we will encrypt the content or data two times. It is the type of encryption technology which adds an extra layer of security to our content and digital communications. By using this technique we can use two different encryption algorithms at both the stages. This encryption ensures secure file sharing, managed file transfer, secure web firms and also transmission of emails.
Double encryption increases the security of your important and sensitive data at rest and as well as in motion. So the importance of this is if the attacker is able to break one layer of security so there is less chance to access the original message because of the second layer of encryption. This technique is very difficult for cybercriminals to access our sensitive information.
Following is a simple diagram which is showing double strength encryption process −
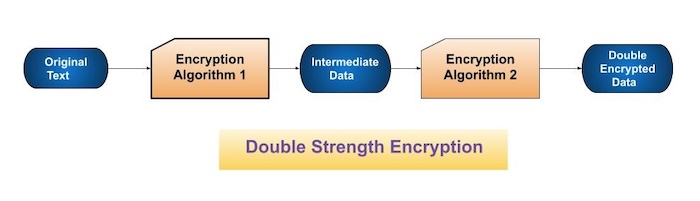
In the above diagram −
Original Text − It is the original message which is shared between two communication channels.
Encryption Algorithm 1 − It is the first algorithm that encrypts the original message.
Intermediate Data − It is the intermediate data which is encrypted using the first encryption algorithm.
Encryption Algorithm 2 − It is another algorithm which will again perform the encryption process and create double encrypted data.
Double Encrypted Data − This is the final data which is double encrypted to send it to the receiver.
How does this work?
In a typical encryption process, file and email data is encrypted once by means of an encryption key, then the encrypted data is sent to the intended recipient who uses the same key to decrypt it. In double encryption, this process is repeated with a second encryption key resulting in a doubly encrypted file: once at the file level and again at the volume level. The recipient will use their respective decryption keys to decode the data.
The first layer of double encryption is known as its outer layer. It is primarily designed to protect private information from unauthorized access. One could use one of several common algorithms like AES-256 or TLS 1.2 for this layer that encrypts files and email communications. The most powerful layer of encryption in most cases tends to be the outermost one; typically security protocols and practices place emphasis on it as such. A specific cryptographic algorithm converts original data into an unreadable state after applying this layer on it. Through applying another algorithm, the second layer encrypts already encrypted data. This process leads to two layers of encryption that should be sequentially decrypted in order to reach the original information.
Types of Double Strength Encryption
There are mainly three types of double encryption: first is symmetric-key encryption, second is asymmetric-key encryption, and third is hashing.
Symmetric Key Encryption
Symmetric encryption is a method of encrypting data using the same key for encoding and decoding. In some cases, this encryption needs to be used in conjunction with a hashing algorithm and added security. Hashing algorithms change plaintext into cryptographically hashed data (ciphertext) that cannot be converted back to its original form when it undergoes hash one way and not in reverse. It is for this reason that symmetric encryption may be combined with other forms of encryption such as asymmetric encryption.
Asymmetric Key Encryption
This encryption uses two types of keys ie. public key and private key for encoding and decoding the data respectively. A public key encodes that information while a private key can decode it back to the original form. Sometimes, asymmetric cryptography may be used alongside symmetric techniques in order to enhance protection even further. The public key encrypts the information while the private key decrypts it making it harder for unauthorized people to get hold of any confidential data they might want since both keys must be known by anyone seeking access.
Hashing and salting
You can also encrypt the data using cryptographic hash functions. This kind of double encryption is used to create a completely unique signature or fingerprint for the records. This fingerprint can then be used to confirm the authenticity of the data.
Implementation
In this implementation, we will demonstrate double encryption by using two encryption algorithms, AES and RSA, to enhance data security.
First, the original data is encrypted with AES using a secret key, and then the result is further encrypted with RSA using a public key. This double layer of encryption ensures a higher level of security for the data −
Example
Following are the programs to demonstrate the usage of double encryption in 4 different programming languages, i.e., C, C++, Java, and Python −
#include <stdio.h>
#include <string.h>
#include <stdint.h>
void aes_encrypt(uint8_t *data, uint8_t *key, uint8_t *encrypted_data, size_t data_len) {
uint8_t aes_key[16];
for (int i = 0; i < 16; i++) {
aes_key[i] = key[i % strlen((char *)key)];
}
for (size_t i = 0; i < data_len; i++) {
encrypted_data[i] = data[i] ^ aes_key[i % 16];
}
}
void rsa_encrypt(uint8_t *data, uint8_t *public_key, uint8_t *encrypted_data, size_t data_len) {
for (size_t i = 0; i < data_len; i++) {
encrypted_data[i] = data[i] ^ public_key[i % strlen((char *)public_key)];
}
}
void double_encrypt(uint8_t *data, size_t data_len, uint8_t *aes_key, uint8_t *rsa_public_key, uint8_t *result) {
uint8_t aes_encrypted_data[data_len];
aes_encrypt(data, aes_key, aes_encrypted_data, data_len);
rsa_encrypt(aes_encrypted_data, rsa_public_key, result, data_len);
}
int main() {
uint8_t data[] = "This is a secret message.";
size_t data_len = strlen((char *)data);
uint8_t aes_key[] = "AES_Key";
uint8_t rsa_public_key[] = "RSA_Public_Key";
uint8_t encrypted_data[data_len];
double_encrypt(data, data_len, aes_key, rsa_public_key, encrypted_data);
printf("Sample Data: %s\n", data);
printf("Double Encrypted Data: ");
for (size_t i = 0; i < data_len; i++) {
printf("%02x", encrypted_data[i]);
}
printf("\n");
return 0;
}
Output
The output obtained is as follows −
Sample Data: This is a secret message. Double Encrypted Data: 477e7b733b79680d4d10736563727662207766595a68774734
#include <iostream>
#include <vector>
#include <cstdint> // For uint8_t
#include <algorithm> // For std::transform
void aes_encrypt(const std::vector<uint8_t>& data, const std::vector<uint8_t>& key, std::vector<uint8_t>& encrypted_data) {
std::vector<uint8_t> aes_key(16, 0);
for (size_t i = 0; i < 16; ++i) {
aes_key[i] = key[i % key.size()];
}
encrypted_data.resize(data.size());
for (size_t i = 0; i < data.size(); ++i) {
encrypted_data[i] = data[i] ^ aes_key[i % 16]; // XOR operation
}
}
void rsa_encrypt(const std::vector<uint8_t>& data, const std::vector<uint8_t>& public_key, std::vector<uint8_t>& encrypted_data) {
encrypted_data.resize(data.size());
for (size_t i = 0; i < data.size(); ++i) {
encrypted_data[i] = data[i] ^ public_key[i % public_key.size()]; // XOR with public key
}
}
void double_encrypt(const std::vector<uint8_t>& data, const std::vector<uint8_t>& aes_key, const std::vector<uint8_t>& rsa_public_key, std::vector<uint8_t>& result) {
std::vector<uint8_t> aes_encrypted_data;
aes_encrypt(data, aes_key, aes_encrypted_data);
rsa_encrypt(aes_encrypted_data, rsa_public_key, result);
}
void print_data(const std::vector<uint8_t>& data) {
std::cout << "Data: ";
for (auto byte : data) {
std::cout << (char)byte;
}
std::cout << std::endl;
std::cout << "Hexadecimal: ";
for (auto byte : data) {
std::cout << std::hex << (int)byte << " ";
}
std::cout << std::dec << std::endl;
}
int main() {
std::vector<uint8_t> data = {'T', 'h', 'i', 's', ' ', 'i', 's', ' ', 'a', ' ', 's', 'e', 'c', 'r', 'e', 't', ' ', 'm', 'e', 's', 's', 'a', 'g', 'e', '.'};
std::vector<uint8_t> aes_key = {'A', 'E', 'S', '_', 'K', 'e', 'y'};
std::vector<uint8_t> rsa_public_key = {'R', 'S', 'A', '_', 'P', 'u', 'b', 'l', 'i', 'c', '_', 'K', 'e', 'y'};
std::vector<uint8_t> encrypted_data;
// Print original data
print_data(data);
// Perform double encryption
double_encrypt(data, aes_key, rsa_public_key, encrypted_data);
// Print double-encrypted data
std::cout << "Double Encrypted Data: ";
for (auto byte : encrypted_data) {
std::cout << std::hex << (int)byte << " ";
}
std::cout << std::dec << std::endl;
return 0;
}
Output
The output produced is as follows −
Data: This is a secret message. Hexadecimal: 54 68 69 73 20 69 73 20 61 20 73 65 63 72 65 74 20 6d 65 73 73 61 67 65 2e Double Encrypted Data: 47 7e 7b 73 3b 79 68 d 4d 10 73 65 63 72 76 62 20 77 66 59 5a 68 77 47 34
import java.util.Arrays;
public class Encryption {
public static void aesEncrypt(byte[] data, byte[] key, byte[] encryptedData) {
byte[] aesKey = new byte[16];
for (int i = 0; i < 16; i++) {
aesKey[i] = key[i % key.length];
}
for (int i = 0; i < data.length; i++) {
encryptedData[i] = (byte) (data[i] ^ aesKey[i % 16]);
}
}
public static void rsaEncrypt(byte[] data, byte[] publicKey, byte[] encryptedData) {
for (int i = 0; i < data.length; i++) {
encryptedData[i] = (byte) (data[i] ^ publicKey[i % publicKey.length]);
}
}
public static void doubleEncrypt(byte[] data, byte[] aesKey, byte[] rsaPublicKey, byte[] result) {
byte[] aesEncryptedData = new byte[data.length];
aesEncrypt(data, aesKey, aesEncryptedData);
rsaEncrypt(aesEncryptedData, rsaPublicKey, result);
}
public static void main(String[] args) {
byte[] data = "This is a secret message.".getBytes();
byte[] aesKey = "AES_Key".getBytes();
byte[] rsaPublicKey = "RSA_Public_Key".getBytes();
byte[] encryptedData = new byte[data.length];
doubleEncrypt(data, aesKey, rsaPublicKey, encryptedData);
System.out.println("Sample Data: " + new String(data));
System.out.print("Double Encrypted Data: ");
for (byte b : encryptedData) {
System.out.printf("%02x", b);
}
System.out.println();
}
}
Output
The output obtained is as shown below −
Sample Data: This is a secret message. Double Encrypted Data: 477e7b733b79680d4d10736563727662207766595a68774734
import hashlib
import base64
def aes_encrypt(data, key):
# simple AES encryption
encrypted_data = hashlib.sha256(key).digest()[:16] # Use key as AES key
encrypted_data += bytes([data[i] ^ encrypted_data[i % 16] for i in range(len(data))]) # XOR operation
return encrypted_data
def rsa_encrypt(data, public_key):
# simple RSA encryption
encrypted_data = bytes([byte ^ public_key[i % len(public_key)] for i, byte in enumerate(data)])
return encrypted_data
def double_encrypt(data, aes_key, rsa_public_key):
# first encryption with AES
aes_encrypted_data = aes_encrypt(data, aes_key)
# second encryption with RSA
rsa_encrypted_data = rsa_encrypt(aes_encrypted_data, rsa_public_key)
return rsa_encrypted_data
# our sample data to encrypt
data = b"This is a secret message."
# our sample keys
aes_key = b"AES_Key"
rsa_public_key = b"RSA_Public_Key"
# perform double encryption
encrypted_data = double_encrypt(data, aes_key, rsa_public_key)
# display the double encrypted data
print("Sample Data: ", data)
print("Double Encrypted Data:", base64.b64encode(encrypted_data).decode())
Output
Following is the output of the above code −
Sample Data: b'This is a secret message.' Double Encrypted Data: B9yUX/ocpYqJBRMPohec5EC47AbobN2l3g1aWPZP6pwll9IfsGv/yKs=
Advantages
The primary purpose of double encryption is to improve security. By using two extraordinary encryption algorithms, double encryption makes it more complex for an unauthorized user to get entry to the information they're trying to intercept.
Dual encryption can also provide protection against keylogging, which is a method of recording keylogging and capturing when it is installed on a computer or device. Using two separate encryption methods makes it more difficult for a keylogger to intercept data and decrypt it.
Double encryption provides additional protection against cyberattacks such as brute force attacks. If an attacker gains access to hidden data, it will break two encryptions on its own instead of one, making it more difficult and time-consuming.
With double encryption, you can ensure that your data remains private and secure even if intercepted by unauthorized parties. This is especially important if you are sending sensitive information over the Internet or storing data in the cloud.
Disadvantages
The process of encrypting data twice requires additional computing strength and can significantly slow down the data transmission process. Double encryption calls for extra processing time than single encryption, which can affect overall performance. But, the impact on processing time is less, and the advantage of enhanced security outweighs the slight decrease in performance.
Another mission is that double encryption is not always compatible with current structures and infrastructure. The one more layer of encryption can make it more difficult to combine into current systems. And it is specially those for that are not designed for double encryption.
Hybrid Cryptography
Hybrid cryptography is a technique that uses several different ciphers together, combining the advantages of each cipher. The most common approach is to generate a random secret key for a symmetric cipher and then encrypt this key using asymmetric key cryptography.
Because of this model, the original message is actually encrypted using a symmetric cipher and then a private key. After receiving the message, the recipient first decrypts the message using the private key, uses their private key and then decrypts the message using the specified key
Summary
Double encryption includes encrypting data first with one encryption algorithm after which encrypting the already encrypted information one more time with some other algorithm. This technique extensively enhances data security, making it more challenging for unauthorized customers to intercept and decrypt sensitive data.
In this chapter we have seen what double strength encryption, its working, advantages, disadvantages and also its implementation using AES and RSA algorithms.