
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptosystems - Overview
A cryptosystem uses cryptographic methods and the support structures around them to secure information. It's also known as a cipher system.
Cryptosystem uses algorithms to convert plain text into ciphertext to securely encode or decode messages. The term cryptosystem refers to a computer system that uses cryptography, codes to protect information and communications so only the intended can read and process it.
Cryptosystems use algorithms for key creation, encryption, and decoding to keep data secure. Cryptographic keys, bit strings used by algorithms, transform plain text into coded text and vice versa.
The key and variable data are provided as input to an algorithm for this operation. The algorithm's security relies on secure keys.
Cryptosystems use private data like credit cards securely online. Secure email uses signatures, hashes, and key management.
We will look at a basic cryptosystem model. This model keeps transmitted information confidential. You can see this simple model in the picture below −
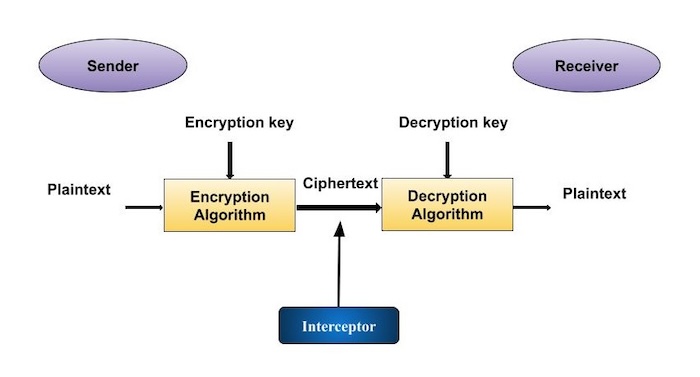
The figure above shows a sender transmitting a sensitive piece of information to a receiver in such a way that the data cannot be extracted by any authenticated or third party in the communication channel.
The goal of this simple crypto scheme is that, at the end of the process, only the sender and receiver will know the private information.
Cryptographic Keys
The key plays an important role in the variable information submitted as input to a cryptographic algorithm to perform an encryption or decryption process. The security of the cryptographic system relies heavily on how secure the keys are that are used. If an unauthorized party were able to access the keys, they could potentially decrypt encrypted messages, pretending to be someone else, or encrypt misleading messages to pose as another individual. It is vital that keys are kept private and are generated, distributed, and stored securely to maintain the integrity of the cryptographic system. The strength of the encryption also depends on the length and complexity of the keys.
Types of Cryptosystems
Fundamentally, there are two types of cryptosystems based on the manner in which encryption-decryption is carried out in the system −
Symmetric Key Encryption
Asymmetric Key Encryption
The biggest difference between these cryptosystems is the link between encryption and decryption keys. In any cryptosystem, both keys are logically connected. It is almost impossible to decrypt the ciphertext using a key unrelated to the encryption key.
Symmetric Key Encryption
The encryption process where the same keys are used for encrypting and decrypting the information is known as Symmetric Key Encryption.
The study of symmetric cryptosystems is referred to as symmetric cryptography. Symmetric cryptosystems are also sometimes referred to as secret key cryptosystems.
A few well-known examples of symmetric key encryption methods are - Digital Encryption Standard (DES), Triple-DES (3DES), IDEA, and BLOWFISH.
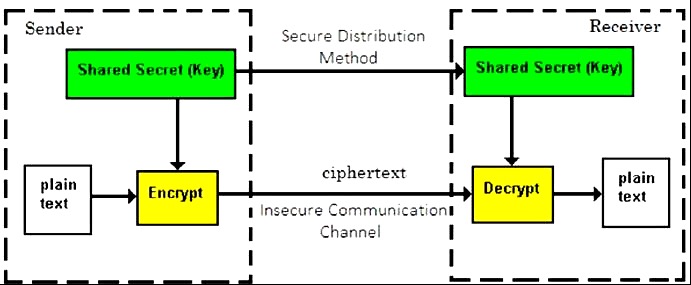
Prior to 1970, all cryptosystems employed symmetric key encryption. Even today, its relevance is very high and it is being used extensively in many cryptosystems. It is very unlikely that this encryption will fade away, as it has certain advantages over asymmetric key encryption.
The salient features of cryptosystem based on symmetric key encryption are −
Persons using symmetric key encryption must share a common key prior to exchange of information.
Keys are recommended to be changed regularly to prevent any attack on the system.
A robust mechanism needs to exist to exchange the key between the communicating parties. As keys need to be changed on a regular basis, this technique becomes expensive and cumbersome.
In a group of n people, to enable two-party communication between any two persons, the number of keys required for the group is n x (n − 1)/2.
Length of Key (number of bits) in this encryption is smaller and hence, process of encryption-decryption is faster than asymmetric key encryption.
Processing power of a computer system required to run a symmetric algorithm is less.
Challenge of Symmetric Key Cryptosystem
There are two main challenges of using symmetric key cryptography.
Key establishment − Before any communication, both the sender and the receiver need to agree on a secret symmetric key. It needs a secure key management scheme in place.
Trust Issue − Since the sender and the receiver use the same symmetric key, there is an implicit requirement that the sender and the receiver 'trust' each other. For example, it may happen that the receiver has lost the key to an attacker and the sender is not informed.
These two challenges are highly restraining for modern day communication. Today, people need to exchange information with non-familiar and non-trusted parties. For example, communication between online sellers and customers. These limitations of symmetric key encryption gave rise to asymmetric key encryption schemes.
Asymmetric(Public) Key Encryption
Asymmetric Key Encryption is the process of encrypting and decrypting information using various keys. Though the keys differ, they are mathematically similar, therefore getting plaintext via decrypting ciphertext is possible. The process is depicted in the following illustration −
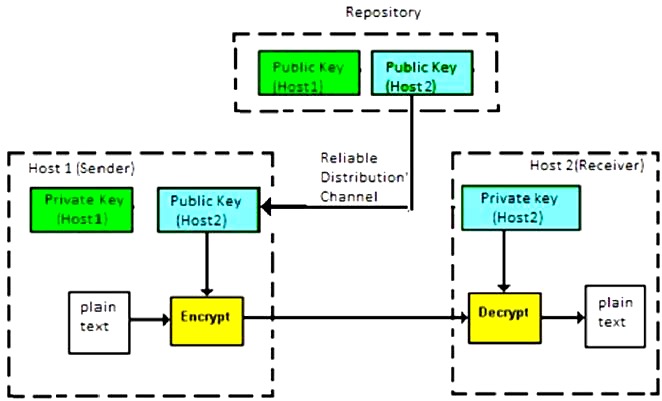
Asymmetric Key Encryption was invented in the 20th century to overcome the necessity of pre-shared secret key between communicating persons. The salient features of this encryption scheme are as follows −
Every user in this system needs to have a pair of dissimilar keys, private key and public key. Because of their mathematical relationship, these keys can be used to decrypt the ciphertext to retrieve the original plaintext when either is used for encryption.
It requires putting the public key in a public repository and the private key as a well-guarded secret. Hence, this scheme of encryption is also called Public Key Encryption.
Though public and private keys of the user are related, it is computationally not feasible to find one from another. This is a strength of this scheme.
When Host1 has to send data to Host2, he gets the public key from the repository, encrypts the file, and sends it.
Host2 uses his private key to extract the plaintext.
Length of Keys (number of bits) in this encryption is large and hence, the process of encryption-decryption is slower than symmetric key encryption.
Processing power of a computer system required to run an asymmetric algorithm is higher.
Symmetric cryptosystems are a natural concept. In contrast, public-key cryptosystems are quite difficult to comprehend.
You may think, how can the encryption key and the decryption key be related', and yet it is impossible to determine the decryption key from the encryption key? The answer lies in the mathematical concepts. It is possible to create a cryptosystem whose keys possess this feature. The concept of public-key cryptography is relatively new. There are fewer public-key algorithms known than symmetric algorithms.
Challenge of Public Key Cryptosystem
One fundamental problem for public-key cryptosystems is that the user has to believe that the public key he is using in communication with another person is actually that person's public key and has not been created by a third party.
This is usually accomplished through a Public Key Infrastructure (PKI) consisting of a trusted third party. The third party securely manages and attests to the authenticity of public keys. When the third party is requested to provide the public key for any communicating person X, they are trusted to provide the correct public key.
The third party ensures user identity by authorization, signing, or another procedure - that X is the one and only, or globally unique, X. The most common method of making the verified public keys available is to embed them in a certificate which is digitally signed by the trusted third party.
Relation between Encryption Schemes
A summary of basic key properties of two types of cryptosystems is given below −
| Heading | Relation between Keys | Encryption Key | Decryption Key |
|---|---|---|---|
| Symmetric Cryptosystems | Same | Symmetric | Symmetric |
| Public Key Cryptosystems | Different, but mathematically related | Public | Private |
Due to the advantages and disadvantage of both the systems, symmetric key and public-key cryptosystems are often used together in the practical information security systems.
Kerckhoff's Principle for Cryptosystem
Kerckhoff's principle is an important concept in the field of encryption. It suggests that the strength of an encrypted system should not depend on keeping the encryption method a secret. Rather, security should come from protecting the encryption key. A well designed encrypted system needs to remain secure even if details about the encryption process become public knowledge.
This idea is crucial for modern encryption standards - it promotes transparent algorithm design and analysis. Knowing the specific encryption process is allowed, as long as the key is concealed. This encourages collaboration from security experts to thoroughly review encryption methods. It also means new algorithms can be openly proposed and tested, with confidence they will not automatically be broken simply by publication. Ultimately, Kerckhoffs' principle is foundational because it shifts focus to diligently shielding the encryption trigger rather than fruitlessly attempting to cloak the encryption mechanism itself.
The concept of information security through cryptography originated in the late 19th century. It was first proposed by Dutch cryptographer Auguste Kerckhoffs, who laid the groundwork for modern cryptanalysis and the design of secure encryption systems. Later in the 20th century, American mathematician and cryptographer Claude Shannon further developed the theory of cryptography and security.
The six design principles defined by Kerckhoff for cryptosystem are −
The cryptosystem should be unbreakable practically, if not mathematically.
Falling of the cryptosystem in the hands of an intruder should not lead to any compromise of the system, preventing any inconvenience to the user.
The key should be easily communicable, memorable, and changeable.
The ciphertext should be transmissible by telegraph, an insecure channel.
The encryption apparatus and documents should be portable and operable by a single person.
Finally, the system has to be easy to utilize, required neither mental strain nor knowledge of a long set of rules to follow.
The second rule is currently known as the Kerckhoff principle. It is applied in virtually all the contemporary encryption algorithms such as DES, AES, etc. These public algorithms are considered to be thoroughly secure. The security of the encrypted message is totally dependent on the security of the secret encryption key.
Keeping the algorithms secret may act as a significant barrier to cryptanalysis. However, keeping the algorithms secret is possible only when they are used in a strictly limited circle.
Importance of Cryptosystems
Cryptosystems play an important role in protecting sensitive information sent over the internet. They allow users to transmit private data, like credit card numbers, in a secure way. Cryptography has various applications beyond just messaging. For example, a secure email system may incorporate digital signatures to verify a sender's identity. It could also use cryptographic hash functions to validate that a message has not been altered during transit. Additionally, such a system would manage encryption keys to encrypt and decrypt correspondence. Overall, the techniques of cryptography help guarantee privacy and integrity in digital communications.