- Wireless Security Tutorial
- Wireless Security - Home
- Wireless Security Basics
- Wireless Security - Concepts
- Wireless Security - Access Point
- Wireless Security - Network
- Wireless Security - Standards
- Wi-Fi Authentication Modes
- Wireless Security - Encryption
- Wireless Security Break an Encryption
- Wireless Threats
- Wireless - Access Control Attacks
- Wireless Security - Integrity Attacks
- Wireless - Confidentiality Attacks
- Wireless Security - DoS Attack
- Wireless Security - Layer 1 DoS
- Wireless Security - Layer 2 DoS
- Wireless Security - Layer 3 DoS
- Authentication Attacks
- Rogue Access Point Attacks
- Client Misassociation
- Misconfigured Access Point Attack
- Ad-Hoc Connection Attack
- Wireless Hacking Methodology
- Wireless Traffic Analysis(Sniffing)
- Launch Wireless Attacks
- Crack Wireless Attacks
- Wireless Security Tools
- Wireless Security RF Monitoring Tools
- Wireless Security - Bluetooth Hacking
- Wireless Security - Bluetooth Stack
- Wireless Security - Bluetooth Threats
- Wireless - Bluetooth Hacking Tools
- Wireless Security - Bluejack a Victim
- Wireless Security - Tools
- Wireless Security Pen Testing
- Wi-Fi Pen Testing
- Pentesting Unencrypted WLAN
- WEP Encrypted WLAN
- Pentesting WPA/WPA2 Encrypted
- Pentesting LEAP Encrypted WLAN
- Wireless Security Useful Resources
- Wireless Security - Quick Guide
- Wireless Security - Useful Resources
- Wireless Security - Discussion
Wireless Security - Hacking Methodology
In this chapter, you will get a little more familiar with a variety of common tools that can be used in performing specific attacks (or being a small step in more advanced attacks). Later on, in the last section, you will need all this knowledge of tools combined together, and perform more advanced and complex types of wireless attacks. It is the last section of this tutorial that will go step by step through wireless security hacking scenarios and use the tools you saw until now, and the ones you will find here.
Wi-Fi Discovery
Wi-Fi discovery is a process used to learn about WLAN's presence in the environment. WiFi discovery process is not against any law, since you are not acting offensively at any point, you are simply, passively listening to the Wi-Fi frequency bands, using your wireless client.
In order to discover what type of WLAN networks are present, you need to use specific tools that uses wireless hardware and listens on either a 2.4GHz or a 5GHz band. Some of them are built-in to the operating system (they are most often very ineffective for detailed WLAN analysis), and other ones are simple tools, which you can find on the internet. There are hundreds or thousands of tools out there in the market.
I will present to you 2 of them, that I really enjoyed due to its simplicity. What you will discover, while going through these chapters (or you already know it from your experience), the tools delivered for Windows OS have better graphics and some fancy graphical features, opposite to what Linux-based tools provide. But I can promise you, the ones based on Linux provide exactly the same information (just in more text-like format). On the other hand, it is a bit easier to write scripts, that takes outputs of one tools as the input to other ones.
For Windows users, you should have a look at the Xirrus Wi-Fi Inspector (it can be used for free). This is a simple tool that identifies WLANs present in the nearby vicinity. Another tool that performs the same functions in the Windows environment is NetStumbler.
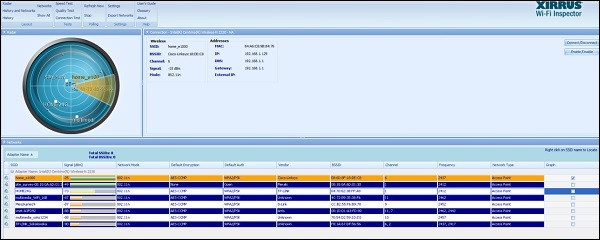
The information which you can extract from the table at the bottom of the above screenshot provides everything you may look for, like SSID name, received signal strength, 802.11 standard used, encryption and authentication set on WLAN, BSSID (MAC address of the AP, in case you would like create a fake AP with the same MAC address) and what channel it operates on. This is a lot of! You can also see, very fancy graphical "radar" showing, how far particular networks are, from your current location - the same information may be read from Signal (dBm) field.
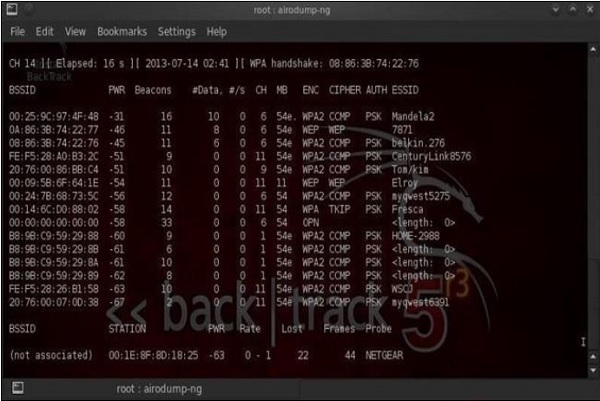
On the other side, when using Linux (I use Kali distribution for penetration testers - you should try as well), the equivalent of that would be a tool called airodump-ng. The set of information, that airodump-ng output to the user is shown in the following screenshot. Also, we have another well-known tool called as Kismet.
Wardriving
Wardriving is the process of finding a Wireless Network (wireless network discovery) by a person in a car using their personal laptop, smartphone or other wireless client tools. Basically, the intention is to find some free-access wireless network, that malicious user can use without any legal obligations. Examples might be some market, that offer free Wi-Fi, without registration or some hotel that you can just register with fake data.
The method of finding those WLAN's are exactly the same as described above in this wireless discovery section.
GPS Mapping
There is a number of satellites that orbit the globe, each of them sending a low-power radio signal towards the piece of earth it covers. The GPS device that you use, it may be for example a smartphone with google maps application started, receives that signal from multiple satellites at the same time. The device itself combines those signals together and calculate current geographical location on earth.
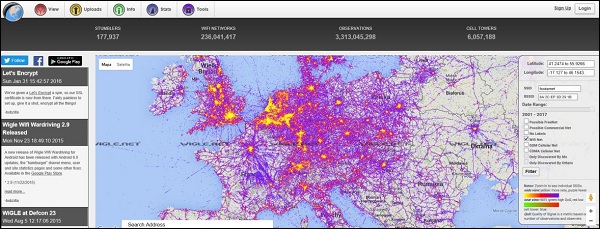
The idea of GPS mapping is to map a wireless network that the user encounters on the global map of wireless network in reference to its geographical location. One may use the already mentioned Kismet tool to map its wireless network to the geographical location, and then put its coordinates on the google earth map.
There is website on the internet http://wigle.net that you can use to see how many WLAN's are GPS mapped. You can use this website to map GSM cellular network as well.