
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
What are the Protocol Hierarchies in Computer Networks?
A protocol is nothing but a set of rules which are followed by the communicating entities for data communication.
The protocol depends on the following −
Syntax − Syntax is the format of data which is to be sent or received.
Semantics − Semantics is the meaning of every section of bits that are transferred.
Timings − It refers to the time at which data is transferred as well as the speed at which it is transferred.
The communication between the computers in the Internet is defined by different protocols. The protocols TCP (Transmission Control Protocol) and IP (Internet Protocol) build on the basis of the communication in the Internet. The combination of the TCP and the IP protocol is called the TCP/IP protocol which represents the standard system used in most large networks.
Before discussing every protocol in hierarchy, let us illustrate the position of each protocol relative to the others in the protocol hierarchy.
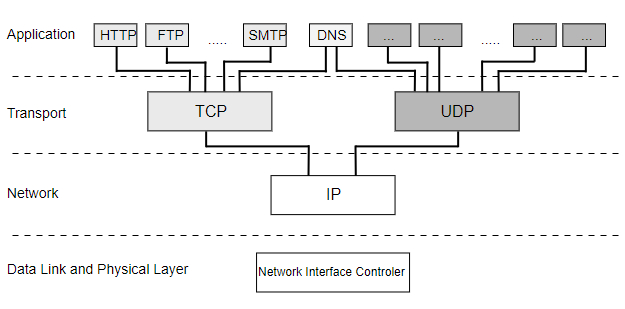
Protocol Hierarchies
A protocol is a standard which controls or enables the connection, communication, and data transfer between computing endpoints. Protocols can be implemented by hardware, software, or a combination of the two.
Generally to reduce the complexity of network software design , most networks are organized as a series of "layers" or "levels”. The different number of layers, the name of each layer, and the function of every layer differ from network to network.
The purpose of every layer is to offer a certain service to the higher layers, shielding those layers from the details of how the offered services are actually implemented.
Layer n in one machine carries on a conversation with layer n on another machine, the rules and conventions used in this conversation are collectively known as layer n "protocol".
Protocol is an agreement between the communication parties and how communication is to proceed.
Structure of Five Layer Protocol
The structure of five layer protocol is as follows −
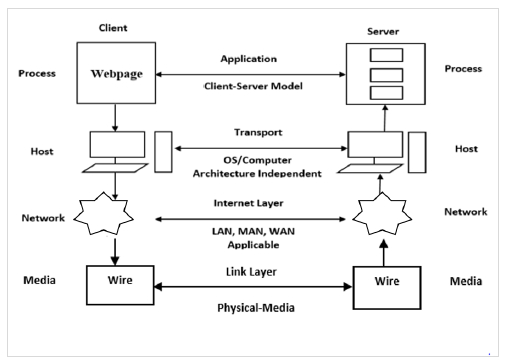
Setp 1 − Generally the entities present on different layers are called peers who are present on different machines.
Setp 2 − There is no data transferred directly from layer n on one machine to layer n on another machine.
Setp 3 − Each layer passes data and control information to the layer below it, until the lowest layer is reached.
Setp 4 − Below layer 1 there is a "physical medium" through which the actual communication occurs.
Setp 5 − In the above figure the virtual communication is shown by dotted lines and physical communication by solid line.
Setp 6 − Between each pair of adjacent layers there is an "interface", the interface defines which operations and services that the lower layer offers to the upper layer through it.
Setp 7 − A list of protocols used by system one protocol per layer is called a "protocol stack".
Now, consider how to provide communication to the top layer of five-layer network in below figure −

Here,
A massage M is produced by an application process running in layer 5.and given to layer 4 for transmission.
Layer 4 puts a " header " in front of massage M to identify the massage and passes the result to layer 3.
In many networks, there is no limit to the size of massage in layer 4-protocol, but there is nearly always a limit imposed by layer 3 protocol.
Hence, layer 3 must break up the incoming message into small units (packets) prepending layer 3 header to each packet.
In this example the message M is split into two parts, M1, and M2.
Layer 3 decides which of outgoing lines to use and passes the packet to layer 2.
Layer 2 adds a header and trailer to each packet and gives the result to layer 1 for physical transmission.
At the receiving machine, the message moves up word from layer to layer with the header being stripped off as it progresses till the message m arrives at application layer 5.

