Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
What is Representing Scope Information?
Representing scope information is a concept in which the scope of each variable name is preserved in the symbol table so that we can use the same name in different blocks and different locations.
Representing Scope Information involves
- A lifetime of a variable in a particular block.
- Representing name in symbol table along with an indicator of the block in which it appears.
- Suppose we have a variable name 'a' in block A and the same variable in block B. Suppose we store 'a' in symbol table without block information. In that se, it will only keep the first instance of 'a' which it encounters, hence to overcome this problem names are stored in the form of pair (variable name, block name) so that the same name can be used in different blocks and procedures.
- Scope Representation reflects the visibility of the variable name in the source program.
Representing Scope Information in FORTRAN
- FORTRAN program consists of the main program, subroutines, and functions.
- Each name has a scope consisting of one routine, i.e., the variable scope is limited to the end of the routine.
- It can generate object code for each routine upon reaching the end of the routine and hence the names stored in the symbol table for variables belonging to that particular routine need to be eliminated.
- Hence we need to store only names that are external to routine and also of the common block in the symbol table.
Consider a hashing scheme, as shown below −
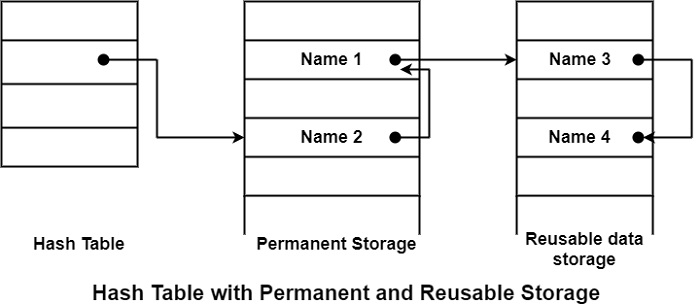 In each chain, names that are external to the current routine will appear first.
In each chain, names that are external to the current routine will appear first.
It can append new internal names to the end and new external names to the beginning.
It is clear from the above diagram hash value has selected name 2, and hence 2 iscpart of the current routine, and Name 1 is external to it, that’s why Name 1 is written in the beginning and Name 2 is appended at the end.
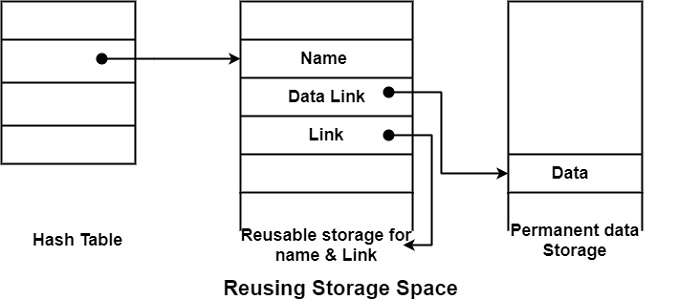
When we reach the end of the routine and generate object code for it, we reset the pointer to available storage in the reusable table but not a permanent one.
All pointer that is from the permanent table to the reusable table is set to nill, and the hash table will directly point to the reusable table.
We can also reuse the storage space used for names in the following way. We will use location in name link storage areas to represent the name, and such a location can describe different routines since that area is reused.