- Metasploit - Home
- Metasploit - Introduction
- Metasploit - Environment Setup
- Metasploit - Basic Commands
- Metasploit - Armitage GUI
- Metasploit - Pro Console
- Metasploit - Vulnerable Target
- Metasploit - Discovery Scans
- Metasploit - Task Chains
- Metasploit - Import Data
- Metasploit - Vulnerability Scan
- Metasploit - Vulnerability Validation
- Metasploit - Exploit
- Metasploit - Payload
- Metasploit - Credential
- Metasploit - Brute-Force Attacks
- Metasploit - Pivoting
- Metasploit - Maintaining Access
- Metasploit - MetaModules
- Metasploit - Social Engineering
- Metasploit - Export Data
- Metasploit - Reports
Metasploit - Import Data
Metasploit is a powerful security framework which allows you to import scan results from other third-party tools. You can import NMAP scan results in XML format that you might have created earlier. Metasploit also allows you to import scan results from Nessus, which is a vulnerability scanner.
Lets see how it works. At first, perform an NMAP scan and save the result in XML format on your desktop, as shown in the following screenshot.
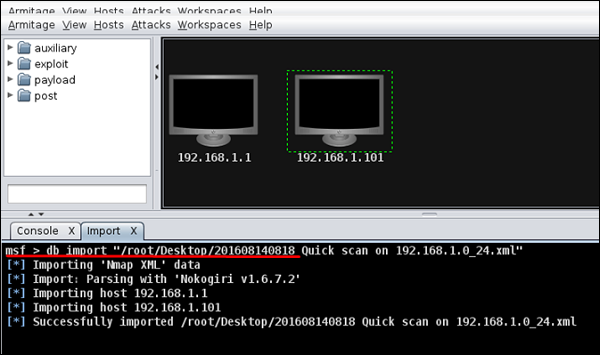
Next, open Metasploit or Armitage to import the scan results. Thereafter, use the following command to import all the host.
Msf > db_import "path of xml file"
The following screenshot shows what the output will look like.
To test whether the import file was correct or not, we can run specific commands on these two hosts and see how they respond. For example, in our case, we have listed all the hosts having the port 445 running on them.