
- Security Testing - Home
- Security Testing - Overview
- Security Testing - Process
- Security Testing - Malicious Software
- HTTP Protocol Basics
- HTTPS Protocol Basics
- Encoding and Decoding
- Security Testing - Cryptography
- Security Testing - Same Origin Policy
- Security Testing - Cookies
- Hacking Web Applications
- Security Testing - Injection
- Testing Broken Authentication
- Testing Cross Site Scripting
- Insecure Direct Object Reference
- Testing Security Misconfiguration
- Testing Sensitive Data Exposure
- Missing Function Level Access Control
- Cross Site Request Forgery
- Components with Vulnerabilities
- Unvalidated Redirects and Forwards
- Security Testing - Ajax Security
- Testing Security - Web Service
- Security Testing - Buffer Overflows
- Security Testing - Denial of Service
- Testing Malicious File Execution
- Security Testing - Automation Tools
Security Testing - Buffer Overflows
A buffer overflow arises when a program tries to store more data in a temporary data storage area (buffer) than it was intended to hold. Since buffers are created to contain a finite amount of data, the extra information can overflow into adjacent buffers, thus corrupting the valid data held in them.
Example
Here is a classic examples of buffer overflow. It demonstrates a simple buffer overflow that is caused by the first scenario in which relies on external data to control its behavior. There is no way to limit the amount of data that user has entered and the behavior of the program depends on the how many characters the user has put inside.
... char bufr[BUFSIZE]; gets(bufr); ...
Hands ON
Step 1 − We need to login with name and room number to get the internet access. Here is the scenario snapshot.
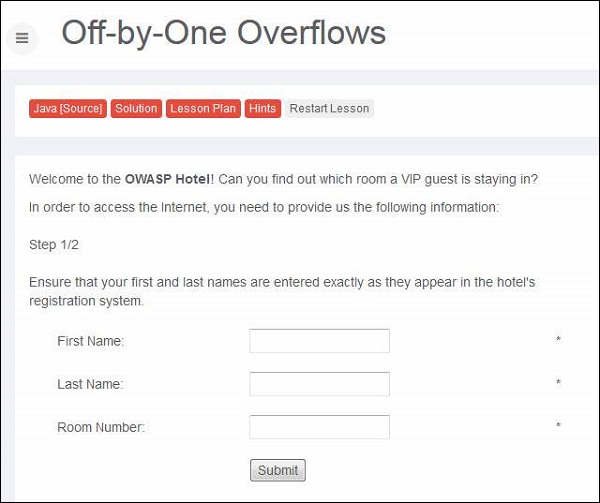
Step 2 − We will also enable "Unhide hidden form fields" in Burp Suite as shown below −
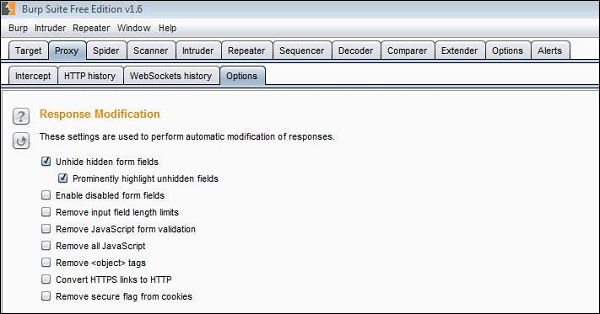
Step 3 − Now we send an input in name and room number field. We also try and inject a pretty big number in the room number field.
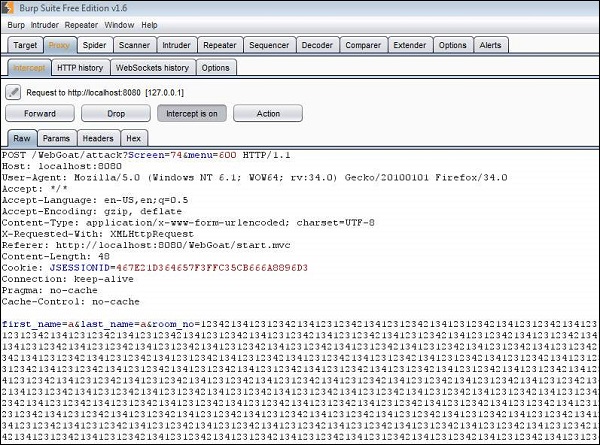
Step 4 − The hidden fields are displayed as shown below. We click accept terms.
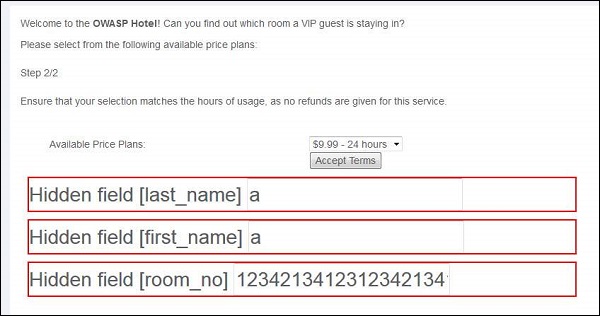
Step 5 − The attack is successful such that as a result of buffer overflow, it started reading the adjacent memory locations and displayed to the user as shown below.
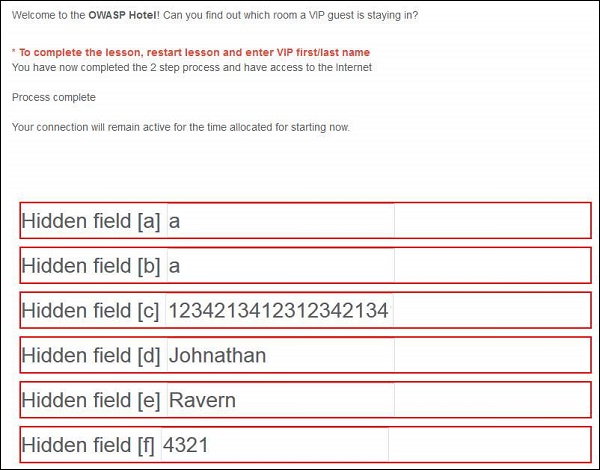
Step 6 − Now let us login using the data displayed. After logging, the following message is displayed −
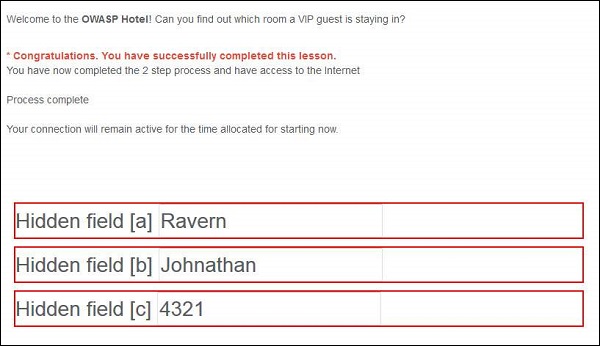
Preventive Mechanisms
- Code Reviewing
- Developer training
- Compiler tools
- Developing Safe functions
- Periodical Scanning