
- Security Testing - Home
- Security Testing - Overview
- Security Testing - Process
- Security Testing - Malicious Software
- HTTP Protocol Basics
- HTTPS Protocol Basics
- Encoding and Decoding
- Security Testing - Cryptography
- Security Testing - Same Origin Policy
- Security Testing - Cookies
- Hacking Web Applications
- Security Testing - Injection
- Testing Broken Authentication
- Testing Cross Site Scripting
- Insecure Direct Object Reference
- Testing Security Misconfiguration
- Testing Sensitive Data Exposure
- Missing Function Level Access Control
- Cross Site Request Forgery
- Components with Vulnerabilities
- Unvalidated Redirects and Forwards
- Security Testing - Ajax Security
- Testing Security - Web Service
- Security Testing - Buffer Overflows
- Security Testing - Denial of Service
- Testing Malicious File Execution
- Security Testing - Automation Tools
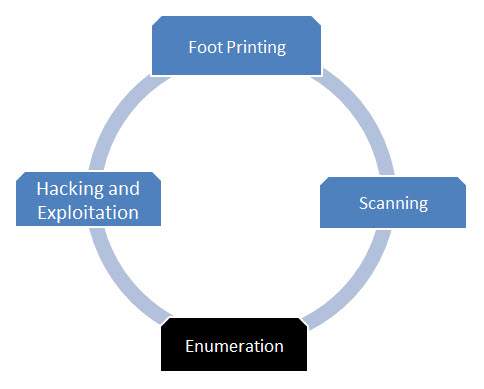
Security Testing - Enumeration
Enumeration
Enumeration is the next step after scanning. The goal of enumeration is to get a complete picture of the target. In this phase, a penetration tester tries to identify valid user accounts or poorly-protected shared resources using active connections to systems.
Techniques Used in Enumeration
Following are the common set of procedures used in Enumeration −
- Identifying vulnerable user accounts
- Obtaining Active Directory information
- Using snmputil for Simple Network Management Protocol enumeration
- Employing Windows DNS queries
- Establishing null sessions and connections
Flow Diagram
Advertisements