
- Security Testing - Home
- Security Testing - Overview
- Security Testing - Process
- Security Testing - Malicious Software
- HTTP Protocol Basics
- HTTPS Protocol Basics
- Encoding and Decoding
- Security Testing - Cryptography
- Security Testing - Same Origin Policy
- Security Testing - Cookies
- Hacking Web Applications
- Security Testing - Injection
- Testing Broken Authentication
- Testing Cross Site Scripting
- Insecure Direct Object Reference
- Testing Security Misconfiguration
- Testing Sensitive Data Exposure
- Missing Function Level Access Control
- Cross Site Request Forgery
- Components with Vulnerabilities
- Unvalidated Redirects and Forwards
- Security Testing - Ajax Security
- Testing Security - Web Service
- Security Testing - Buffer Overflows
- Security Testing - Denial of Service
- Testing Malicious File Execution
- Security Testing - Automation Tools
Security Testing - Process
Security testing can be seen as a controlled attack on the system, which uncovers security flaws in a realistic way. Its goal is to evaluate the current status of an IT system. It is also known as penetration test or more popularly as ethical hacking.
Penetration test is done in phases and here in this chapter, we will discuss the complete process. Proper documentation should be done in each phase so that all the steps necessary to reproduce the attack are available readily. The documentation also serves as the basis for the detailed report customers receive at the end of a penetration test.
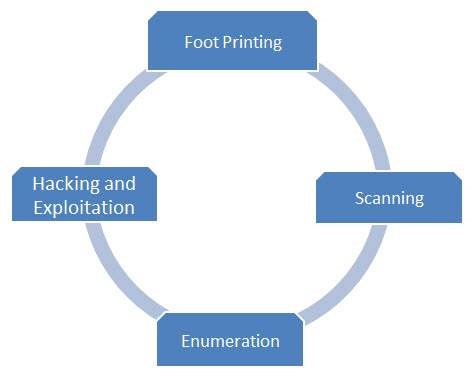
Penetration Test Workflow
Penetration test includes four major phases −
These four steps are re-iterated multiple times which goes hand in hand with the normal SDLC.
Advertisements