
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptosystem - Attacks
Cryptography is just like a secret code used to secure the information. Occasionally, some people try to break such codes in order to access private information. These attempts are what we refer to as attacks. Cryptosystems may suffer several forms of attacks which we are going to discuss here.
In the current scenario, not only commerce but almost all aspects of human life are driven by information. so, Protecting sensitive information from attacks and other malicious activities has become important. Let's think about it Information is often a type of attack.
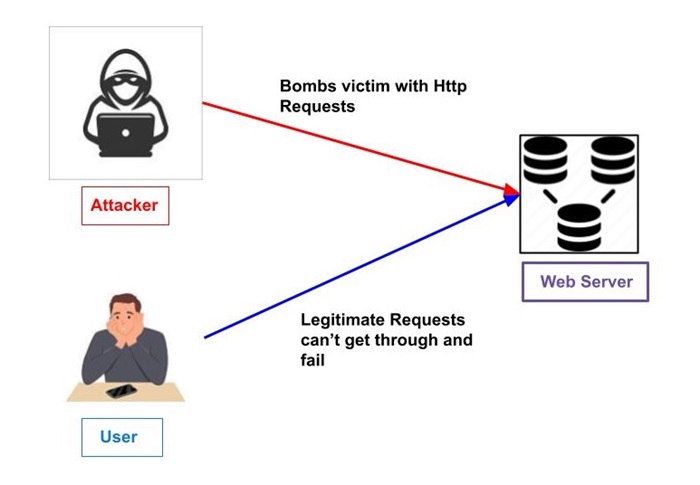
Usually, attacks are classified according to the action taken by the attacker. Attacks may of two forms: passive or active.
Let us see what are these attacks −
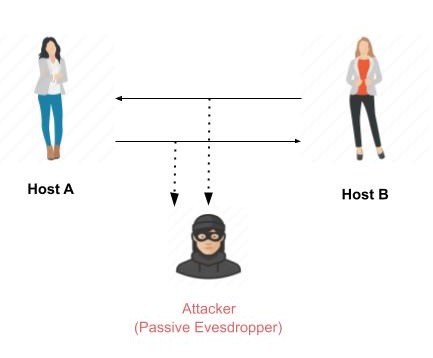
Passive Attacks
Passive cryptography attacks try to gain unauthorized access to sensitive data or information by monitoring or recording on broad communication. In this case, the data and communication remain unaltered and untampered with. Everything that is accessible to the attacker is the data.
These actions are passive, as they do not influence information or interfere with communication channels. Passive attacks are often considered information theft. The only difference between product theft and information theft is that data theft still leaves that data in the possession of the owner. Passive information attacks are thus more dangerous than merchandise theft, as information theft can occur without the owner's knowledge.
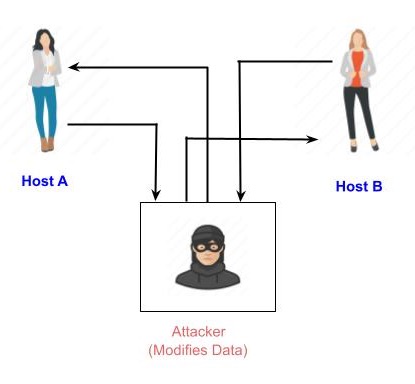
Active Attacks
An active attack consists of performing a process on the information to alter it in some way. For example,
Modifying the information in an unauthorized manner.
Initiating unintended or unauthorized transmission of information.
Modification of authentication data, including the identity of the originator or the information's related timestamp.
unauthorised data deletion..
Denying authorised users access to information (denial of service).
Numerous tools and methods are available in cryptography to create cryptosystems that can defeat most of the attacks mentioned above.
How Attackers Think
Let's look at the current environment for cryptosystems and the attacks used to break them.
Environment around Cryptosystem
Understanding the environment of the cryptosystem is important when thinking about potential attacks. The attacker's capabilities are determined by attacker's assumptions and environmental information.
Three assumptions are made about the security environment and the skills of the attackers in cryptography.
Encryption Scheme Details
The following two cryptography algorithms act as the foundation for cryptosystem design −
Public Algorithms − In this case, the algorithm's entire specification is available to the general public domain which is well-known to everyone.
Proprietary Algorithms − These algorithms are those that are only known to the people who designed the system and its users.
When it comes to proprietery algorithms, security is ensured through obscurity. Since private algorithms are created internally and may not be thoroughly examined for flaws, they might not be the strongest algorithms.
Secondly, they allow communication among closed groups only. As a result, they are inefficient for the high volume of known and unknown items that people communicate with in modern communication. Additionally, the method should be made public with the key containing the encryption strength, according to the Kerckhoff's principle.
Therefore, the attacker's knowledge of the encryption algorithm is the initial assumption concerning the security environment.
Availability of Ciphertext
We are aware that after being converted from plaintext to ciphertext, the data is transmitted over an unsecured public channel, like email. It follows that the attacker can presume to have access to the ciphertext generated by the cryptosystem.
Availability of Plaintext and Ciphertext
This assumption is not as obvious as others. However, there might be scenarios in which an attacker has access to both the plaintext and the related ciphertext. Some such possible circumstances are −
The attacker obtains the ciphertext by convincing the sender to convert the chosen plaintext.
Unintentionally, the recipient might provide the attacker access to the plaintext. The attacker has access to corresponding ciphertext gathered from the open channel.
Any possible attacker can know the encryption key in a public-key cryptosystem since it is in the open domain. He can create matching pairs of plaintexts and ciphertexts with this key.
Cryptographic Attacks
An attacker's primary goal is to crack a cryptosystem and extract the plaintext from the ciphertext. Since the technique is now public knowledge, the attacker just needs to discover the secret decryption key to retrieve the plaintext.
He then puts in all of his effort to discover the cryptosystem's secret key. The attacked system has been declared compromised or broken after the attacker has managed to find the key.
As per the methodology used, attacks on cryptosystems are divided as follows −
Ciphertext Only Attacks (COA) − The attacker has access to a collection of ciphertext(s) while using this method. He is not in control of the relevant plaintext. When a given set of ciphertext can be used to determine the corresponding plaintext, COA is considered to be successful. In some cases, this approach can be used to figure out the encryption key. Current cryptosystems are protected from attacks that target just the ciphertext.
Known Plaintext Attack (KPA) − With this technique, certain portions of the ciphertext are known to the attacker of plaintext. Using this knowledge, the challenge is to decrypt the remaining ciphertext. This could be done via finding the key or in another way. Block ciphers are most effectively attacked using linear cryptanalysis.
Chosen Plaintext Attack (CPA) − The attacker uses this method with an encrypted version of the text of his choice. He can therefore choose the pair of ciphertext and plaintext. This makes it easier for him to figure out the encryption key. Differential cryptanalysis used against hash functions and block ciphers is an example of this type of attack. RSA, a well-known public key cryptosystem, is vulnerable to chosen-plaintext attacks.
Dictionary Attack − There are numerous versions of this approach, all of which involve creating a "dictionary." The attacker creates a dictionary of ciphertexts and matching plaintexts that he has learned over time in the most basic version of this attack. When an attacker receives the ciphertext in the future, he checks the dictionary to determine the matching plaintext.
Brute Force Attack (BFA) − With this technique, the attacker tries every key that could be used in order to figure out the key. There are 28 = 256 potential keys if the key has eight bits. The attacker attempts to decrypt using each of the 256 keys one at a time, having knowledge of the algorithm and the ciphertext. If the key is long, the attack would take a very long time to finish.
Birthday Attack − The attack utilises another version of the brute-force method. It is used to attack the hash function in cryptography. When a student of a class is asked what day they were born, the student can respond with any one of the 365 available dates. Assume for the moment that the first student was born on August 3. Then to find the next student whose birthdate is 3 rd Aug, we need to enquire 1.25 *√365 ≈ 25 students.
In a similar way, if the hash function produces 64 bit hash values, the possible hash values are 1.8x10 19. By continually checking the function for multiple inputs, the same output is approximately to be obtained after about 5.1x10 9 random inputs.
A collision occurs when the attacker finds two distinct inputs that produce the same hash value; in this case, the hash function is considered broken.
Man in Middle Attack (MIM) − The majority of public key cryptosystems, which need key exchange prior to communication, are the targets of this attack.
In order to communicate with host B, host A requests B's public key.
Instead of replying to this request, the attacker transmits his public key.
Thus, the attacker can read whatever that host A sends to host B.
The attacker reads the data with his public key, re-encrypts it, and sends it to B in order to keep the lines of communication open.
In order to make it appear that B is taking it from A, the attacker sends his public key as A's public key.
Side Channel Attack (SCA) − This kind of attack doesn't target any specific kind of algorithm or cryptosystem. Rather, its purpose is to take advantage of a weakness in the cryptosystem's physical implementation.
Timing Attacks − They take advantage of the fact that different processor calculations compute at different rates. It is possible to determine the specific computation the processor is performing by measuring these timings. An extended encryption time, for example, indicates that the secret key is lengthy.
Power Analysis Attacks − These attacks similar to timing attacks in that information about the type of underlying calculations can be determined by measuring power usage.
Fault analysis Attacks − In these attacks, the cryptosystem is made to make errors, and the attacker examines the output to find valuable information.
Practical Cryptographic Attack
Since most of the attacks on cryptosystems mentioned here originate from the academic community, they are considered extremely educational. Actually, a lot of academic attacks involve incredibly unrealistic assumptions about both the attacker's and the environment's capabilities. For example, in chosen−ciphertext attack, the attacker requires an impractical number of deliberately chosen plaintext−ciphertext pairs. It may not be practical altogether.
However, the existence of any attack should raise alerts, particularly if the attack method has potential for development.
Preventing cryptography attacks
A strong cryptographic system should be put in place to prevent cryptography attacks. Some of these ways of preventing this are −
Regularly update the cryptographic algorithms and protocols so that they don't become outdated.
See to it that the data is properly encrypted so that it may not be read even if it falls into the wrong hands.
Strong and unique keys should be used for encryption.
Keep keys in a safe place.
Ensure proper implementation of cryptographic systems.
Test system for vulnerabilities regularly.
Educate employees on cryptosystems attacks prevention.