- SAP HANA Admin - Home
- SAP HANA Admin - Overview
- Architecture Overview
- Multitenant Database
- Multiple Host Systems
- Tools
- Cockpit
- Studio
- SAP HANA Admin - System Mngmt
- Multitenant DB Container Mgmt
- Starting a HANA System
- Stopping a HANA System
- License Keys
- Monitoring the HANA System
- SAP HANA Admin - Table Mngmt
- SAP HANA Admin - Table Partition
- SAP HANA Admin - Table Replication
- Data Compression
- Solman Integration
- SAP HANA Admin - Lifecycle Mngmt
- Securing HANA System
- User Provisioning
- Authentication Methods
- Auditing Activities
- Backing Up HANA System
- Recovery HANA System
- HANA XS Application Service
- Data Provisioning
- Smart Data Access
- New Remote System Connection
- Integration with Hadoop
- Key Commands
- Job Responsibilities
SAP HANA Admin - Securing HANA System
It is necessary to implement security in SAP HANA environment to protect critical information and access the database system. You should properly manage authentication and authorization methods, and security policies should be reviewed regularly.
You should also manage the users and roles, auditing activities in SAP HANA, encryption of data in HANA database, and client certificates in the system.
SAP HANA system has many security settings that should be implemented carefully otherwise any misconfiguration can result in a risk of unauthorized access.
SAP HANA Cockpit and HANA Studio provides you with different options to monitor critical security settings.
Following is a list of security related features provided by SAP HANA −
- User and Role Management
- Authentication and SSO
- Authorization
- Encryption of data communication in Network
- Encryption of data in Persistence Layer
Additional features in multitenant HANA database −
Database Isolation − It involves preventing cross-tenant attacks through the operating system mechanism.
Configuration Change blacklist − It involves preventing certain system properties from being changed by tenant database administrators.
Restricted Features − It involves disabling certain database features that provides direct access to the file system, the network, or other resources.
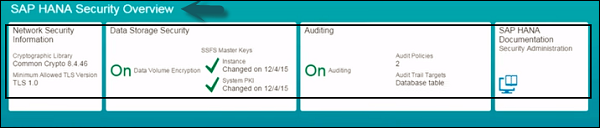
View Security Settings in SAP HANA Cockpit
To view security settings in SAP HANA system, open SAP HANA Cockpit and navigate to SAP HANA Security Overview group.
You should have the role sap.hana.security.cockpit.roles::DisplaySecurityDashboard assigned to view the security settings in HANA Cockpit.
You can check the status of security on each tile under SAP HANA Security Overview. You can further drill down by clicking on any tile to see more details.