
- SAP Security Tutorial
- SAP Security - Home
- SAP Security - Overview
- User Authentication & Management
- Network Communication Security
- Protecting Standard Users
- Un-authorizing Logons Protections
- System Authorization Concept
- SAP Security - Unix Platform
- SAP Security - Windows Platform
- SAP Security - Databases
- User Authentication & Single SignOn
- SAP Security - Logon Tickets
- SAP Security Useful Resources
- SAP Security - Quick Guide
- SAP Security - Useful Resources
- SAP Security - Discussion
SAP Security - Network Communication
Secure Network Communication (SNC) can also be used to login to an application server using secure authentication method. You can use SNC for user authentication via SAP GUI for windows or by using an RFC connection.
The SNC uses an external security product to perform the authentication between the communication partners. You can use security measures like public key infrastructure PKI, and procedures to generate and distribute key pairs.
You should define network topology that can eliminate threats and prevent network attacks. When users cannot login to the application or database layer, attackers cannot get access to the SAP system or the database system to access critical information.
A well-defined network topology doesn’t allow intruders to connect to the company’s LAN and hence no access to security loop holes on the network services or on the SAP system.
Network Topology in a SAP System
Your physical network architecture completely depends on the size of your SAP System. A SAP System is commonly implemented with a client-server architecture and each system is commonly divided into the following three layers −
- Database Layer
- Application Layer
- Presentation Layer
When your SAP system is small, it may not have a separate application and database server. However, in a large system, many application servers communicate with a database server and several frontends. This defines the network topology of a system from simple to complex and you should consider different scenarios when organizing your network topology.
In a large-scale organization, it is recommended that you install your application and database server on different machines and place in a separate LAN from the frontend system.
In the following image, you can see the preferred Network topology of a SAP system −
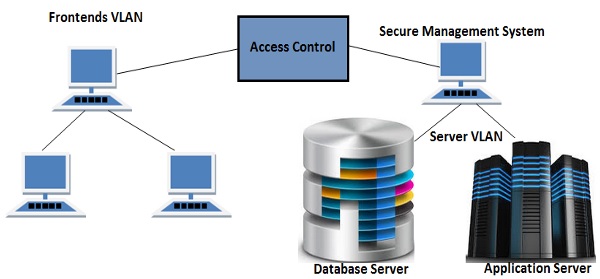
When you place your database and application server in separate VLAN from frontends VLAN, it allows you to improve the access control system and hence increases the security of your SAP system. Frontend systems are in different VLAN, so it is not easy to get into the Server VLAN and hence bypass the security of your SAP system.
SAP Network Services
In your SAP system, there are various services that are enabled however only few are required to run SAP system. In a SAP system, the Landscape, Database and Application Servers are the most common target of network attacks. Many network services are running in your landscape that allows the access to these servers and these services should be carefully monitored.
In your Window/UNIX machines, these services are maintained in /etc/services. You can open this file in Windows machine by going to the following path −
system32/drivers/etc/services
You can open this file in a Notepad and review all the activated services in your server −
It is recommended that you disable all the unrequired services on landscape servers. Sometimes these services contain a few errors which can be used by intruders to gain unauthorized access. When you disable these services, you reduce the chances of an attack on your network.
For high level of security, it is also recommended to use static password files in your SAP environment.
Private Keys
SNC uses an external security product to perform the authentication between the communication partners. You can use security measures like Public Key Infrastructure (PKI) and other procedures to generate and distribute key pairs and to ensure that private keys for users are properly secured.
There are different ways of securing the private keys for a network authorization −
- Hardware Solution
- Software Solution
Let us now discuss them in detail.
Hardware Solution
You can protect private keys for users using hardware solution where you issue smart card to individual users. All the keys are stored in a smart card and the user should authenticate to their smart cards via biometrics by using finger prints or using a PIN password.
These smart cards should be protected from theft or loss by each individual user and users can use the card to encrypt the documents.
Users are not allowed to share the smart cards or give them to other users.
Software Solution
It is also possible to use software solution to store private keys for individual users. Software solution is less expensive solution as compared to hardware solution, but they are also less secure.

When users store private keys in files and user details, there is a need to secure those files for unauthorized access.