
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Protection ring
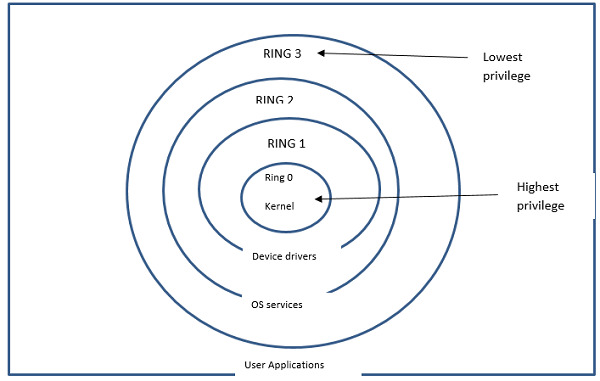
The operating system functions on different layers and each of them has its privileges. These privileges are mentioned using a protection ring that is used for sharing resources and the hardware systems, that manage the resources stored in the computer system like CPU processing time and memory access time. Protection rings are arranged in a hierarchical order from most trusted to least trusted privilege. The central ring at the kernel level can access all resources and has the highest privilege whereas the subsequent layers have a lesser level of access permissions. This mechanism is hardware imposed by the architecture of the CPU at different access modes. Processor with x86 uses four levels of rings implemented utilizing ring 0 to ring 3, where ring 0 has the highest privilege.
Importance of Protection Ring
This method of providing a layered protection model offers advantages that are listed below ?
-
It provides computer security when a process needs a set of instructions with several CPU resources then the process initiates a request to the Operating system. After receiving the request, the Operating system may decide whether to grant access privileges or not. This activity prevents the system from malicious attacks or behavior from other processes or external sources.
-
System crashes can be reduced by providing fault tolerance to the applications that have direct access to the kernel space with ring 0 protection.
Levels in Protection Ring
As said earlier, the x86 instruction set uses four privilege levels from ring 0 to ring 3. Ring 0 has access to the kernel part which is called the core of the operating system. The process that runs in kernel mode can access all resources of the system. It can access the physical functions of hardware in CPU and motherboard chipsets. Computer architects have limited the interactions to this layer as it contains all the functions of system processes.
-
Ring 1 and 2 have distinct privileges supported than Ring 3. Ring 1 is used to interact with hardware that would execute commands for streaming of video using a camera to the display interface. Commands that are needed for storing, loading, and saving are done in Ring 2.
-
Ring 3 has the access right of the user's application and it offers the least privilege. When any resources are needed for the process then, it should request to ring 0 which is near to kernel for accessing the needed application, and all the information's passed to the lower levels.
Protection Ring for x86 processor
It is not necessary for the system needs to use all four levels of protection rings. Windows, Mac OS, Android, and UNIX operating systems use a paging mechanism to define the privilege mode as a supervisor or user mode. Ring 0 and 3 are the needed ones and other levels of Ring 1 and 2 are optional.
Interaction in Privilege Rings
Before knowing how the levels of the ring interact with the processes, one should be familiar with two types of modes.
-
Supervisor mode can be modified by the code or process running at the system software level. System-level process or threads has this supervisor flag set whereas other user-level applications cannot do it. This mode provides instructions to execute the processes and it can modify the registers functions or disabling interrupt signals. Operating system with microkernel usually runs in supervisor mode.
-
Hypervisor mode is supported by a recent CPU with x86 configuration to provide control to Hardware space in Ring 0. Intel VT-x and AMD-v create a new Ring 1 which is used by the guest operating system and can execute Ring 0 functions without interrupting guest users or host users.
Ring 0 functions in the supervisor mode that does not require any input interaction from the user. If any interaction made to this mode could result in security threats and a high risk of system errors. Due to these security reasons, this level is not accessible to all the host users. Linux and Windows operating system uses Ring 0 and Ring 3 for kernel and applications whereas modern OS systems with new CPU configurations used the other two ring levels also.
Protection of rings can be combined with any of the processer modes either with a supervisor or kernel or hypervisor. Hardware-supported systems use both either one or both layers of protection. Earlier versions of Windows 95 and Windows 98 provide fewer shielding factors between the privilege level of rings and this in turn leads to more security errors.
Conclusion
An operating system that uses protection rings to restrict access and operations by enabling different hierarchy levels of security improves fault tolerance issues. These extra layers of rings to each process can reduce the performance of the system and maintaining these privilege levels is quite a tedious task. Recent advancements in the processor built in various operating systems use the combination of protection rings to support extra security and improve the overall performance of the system when used in the network environment.

