
- Security Testing - Home
- Security Testing - Overview
- Security Testing - Process
- Security Testing - Malicious Software
- HTTP Protocol Basics
- HTTPS Protocol Basics
- Encoding and Decoding
- Security Testing - Cryptography
- Security Testing - Same Origin Policy
- Security Testing - Cookies
- Hacking Web Applications
- Security Testing - Injection
- Testing Broken Authentication
- Testing Cross Site Scripting
- Insecure Direct Object Reference
- Testing Security Misconfiguration
- Testing Sensitive Data Exposure
- Missing Function Level Access Control
- Cross Site Request Forgery
- Components with Vulnerabilities
- Unvalidated Redirects and Forwards
- Security Testing - Ajax Security
- Testing Security - Web Service
- Security Testing - Buffer Overflows
- Security Testing - Denial of Service
- Testing Malicious File Execution
- Security Testing - Automation Tools
AJAX Security
Asynchronous Javascript and XML (AJAX) is one of the latest techniques used to develope web application inorder to give a rich user experience. Since it is a new technology, there are many security issues that are yet to be completed established and below are the few security issues in AJAX.
The attack surface is more as there are more inputs to be secured.
It also exposes the internal functions of the applications.
Failure to protect authentication information and sessions.
There is a very narrow line between client-side and server-side, hence there are possibilities of committing security mistakes.
Example
Here is an example for AJAX Security −
In 2006, a worm infected yahoo mail service using XSS and AJAX that took advantage of a vulnerability in Yahoo Mail's onload event handling. When an infected email was opened, the worm executed its JavaScript, sending a copy to all the Yahoo contacts of the infected user.
Hands ON
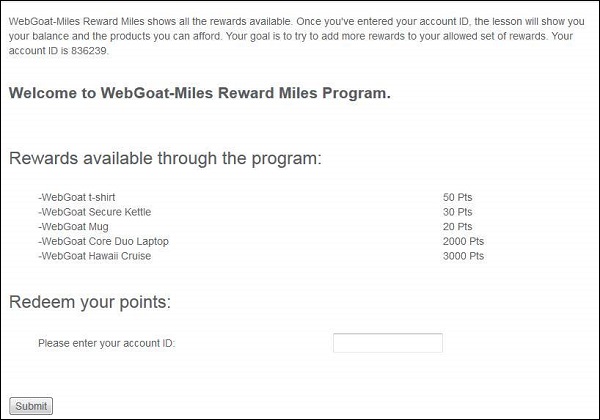
Step 1 − We need to try to add more rewards to your allowed set of reward using XML injection. Below is the snapshot of the scenario.
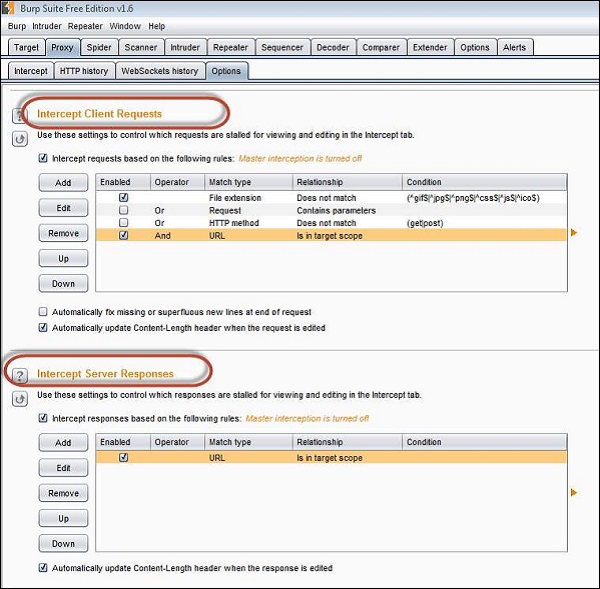
Step 2 − Make sure that we intercept both request and response using Burp Suite. Settings of the same as shown below.
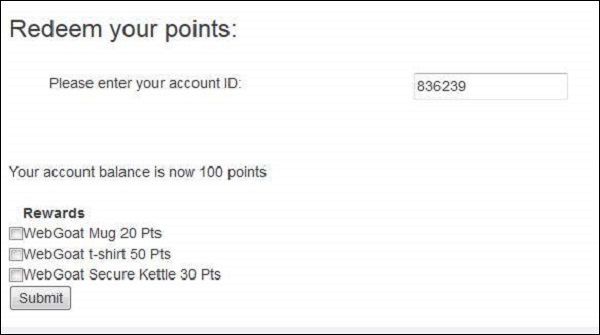
Step 3 − Enter the account number as given in the scenario. We will be able to get a list of all rewards that we are eligible for. We are eligible for 3 rewards out of 5.
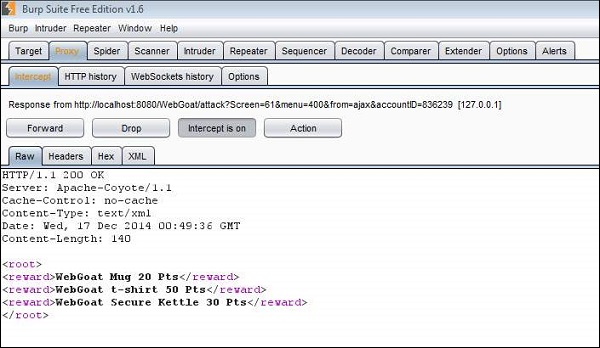
Step 4 − Now let us click 'Submit' and see what we get in the response XML. As shown below the three rewards that are we are eligible are passed to us as XML.
Step 5 − Now let us edit those XMLs and add the other two rewards as well.
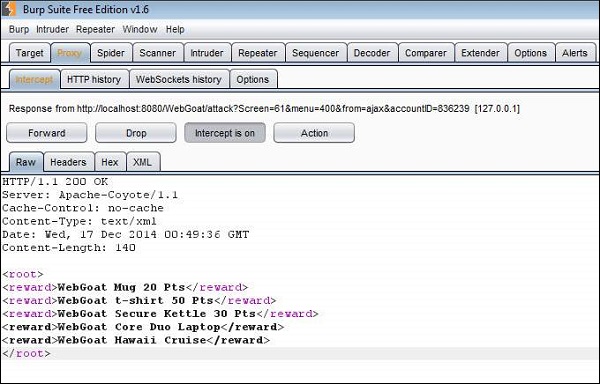
Step 6 − Now all the rewards would be displayed to the user for them to select. Select the ones that we added and click 'Submit'.
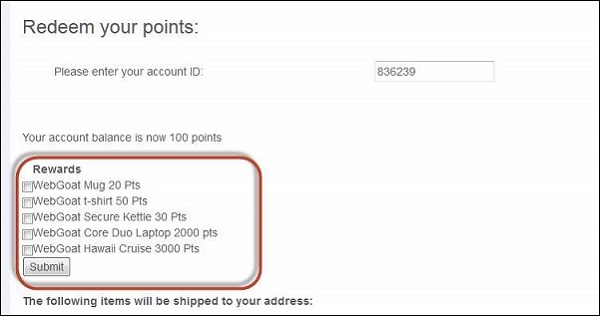
Step 7 − The following message appears saying, "* Congratulations. You have successfully completed this lesson."
Preventive Mechanisms
Client side −
- Use .innerText instead of .innerHtml.
- Do not use eval.
- Do not rely on client logic for security.
- Avoid writing serialization code.
- Avoid building XML dynamically.
- Never transmit secrets to the client.
- Do not perform encryption in client side code.
- Do not perform security impacting logic on client side.
Server side −
- Use CSRF protection.
- Avoid writing serialization code.
- Services can be called by users directly.
- Avoid building XML by hand, use the framework.
- Avoid building JSON by hand, use an existing framework.