
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Windows UAC protection Bypass
UAC (User account control ) is a windows IS security that enables a user to perform limited number of admin operations. Overall, it prevents normal users from performing specific actions that could pose a security risk to the system by requiring users to have admin-level permission. For security reasons enabling UAC to detect application installations and prompt for elevation to prevent regular user accounts from installing unauthorized software on clients is a best practice within Windows OS environments.
In this tutorial, we shall investigate how to elevate the admin-level right from the end of a normal logged-in user by bypassing UAC protection mechanism.
So, First type netplwiz.exe in the Windows Run prompt, select the Advanced tab as following;
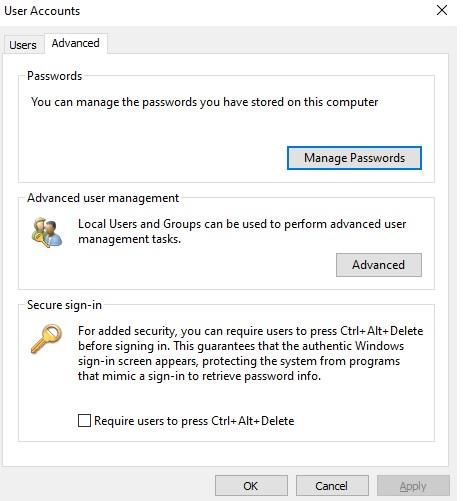
Advance option from the advance user management section
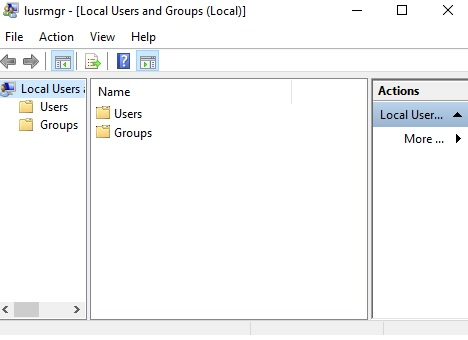
Then, select the “help topics” from the Help menu in the local users and group as following;
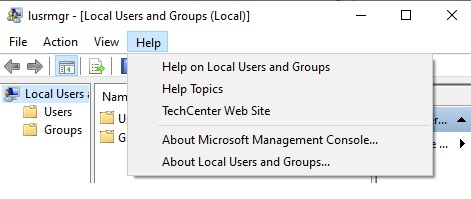
After that, Right-click in the dialog box and select view source, and then select the file-open menu and navigate to the path C\Windows\System32 from the Notepad file.
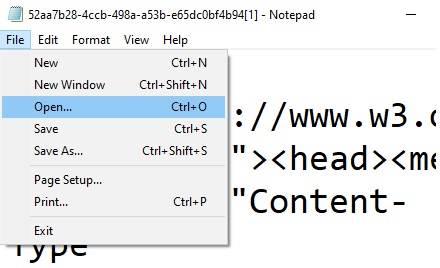
Now, change the selection to all files and search cmd.exe. Now right-click on it and run it as administrator.
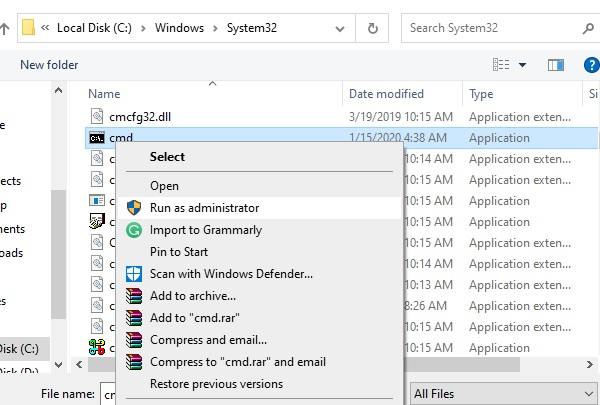
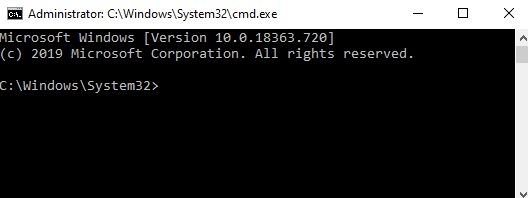
Voila! We have got the windows DOS terminal with admin rights to perform privilege escalation as following.
Now view the currently logged in user name with Admin right by the command of Net User. Thereafter that reset the admin user password by the net user * command as following;
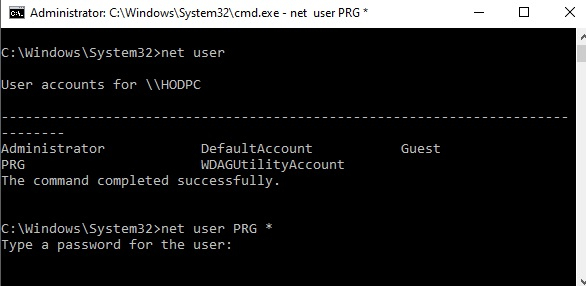
Finally, we have bypassed the windows UAC restriction as well as reset the administrator password.

