
- Cryptography Tutorial
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Symmetric Algorithms
- Data Encryption Standard
- Triple DES
- Advanced Encryption Standard
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Cryptography Useful Resources
- Cryptography - Quick Guide
- Cryptography - Discussion
Cryptosystem - Rainbow table Attack
What is the Rainbow table Attack?
Rainbow table attack is a technique used to decipher passwords that uses a table known as a "rainbow table". Passwords are not kept in simple text, they are encrypted into hashes instead. When a user attempts to log in by keying in a password, it's transformed into hashes. they are then linked to the server's table of stored hashes to verify a match. A match signifies that the user's identity has been confirmed, granting them access to the software.
the rainbow table itself displays a pre-calculated table of password hash values in whatever plain characters are used in the authentication process. Hackers can easily crack every password using the rainbow table if they have access to the password hash list.
A tool called "salting" has drastically decreased the rainbow table attacks. Salt is a modern way of preventing rainbow table attacks. this needs adding a new random value to each hash password to create a unique hash value. Most modern password authentication systems contain salts, to greatly reduce the number of successful rainbow table attacks.
Most programmers use salting, but there are still some who do not and this makes them more vulnerable to rainbow tables.
Here is a simple diagram of how the rainbow table attack works −
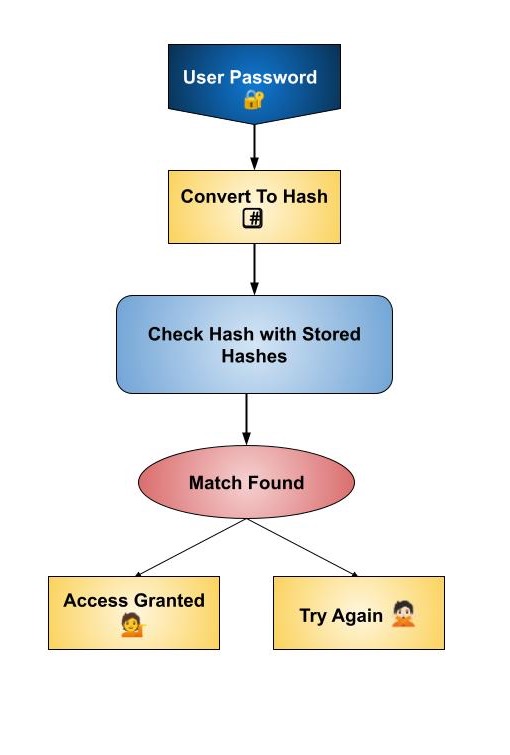
Explanation
the user enters a password.
the password is converted to a hash (a special code).
the hash is compared with the hashes stored on the server.
If a match is found, access is granted. Otherwise, the user can try again.
Rainbow table attacks occur when hackers gain access to stored hashes and use a pre-computed table to quickly find the original passwords associated with those hashes.
How actually Rainbow table attack work?
to attack the rainbow table, hackers must first gain access to the leaking hash. Sometimes the password database itself is not well secured, or perhaps they have access to Active Directory. Users who need to gain access to the password database gain access through phishing techniques. In all these ways, there are already millions and millions of leaked password hashes on the Dark Web available to hackers.
Once the password hash is obtained, the rainbow table is used to help decrypt the password hash. As long as there is no "salt" in the password hash, (defined above), encrypted passwords can be translated into plain text.
the whole rainbow table attack process has four steps −
Creation − The rainbow table generates a hash list by first taking a list of potential passwords and applying a hash function to each one. A rainbow table is used to store the hashes that are produced along with the plaintext passwords that correspond with them.
Finding − A hacker can use the rainbow table to find passwords in plaintext that match a collection of hashes they have. In order to find a match to the target hash, the hashes in the rainbow table are verified backwards, beginning with the final hash in each chain.
Cracking − When the matching hash value is found, it indicates that the target hash's original password is the matching plaintext password. Now a hacker can use the authentication process to gain access to someone else's account.
Reduction − the hashes in the rainbow table are reprocessed by a reduction function to generate a new hash set. the reduction function maps each hash to a new value, and the new value is used as the starting point for the next step. this step is repeated several times to create a hash chain.
Rainbow table Attack Examples
Below we list two real world examples of how rainbow table attacks can happen −
the attacker discovers a web application with outdated password hashing techniques and very poor security. By obtaining the password hashes, the attacker can utilise the rainbow table to decrypt each user's password for the application.
the hacker is able to gain access to the password hash by searching for vulnerabilities in the company's Active Directory. A rainbow table attack is used to decrypt the hashes into plain text passwords after you get a list of them.
Protect Against a Rainbow table Attack!
Defending yourself against rainbow table attacks is fairly straightforward if you follow these guidelines −
Eliminate passwords − the only way to ensure that password-based attacks are prevented is to resolve passwords. there is no way to do a rainbow gate attack without having a password hash list to steal. Learn more about passwordless authentication today and keep your important applications running smoothly.
Using salt − Hash passwords should never be stored without salting. this makes it more difficult to decrypt the password. However, it is recommended removing the alphanumeric term altogether.
Use biometrics − It is very difficult, if not impossible, for an attacker to conduct a rainbow table attack successfully when using a biometric authentication mechanism against a biometric password.
Monitor your servers − Most modern server security software monitors attempts to access sensitive information and can work to minimize and catch attackers before they discover the password database.
Avoid using outdated hashing algorithms − Hackers target applications and servers that use outdated password hashing algorithms MD5 and SHA1. If your application uses an outdated algorithm, the chances of rainbow table attacks may increases dramatically.
Rainbow table Attack vs. Dictionary Attack
Both rainbow table attacks and dictionary attacks are password cracking techniques used by hackers to obtain passwords.
An attacker uses a pre-computed hash table in a rainbow table attack to determine the hash password's plaintext version.. Unlike a dictionary attack, where an attacker tries each word in a dictionary until a match is found, a rainbow table attack allows an attacker to quickly find a plaintext word that contains a preceding table that has been calculated. But they take a lot of time to create and use a lot of space.
In a dictionary attack, the hacker uses a pre-compiled list of common passwords (popular words and symbols), a dictionary, to compare against a hash password and as a match is found to indicate that the hash password is cracked. Dictionary attacks are successful because many users create passwords that are straightforward and simple to figure out. This attack depends on the speed of the computer and uses several possible passwords.
Summary
A rainbow table attack is a way for hackers to crack hash passwords stored in databases using pre-calculated tables. However, the effectiveness of such attacks is reduced by the use of salt, which adds random values to hash passwords. to protect against rainbow desktop attacks, organizations should eliminate password-based authentication, adopting secure methods such as password-less authentication or biometrics, with password hashing with salt use, monitor servers for malicious activity, and classic techniques such as MD5 and SHA1. Hashing algorithms and evasion should be considered these features help reduce the risk of becoming a victim of a rainbow desktop attack and increase overall cybersecurity.
To Continue Learning Please Login