Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Microsoft Emergency Path for RCE (Remote Code Execution) in Windows Malware Scanner (CVE-2017-0290)
The famous security researcher Tavis Ormandy has recently announced on Twitter that he and his researcher Natalie Silvanovich has discovered a vulnerability called “Remote Code Execution” in recent memory. According to them, the vulnerability will work against the default installation which is “Wormable” has the ability to replicate itself on an infected computer and then spread to the other PCs automatically in the network.
Microsoft has announced that their own antivirus is made of Windows 7, 8.0, 8.1 and 10 computers as well as Windows Server 2016, is vulnerable due to the latest released out-of-band update for the patch “Remote Code Execution” which is discovered by a pair of Google Project engineers over this weekend.
According to Microsoft’s released advisory, the remotely exploitable security flaw (CVE-2017-0290) exists in the MMPE (Microsoft Malware Protection Engine) which is the own antivirus engine which can be used to compromise the Windows PCs fully without any user’s interference.
Microsoft has responded to this vulnerability quickly and released a patch within the 1-2 days. The Patch is available with Windows Updates for all the affected machines like Windows 7, 8.0, 8.1 and 10.
How the Remote Code Execution Flaw Works
So, first of all – What is this Remote Code Execution Flaw in MMPE (Microsoft’s Malware Protection Engine)
This vulnerability resides in the way of the MMPE (Microsoft’s Malware Protection Engine) which scans the files and makes the attacker to craft files that can lead to the memory corruption of the targeted machine which makes the MMPE engine which evaluates the files system or network activity which looks like the JavaScript and fails to validate the JavaScripts inputs.
Since, the antivirus programs have the real-time scanning functionality which is enabled by automatic schedules and which scans the files when they are created, copied, downloaded. This exploit gets triggered as soon as the affected file is downloaded and infects the target computers.
The hackers can be exploited by the hackers in several ways by sending the emails, sending malicious files, instance messaging and by inviting to the infected sites.
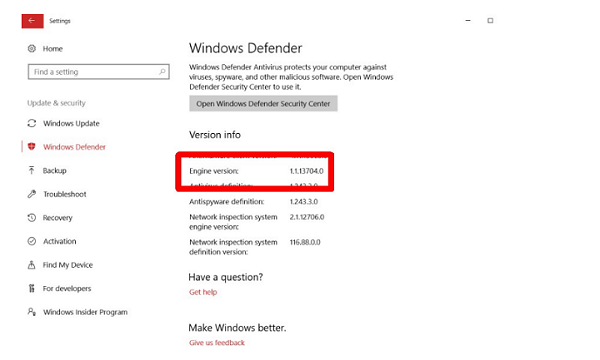
Vulnerable Versions of MMPE
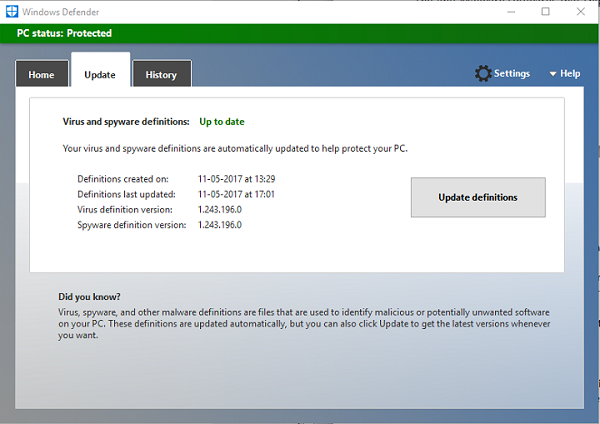
The vulnerable version of MMPE (Microsoft Malware Protection Engine) is 1.1.13701.0 and the Update patched version is 1.1.13704.0.
The list of Affected Microsoft Anti-Malware Softwares –
The Anti-Malware software’s ships with the MMPE (Microsoft’s Malware Protection Engine) which are vulnerable to this and below are the software’s affected –
- Windows Defender
- Windows Intune Endpoint Protection
- Microsoft Security Essentials
- Microsoft System Center Endpoint Protection
- Microsoft Forefront Security for SharePoint
- Microsoft Endpoint Protection
- Microsoft Forefront Endpoint Protection
How to Fix?
As a default activity, Microsoft Windows PC’s will automatically install the latest definitions and updates the Malware Engine. The PC’s will install all the emergency updates automatically within 1-2 days but we can get installation updates by clicking update definitions on the update page.