
- Wireless Security Tutorial
- Wireless Security - Home
- Wireless Security Basics
- Wireless Security - Concepts
- Wireless Security - Access Point
- Wireless Security - Network
- Wireless Security - Standards
- Wi-Fi Authentication Modes
- Wireless Security - Encryption
- Wireless Security Break an Encryption
- Wireless Threats
- Wireless - Access Control Attacks
- Wireless Security - Integrity Attacks
- Wireless - Confidentiality Attacks
- Wireless Security - DoS Attack
- Wireless Security - Layer 1 DoS
- Wireless Security - Layer 2 DoS
- Wireless Security - Layer 3 DoS
- Authentication Attacks
- Rogue Access Point Attacks
- Client Misassociation
- Misconfigured Access Point Attack
- Ad-Hoc Connection Attack
- Wireless Hacking Methodology
- Wireless Traffic Analysis(Sniffing)
- Launch Wireless Attacks
- Crack Wireless Attacks
- Wireless Security Tools
- Wireless Security RF Monitoring Tools
- Wireless Security - Bluetooth Hacking
- Wireless Security - Bluetooth Stack
- Wireless Security - Bluetooth Threats
- Wireless - Bluetooth Hacking Tools
- Wireless Security - Bluejack a Victim
- Wireless Security - Tools
- Wireless Security Pen Testing
- Wi-Fi Pen Testing
- Pentesting Unencrypted WLAN
- WEP Encrypted WLAN
- Pentesting WPA/WPA2 Encrypted
- Pentesting LEAP Encrypted WLAN
- Wireless Security Useful Resources
- Wireless Security - Quick Guide
- Wireless Security - Useful Resources
- Wireless Security - Discussion
Rogue Access Point Attacks
When we think about corporate networks, the corporate WLAN is an authorized and secured wireless portal to the network resources. A rogue access device (AP) is any WLAN radio that is connected to the corporate network (most often to some network switch) without the authorization.
Most of the rogue access points that are installed by employees (malicious users or by mistake) are actually not the same AP's that the IT department in the organization is using, but some Small-office home-office (SOHO) wireless routers - the same ones, that you probably have at home. In the situation when they are misconfigured or configured without any security - it opens a next attack surface for having easy access to a very secure network).
With the current evolution of the IT industry, rogue access point might be very well hidden and extremely hard to find. Would you be able to easily spot a Raspberry Pi connected to your network switch, if it would be placed at the back of the rack hidden in between hundreds of network cables? I can definitely say, you would NOT spot it at all!
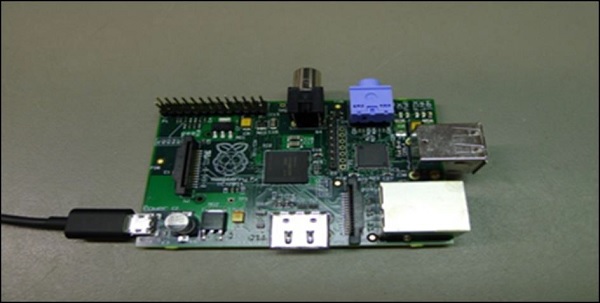
If the network resources are exposed by a rogue access point, the following risks may be identified −
Data Theft − Corporate data may be compromised.
Data Destruction − Databases may be erased.
Loss of Services − Network services can be disabled.
Malicious Data Insertion − An attacker may use a portal to upload viruses, key loggers or pornography.
3rd Party Attacks − A company's wired network may be used as a launching pad for 3rd party attacks against other networks across the internet.